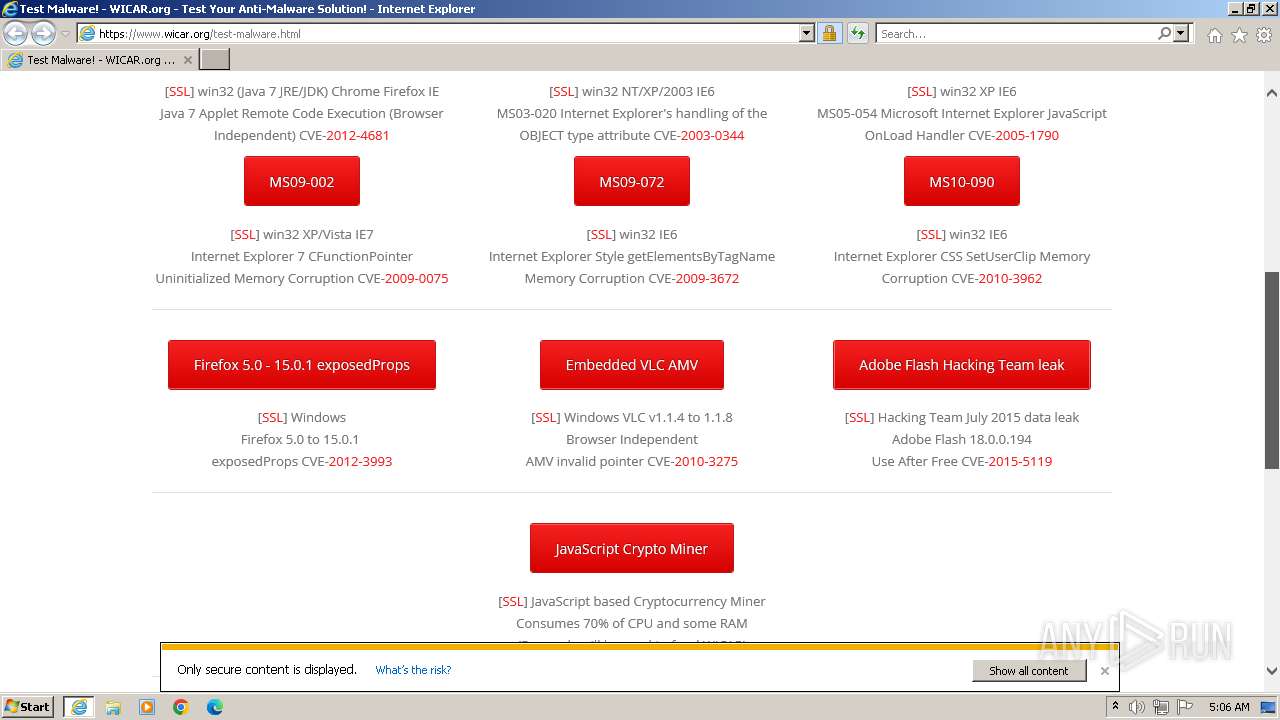
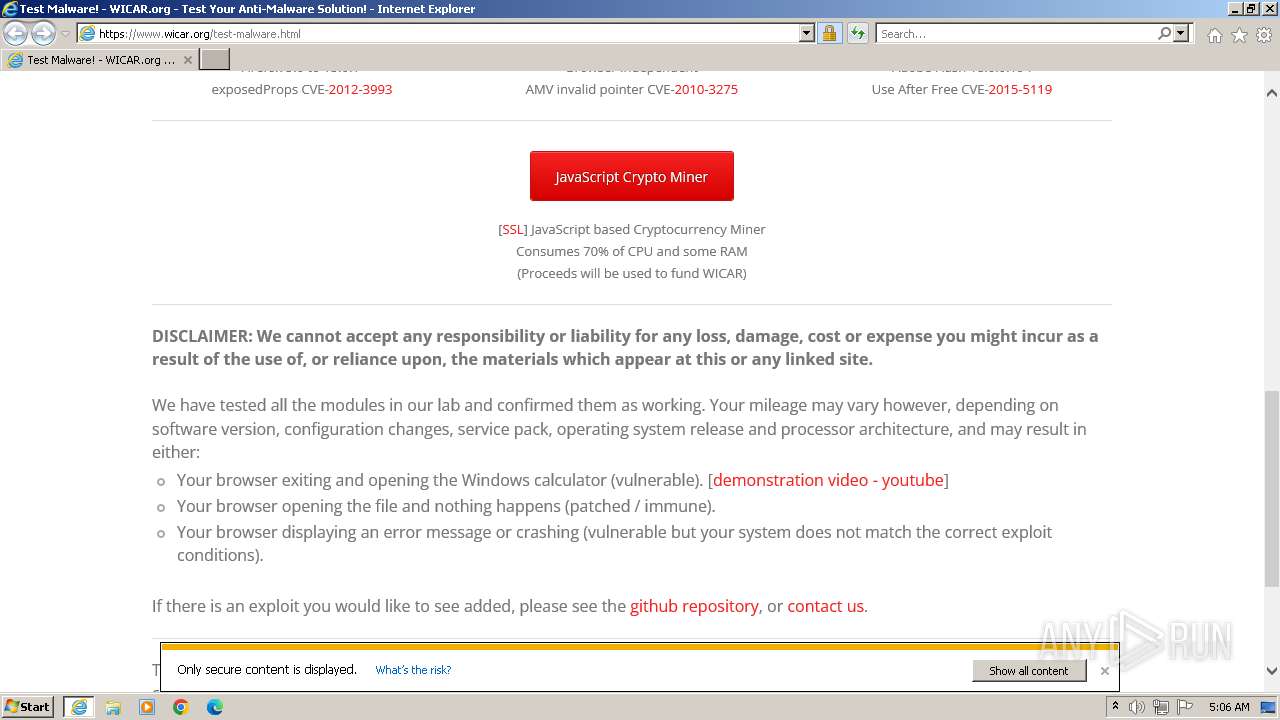
