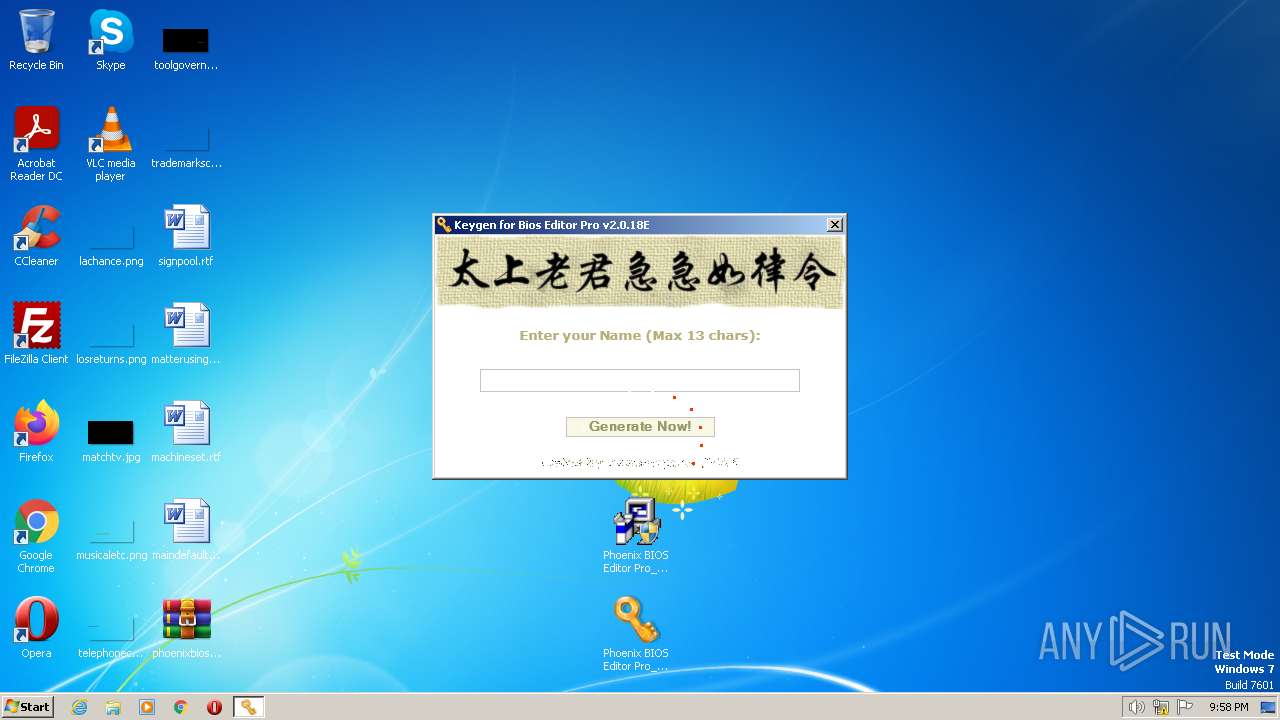
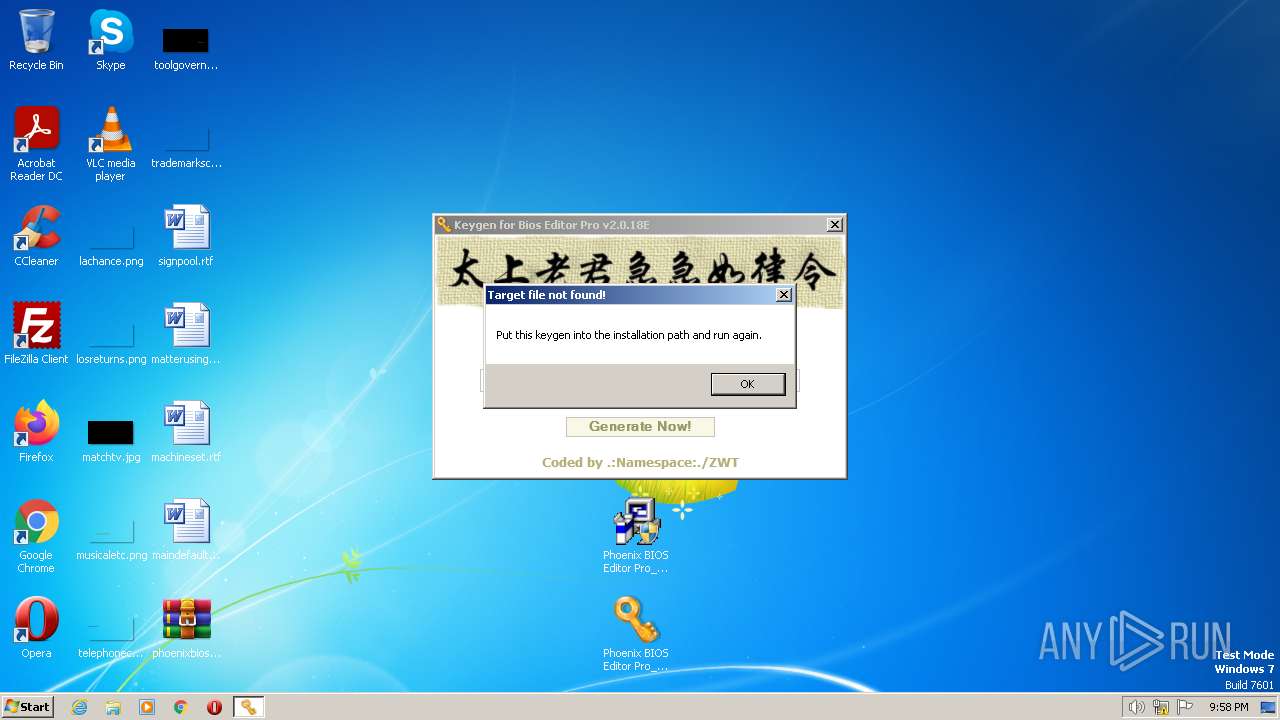
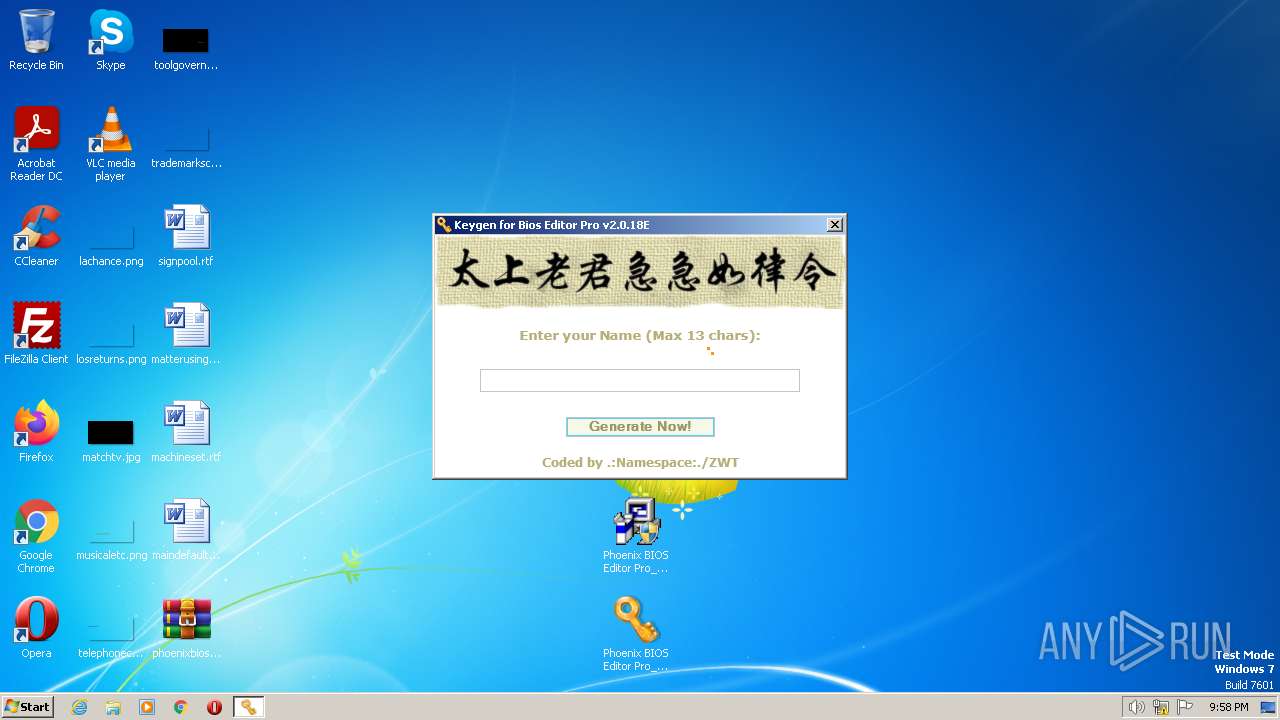
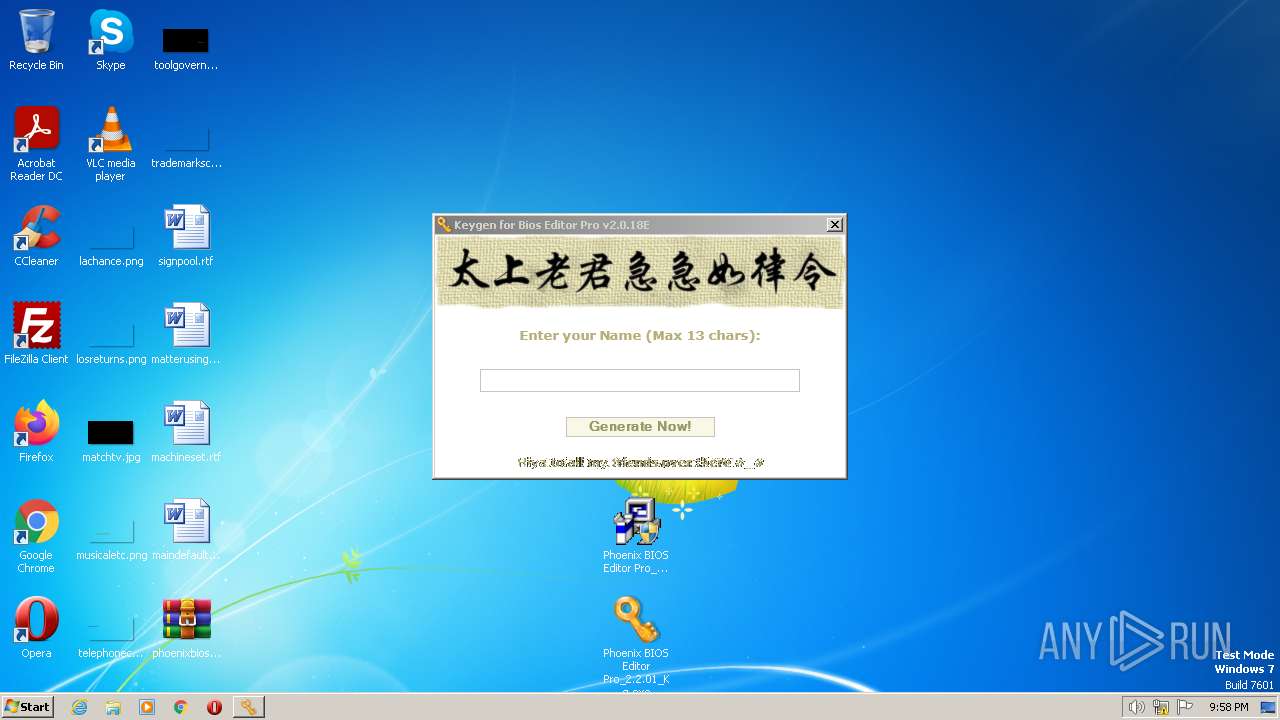
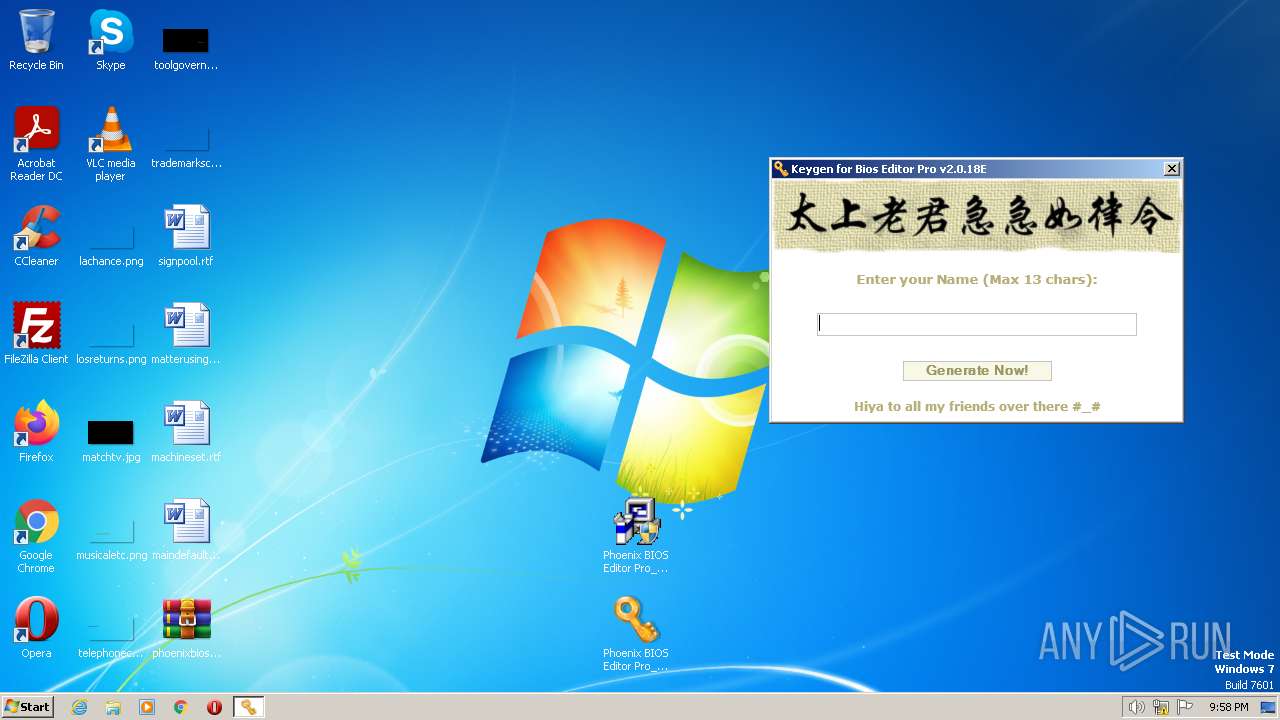
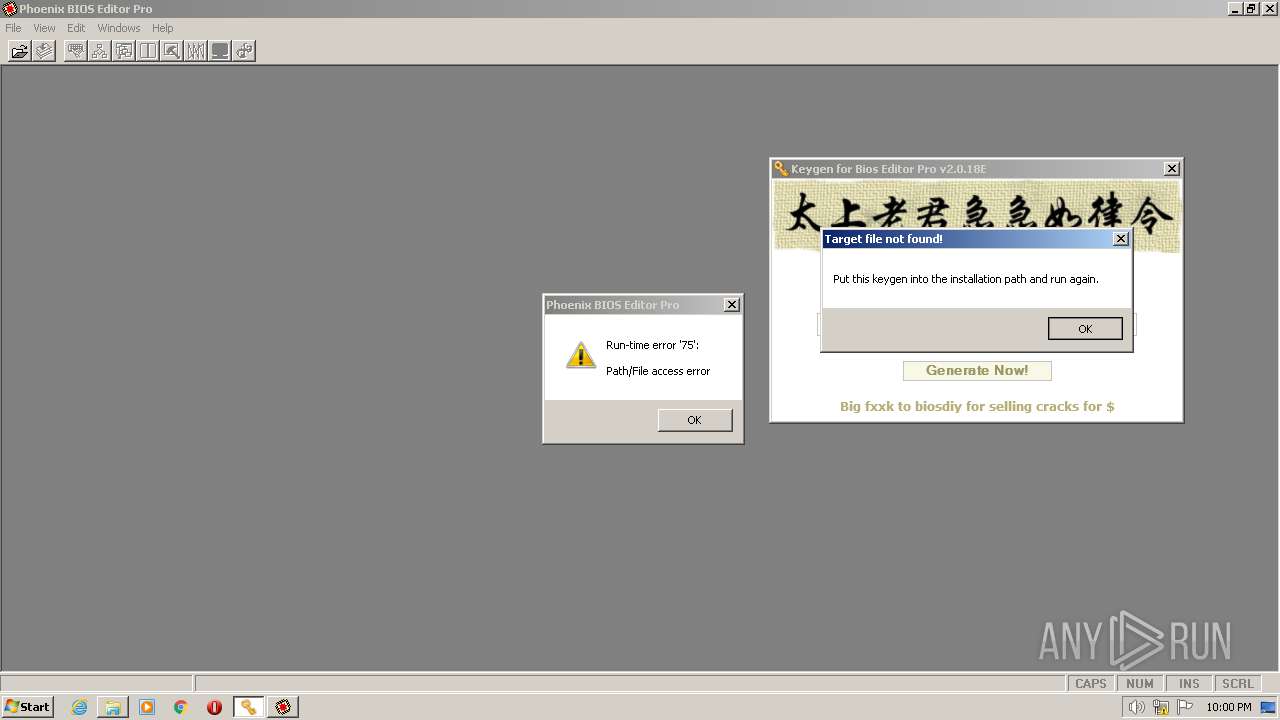
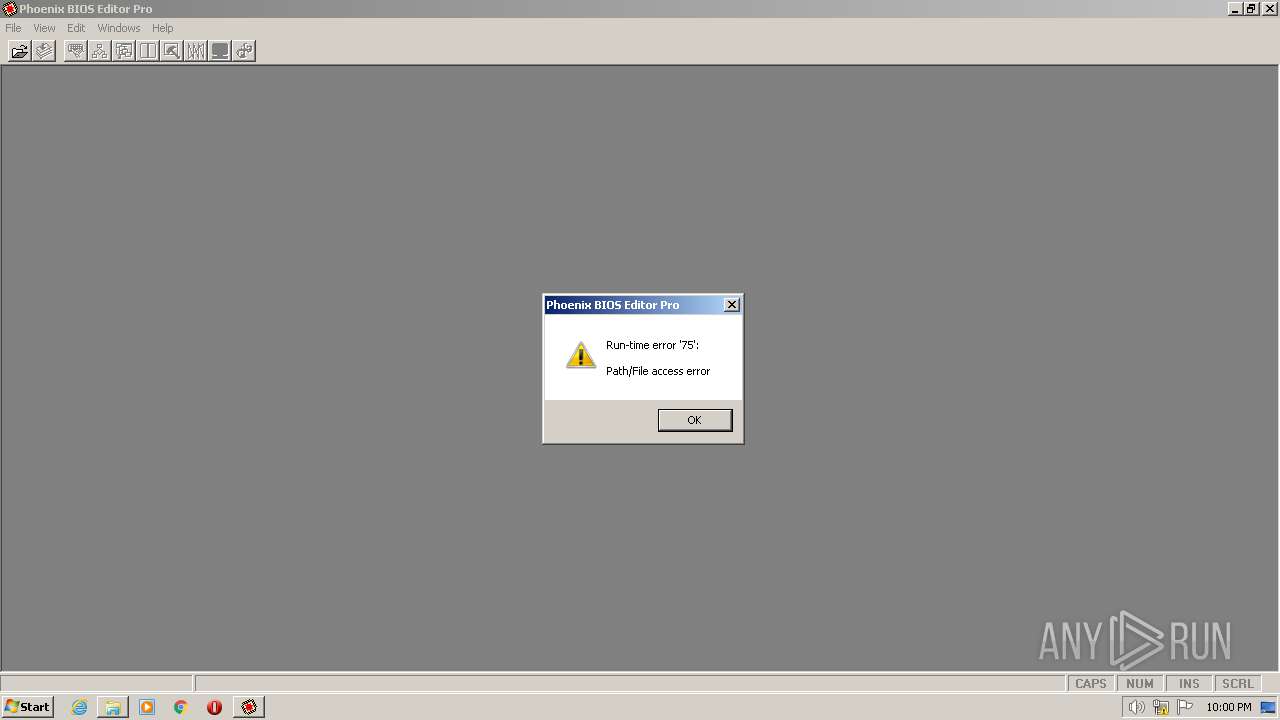
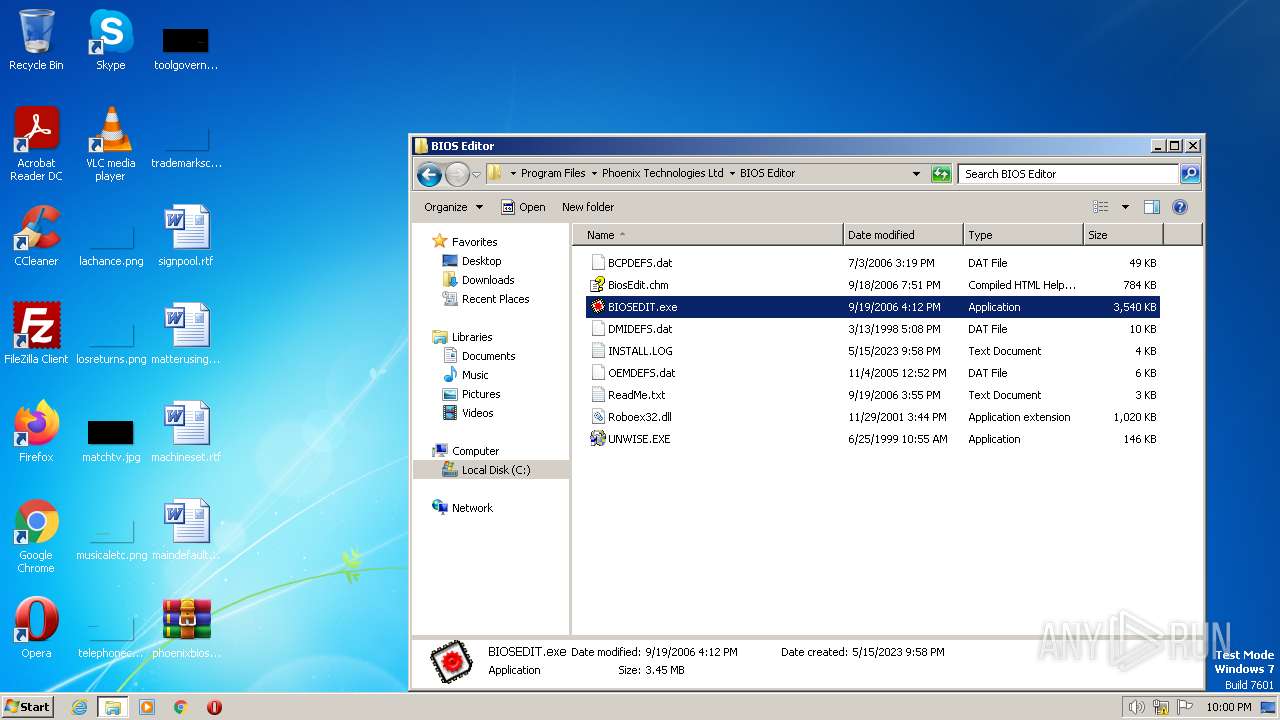
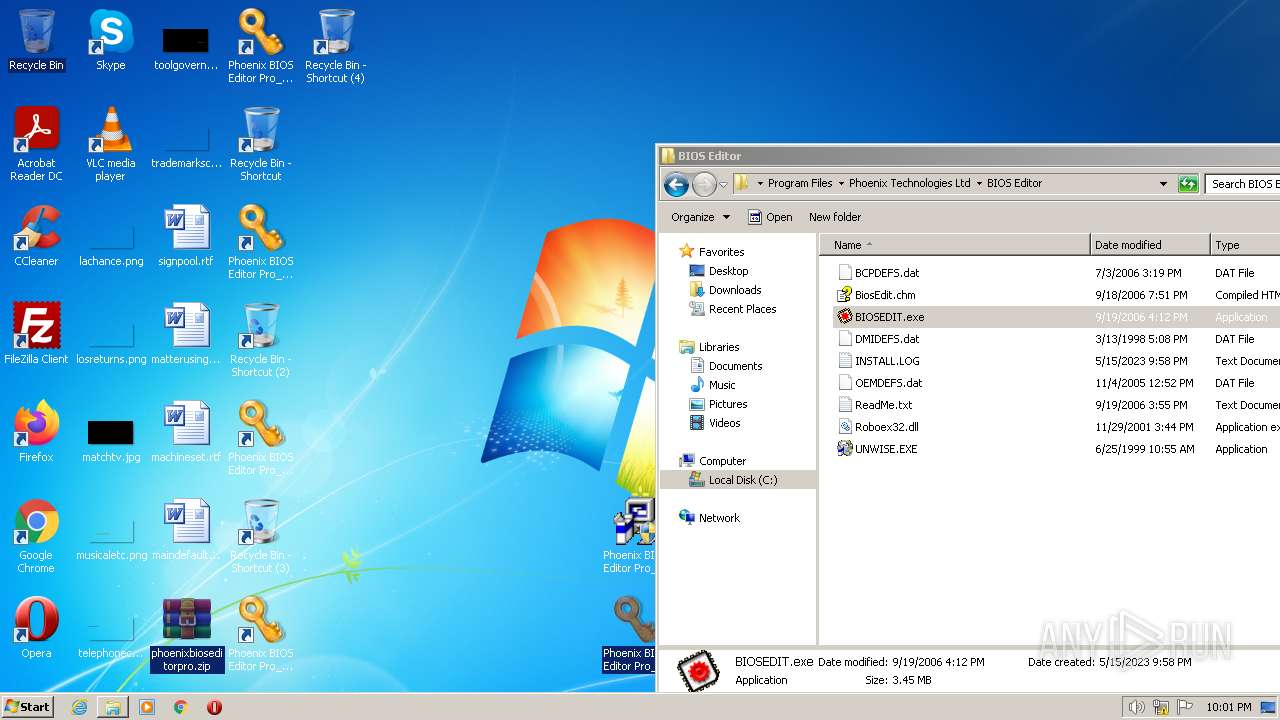
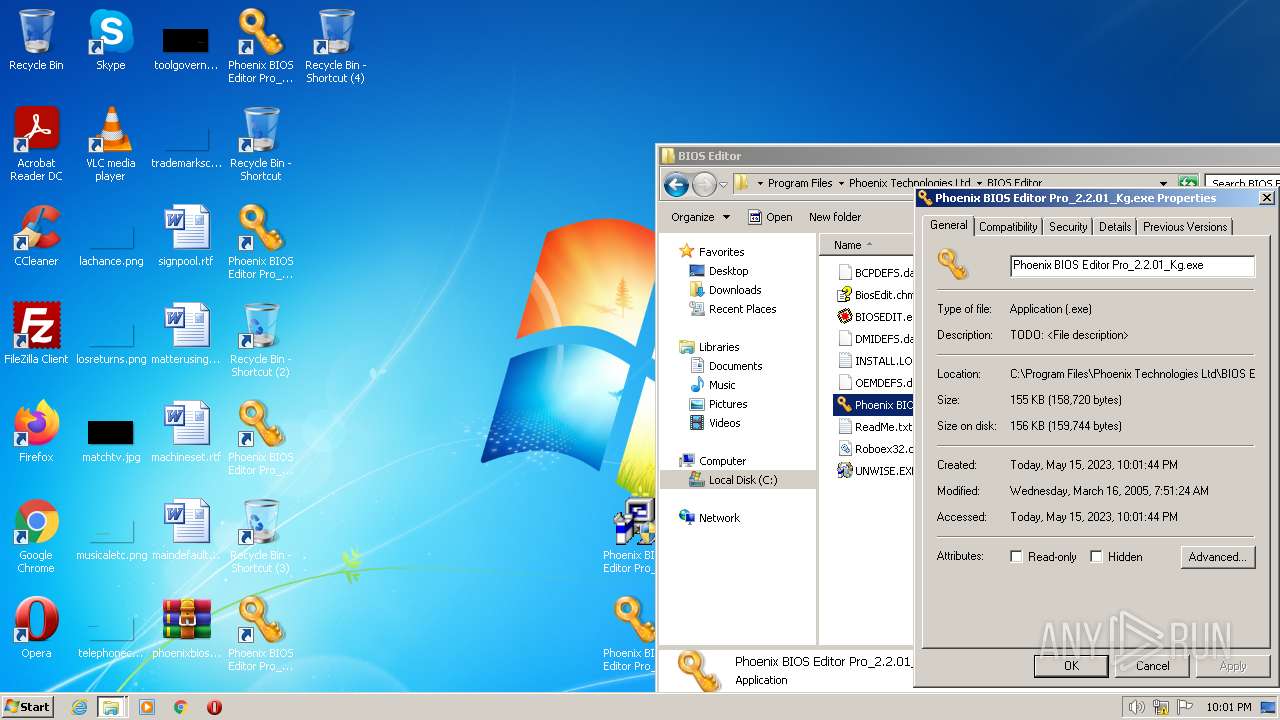
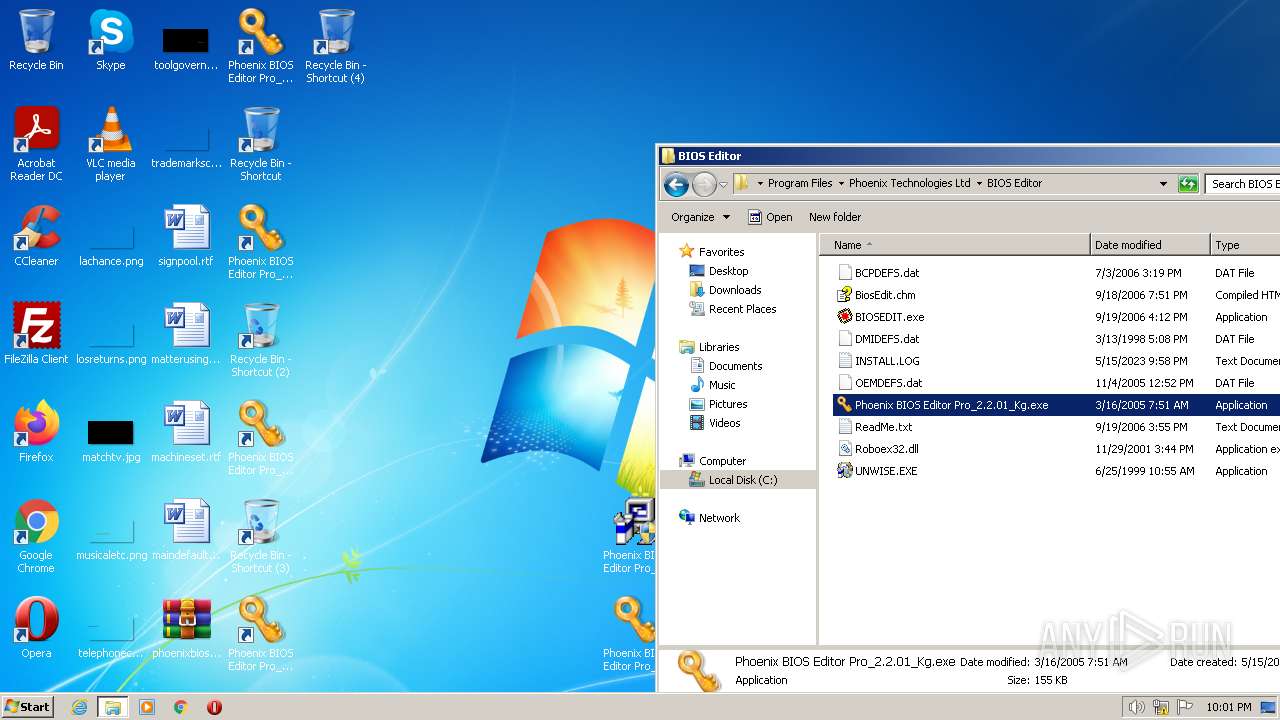
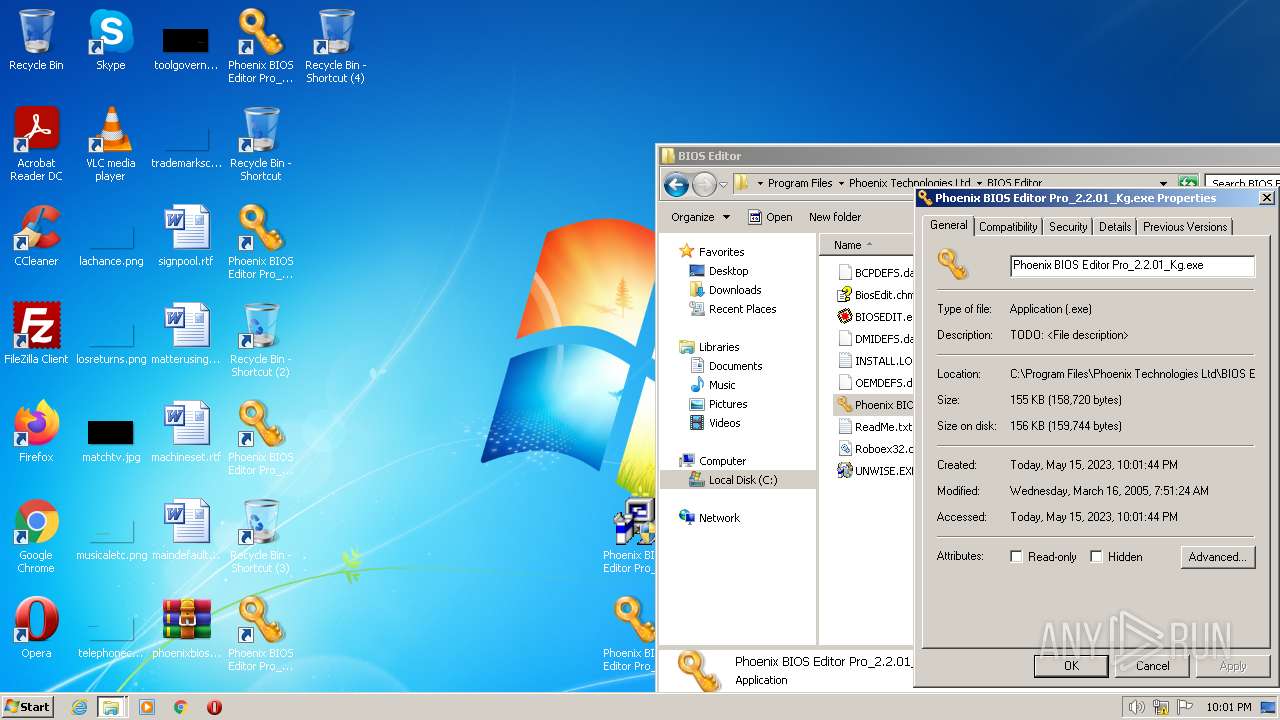
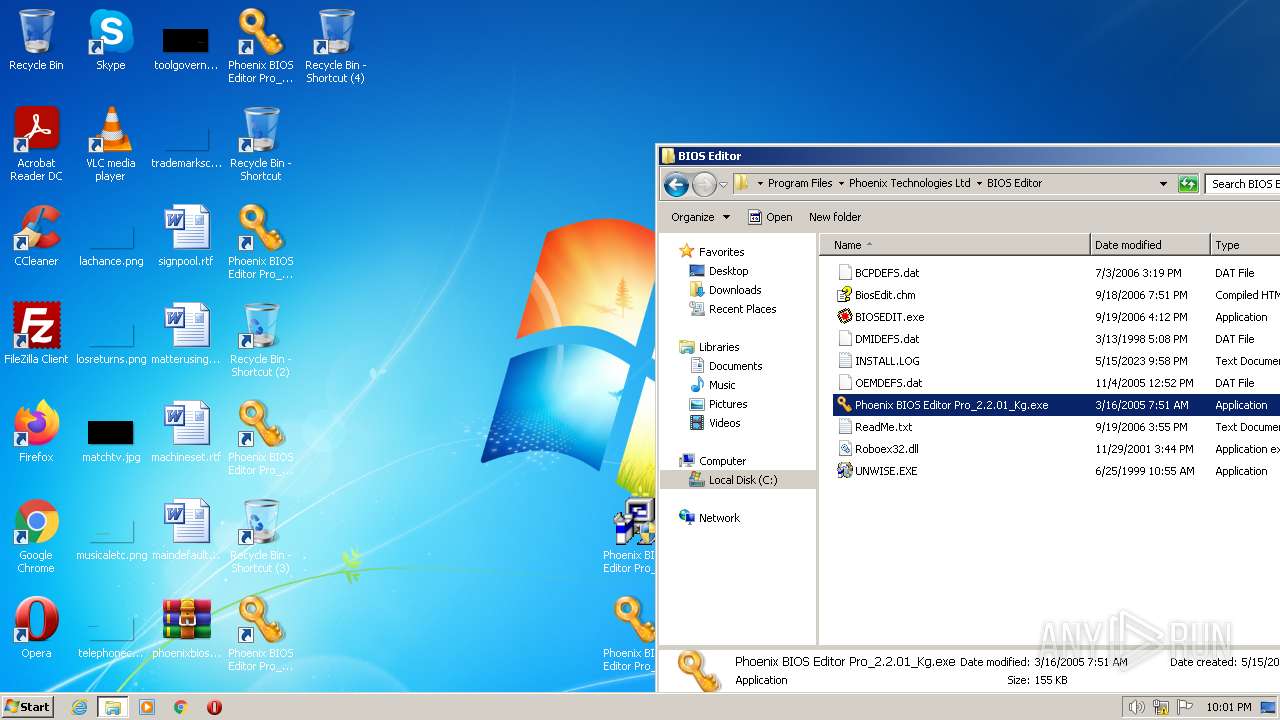
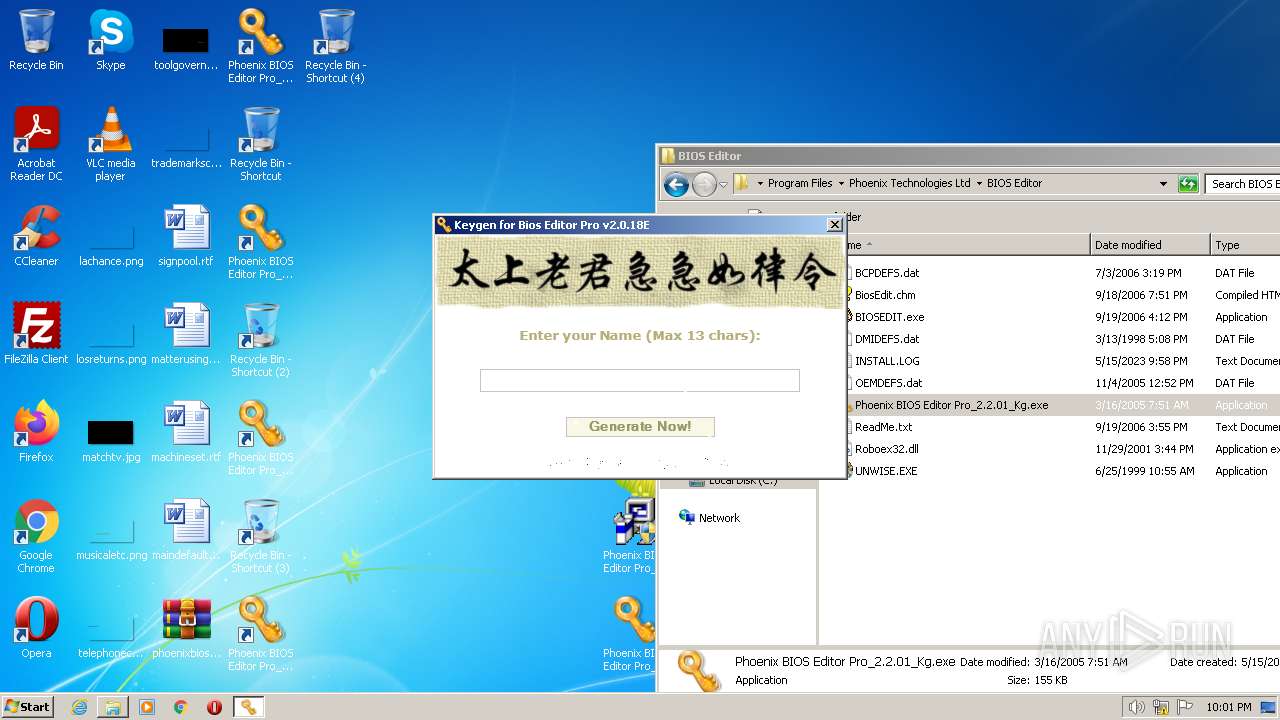
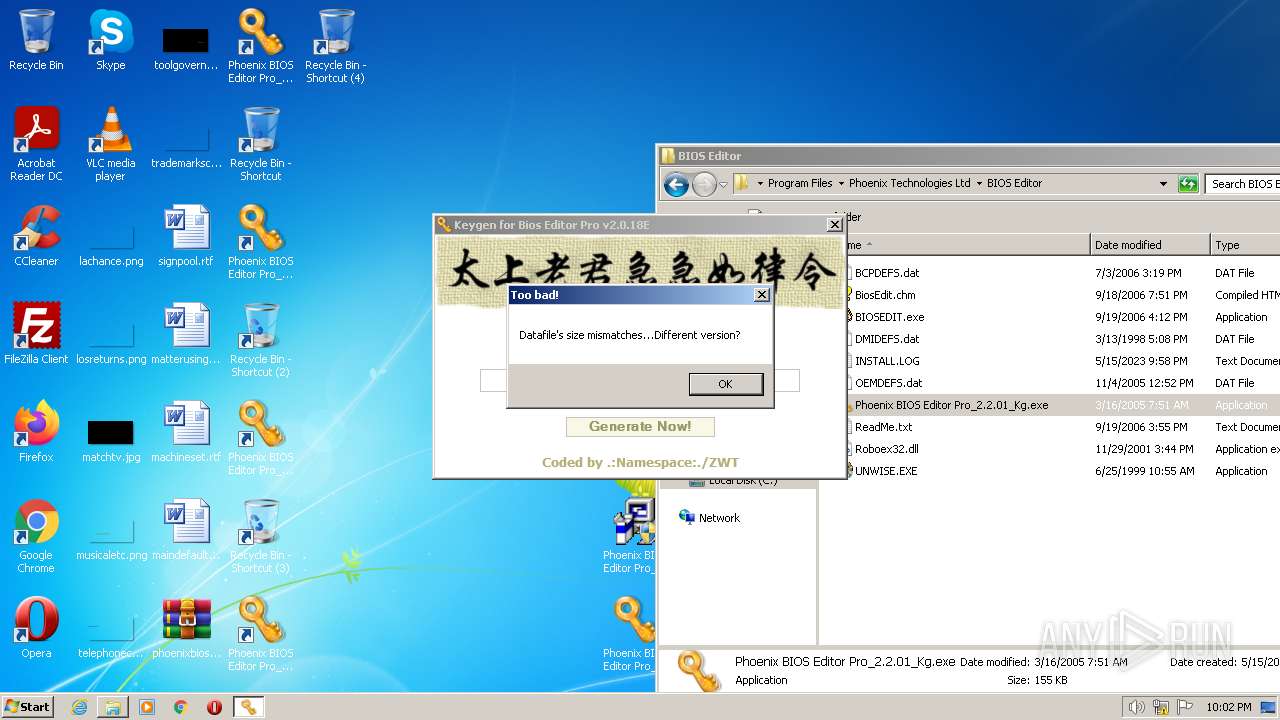
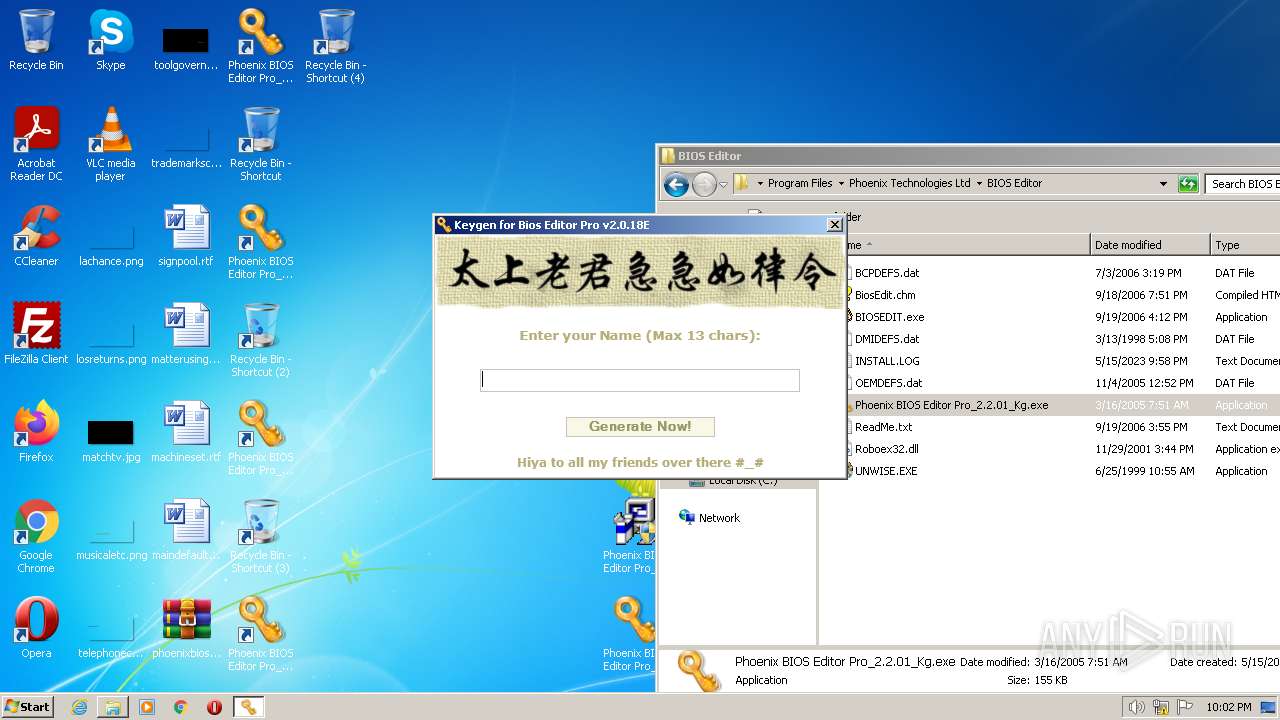
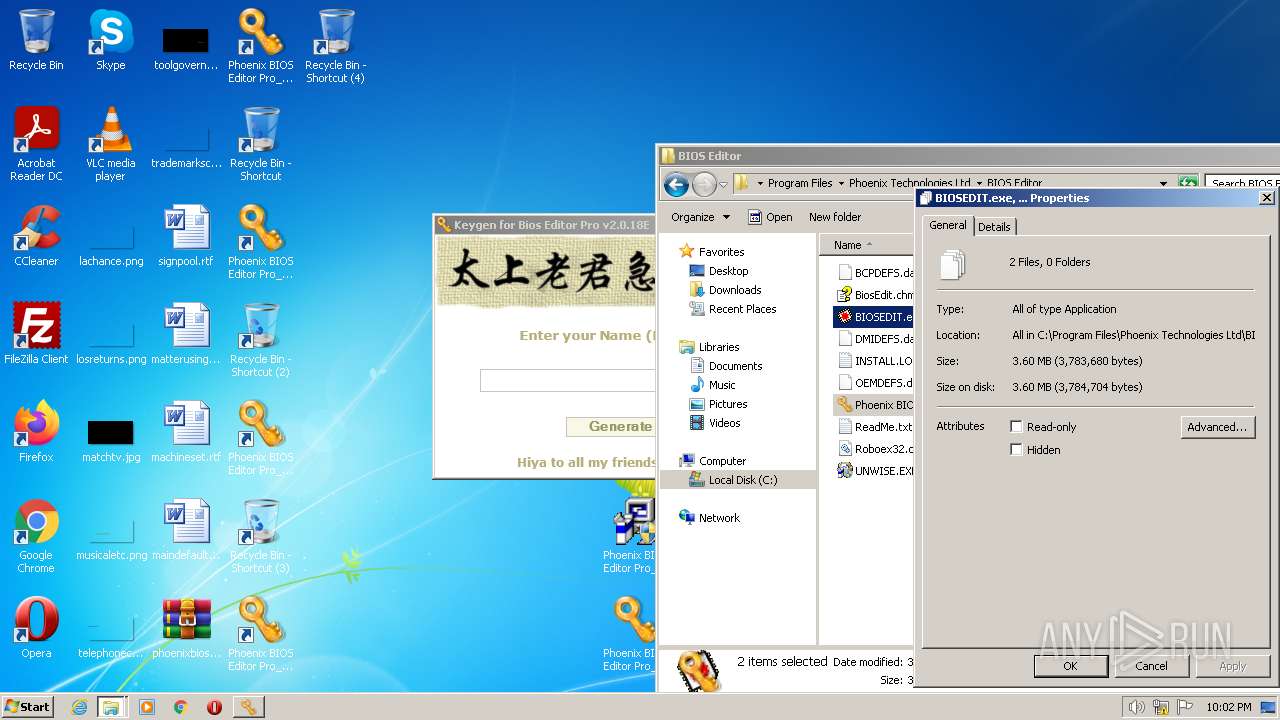
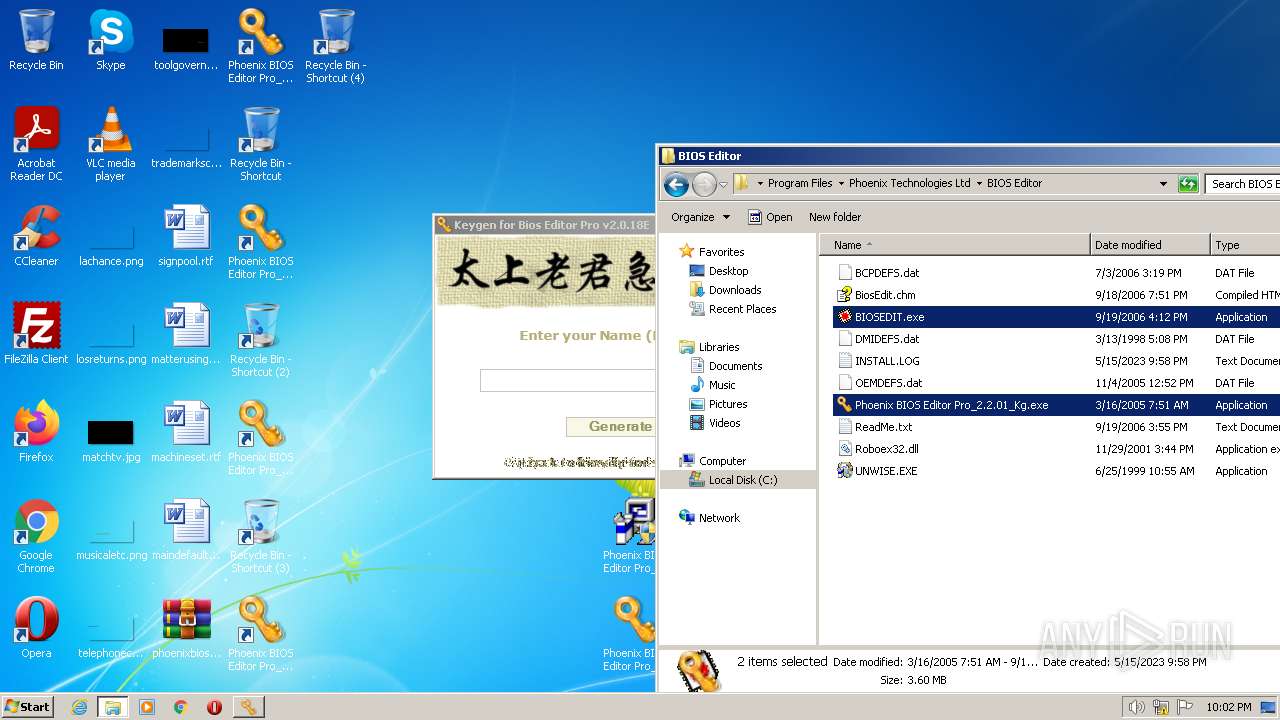
| File name: | phoenixbioseditorpro.zip |
| Full analysis: | https://app.any.run/tasks/2f7fc2de-6889-4dd9-ba4f-0c74d6d85236 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2023, 20:57:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D63A0D8009FEDF027E2D8C62E381DD62 |
| SHA1: | 82D114DE11D077141BCBB8572A761F22084281B8 |
| SHA256: | 00815EDF549AC844F47C29FE1B91EF65D92B65F2CDD1D1E0254C795CAEEA9A1F |
| SSDEEP: | 196608:bZ8T0LKd+B/fs3PZWL02lAXFDBICUbB6aI9Dd:bZhedC/WZWRlyFDBIChaI9Dd |
MALICIOUS
Creates a writable file the system directory
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 2432)
SUSPICIOUS
Creates/Modifies COM task schedule object
- GLJ53EA.tmp (PID: 3376)
- GLJ53EA.tmp (PID: 3140)
Starts application with an unusual extension
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
Reads Microsoft Outlook installation path
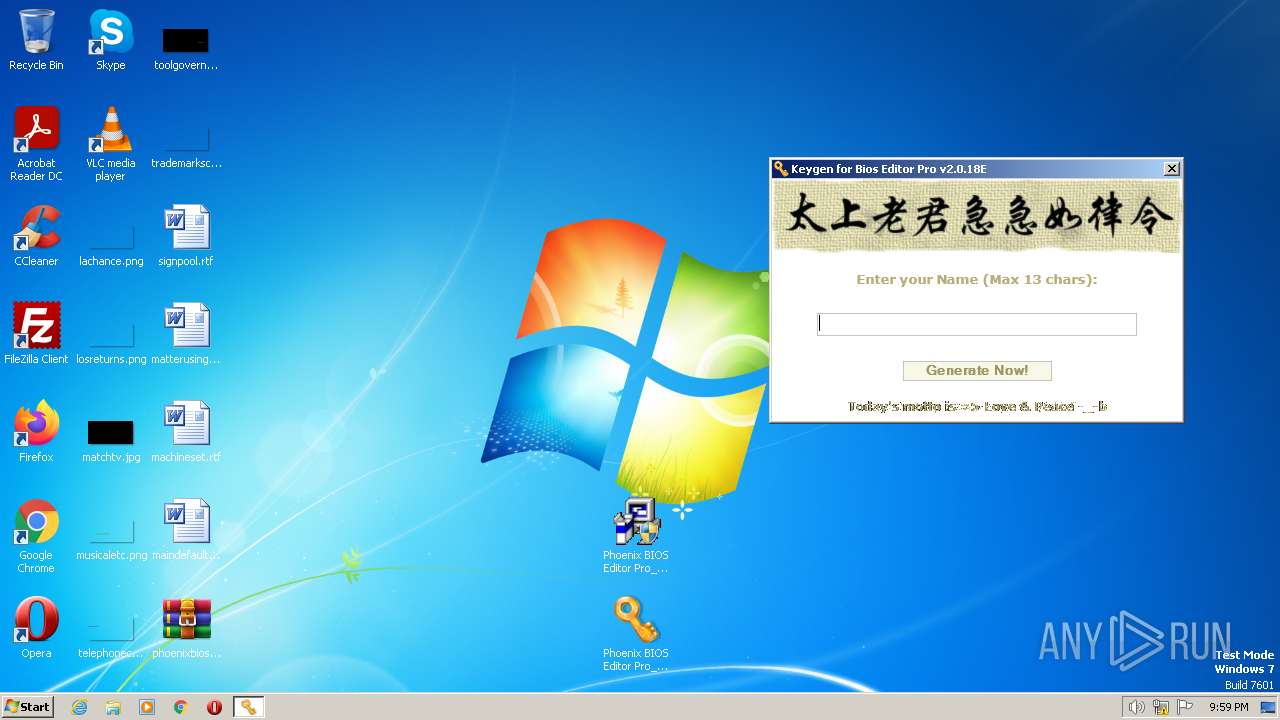
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Reads Internet Explorer settings
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Reads the Internet Settings
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Executable content was dropped or overwritten
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 2432)
- dllhost.exe (PID: 1572)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
INFO
Manual execution by a user
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3784)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3616)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 2432)