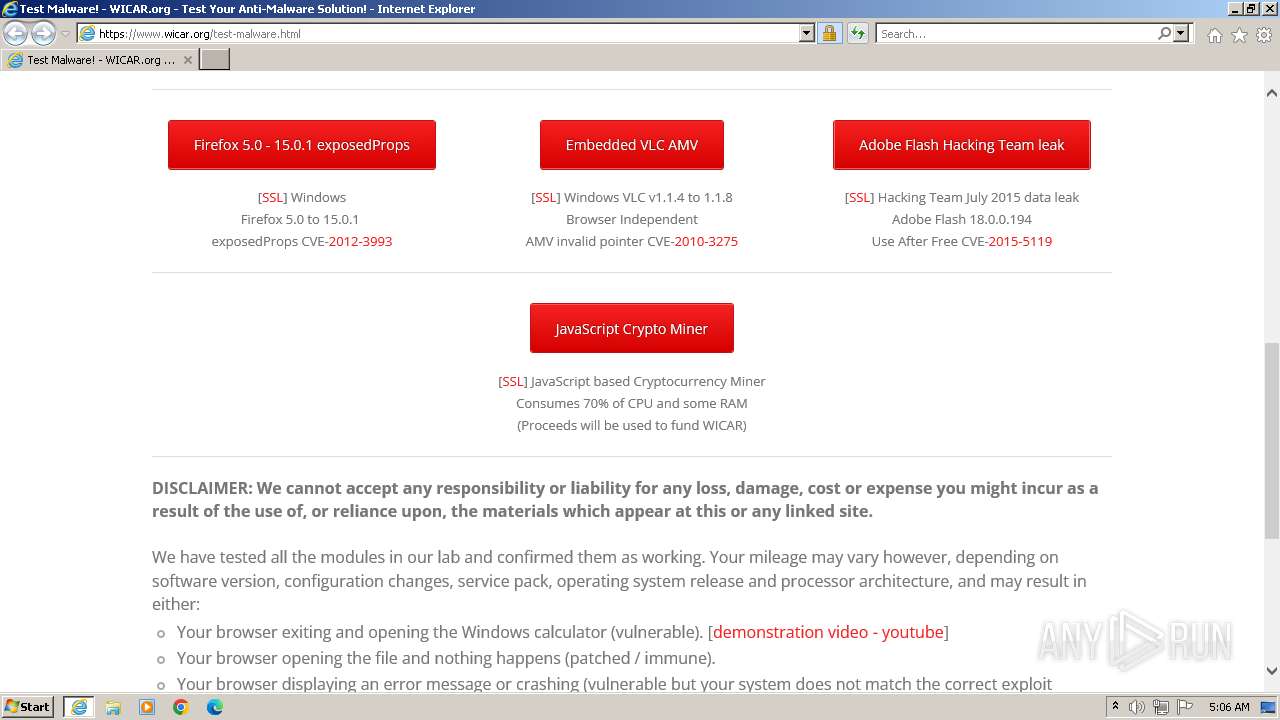