- BIOSEDIT.exe (PID: 3424)
- BIOSEDIT.exe (PID: 2452)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
The process checks LSA protection
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- BIOSEDIT.exe (PID: 2452)
- dllhost.exe (PID: 1572)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
- BIOSEDIT.exe (PID: 3424)
Reads mouse settings
- GLJ53EA.tmp (PID: 3376)
Reads the computer name
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
- GLJ53EA.tmp (PID: 3140)
- GLJ53EA.tmp (PID: 3376)
- GLJ53EA.tmp (PID: 2020)
- GLJ53EA.tmp (PID: 2192)
- GLJ53EA.tmp (PID: 4000)
- GLJ53EA.tmp (PID: 1820)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 2432)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Checks supported languages
- GLJ53EA.tmp (PID: 3140)
- GLJ53EA.tmp (PID: 3376)
- GLJ53EA.tmp (PID: 2020)
- GLJ53EA.tmp (PID: 2192)
- GLJ53EA.tmp (PID: 4000)
- GLJ53EA.tmp (PID: 1820)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 2432)
- BIOSEDIT.exe (PID: 3424)
- BIOSEDIT.exe (PID: 2452)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
Creates files in the program directory
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
- dllhost.exe (PID: 1572)
Creates files or folders in the user directory
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Reads the machine GUID from the registry
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- BIOSEDIT.exe (PID: 3424)
- BIOSEDIT.exe (PID: 2452)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Checks proxy server information
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 2000)
- Phoenix BIOS Editor Pro_2.2.01_Kg.exe (PID: 3296)
Create files in a temporary directory
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 2432)
- BIOSEDIT.exe (PID: 3424)
- BIOSEDIT.exe (PID: 2452)
- Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe (PID: 3992)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe |
|---|---|
| ZipUncompressedSize: | 6349847 |
| ZipCompressedSize: | 6331991 |
| ZipCRC: | 0x1d4a6d2e |
| ZipModifyDate: | 2008:04:21 08:25:54 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
70
Monitored processes
16
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1572 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp" C:\Windows\System32\ComCtl32.ocx | C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp | — | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2000 | "C:\Users\admin\Desktop\Phoenix BIOS Editor Pro_2.2.01_Kg.exe" | C:\Users\admin\Desktop\Phoenix BIOS Editor Pro_2.2.01_Kg.exe | — | explorer.exe | |||||||||||
User: admin Company: TODO: <Company name> Integrity Level: MEDIUM Description: TODO: <File description> Exit code: 2 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp" C:\Windows\System32\COMDLG32.OCX | C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp | — | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp" C:\Windows\System32\MsFlxGrd.ocx | C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp | — | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Desktop\Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe" | C:\Users\admin\Desktop\Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Phoenix Technologies Ltd\BIOS Editor\BIOSEDIT.exe" | C:\Program Files\Phoenix Technologies Ltd\BIOS Editor\BIOSEDIT.exe | — | explorer.exe | |||||||||||
User: admin Company: Phoenix Integrity Level: MEDIUM Exit code: 0 Version: 2.02 Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp" C:\Windows\System32\COMDLG32.OCX | C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp | — | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3296 | "C:\Program Files\Phoenix Technologies Ltd\BIOS Editor\Phoenix BIOS Editor Pro_2.2.01_Kg.exe" | C:\Program Files\Phoenix Technologies Ltd\BIOS Editor\Phoenix BIOS Editor Pro_2.2.01_Kg.exe | — | explorer.exe | |||||||||||
User: admin Company: TODO: <Company name> Integrity Level: MEDIUM Description: TODO: <File description> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp" C:\Windows\System32\MSCOMCTL.OCX | C:\Users\admin\AppData\Local\Temp\GLJ53EA.tmp | — | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
5 304
Read events
4 918
Write events
184
Delete events
202
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
92
Suspicious files
20
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Users\admin\AppData\Local\Temp\~GLH0001.TMP | text | |
MD5:A7F5438EDDA1871FE1417D77B332F3EF | SHA256:7DA54C8C8908DAA9322A33129ADAACCDFEEFA59495E8F2B5E9EA064CFD173717 | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3980.27767\Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | executable | |
MD5:F83EC4811A9416F4321D9CE501AD8407 | SHA256:979EF1A4AE3F528636E3BF05ECBBF8E1BCEA4E685008BB06E8459987A22F994E | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Windows\system32\~GLH0002.TMP | executable | |
MD5:12C2755D14B2E51A4BB5CBDFC22ECB11 | SHA256:3B6CCDB560D7CD4748E992BD82C799ACD1BBCFC922A13830CA381D976FFCCCAF | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Users\admin\AppData\Local\Temp\GLC53DA.tmp | executable | |
MD5:ACFCAB119456B15BB70BACEB81BD7E5F | SHA256:76C0A0AA1A6A2E050A24795D772BA598CF074A1BB4C8C62658B9E55DBF3A89BD | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Users\admin\AppData\Local\Temp\GLK55FF.tmp | executable | |
MD5:3DF61E5730883B2D338ADDD7ACBE4BC4 | SHA256:2EFE9A54C8EB878711D9B6CD18F276838645AFF52FE69D8A864376CB258EC616 | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Windows\system32\temp.001 | executable | |
MD5:D76F0EAB36F83A31D411AEAF70DA7396 | SHA256:46F4FDB12C30742FF4607876D2F36CF432CDC7EC3D2C99097011448FC57E997C | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Program Files\Phoenix Technologies Ltd\BIOS Editor\~GLH0005.TMP | executable | |
MD5:443E13846997C537E8F5ED61130AB705 | SHA256:49EF36BD01B8EBF38C7B807A5FB44CBAF47C9D4EFA883B01C41494C61AE4A2E2 | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Users\admin\AppData\Local\Temp\GLF5FB6.tmp | executable | |
MD5:B9B41E50D612E00BF3A49A6405B89D74 | SHA256:50E7A30E1825FAB93B94B698C2C6D2CC1787B094C6CEE53EEED5C497F77443C9 | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | executable | |
MD5:B9B41E50D612E00BF3A49A6405B89D74 | SHA256:50E7A30E1825FAB93B94B698C2C6D2CC1787B094C6CEE53EEED5C497F77443C9 | |||
| 3992 | Phoenix BIOS Editor Pro_2.2.0.1_Setup.exe | C:\Windows\system32\temp.000 | executable | |
MD5:12C2755D14B2E51A4BB5CBDFC22ECB11 | SHA256:3B6CCDB560D7CD4748E992BD82C799ACD1BBCFC922A13830CA381D976FFCCCAF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3404 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |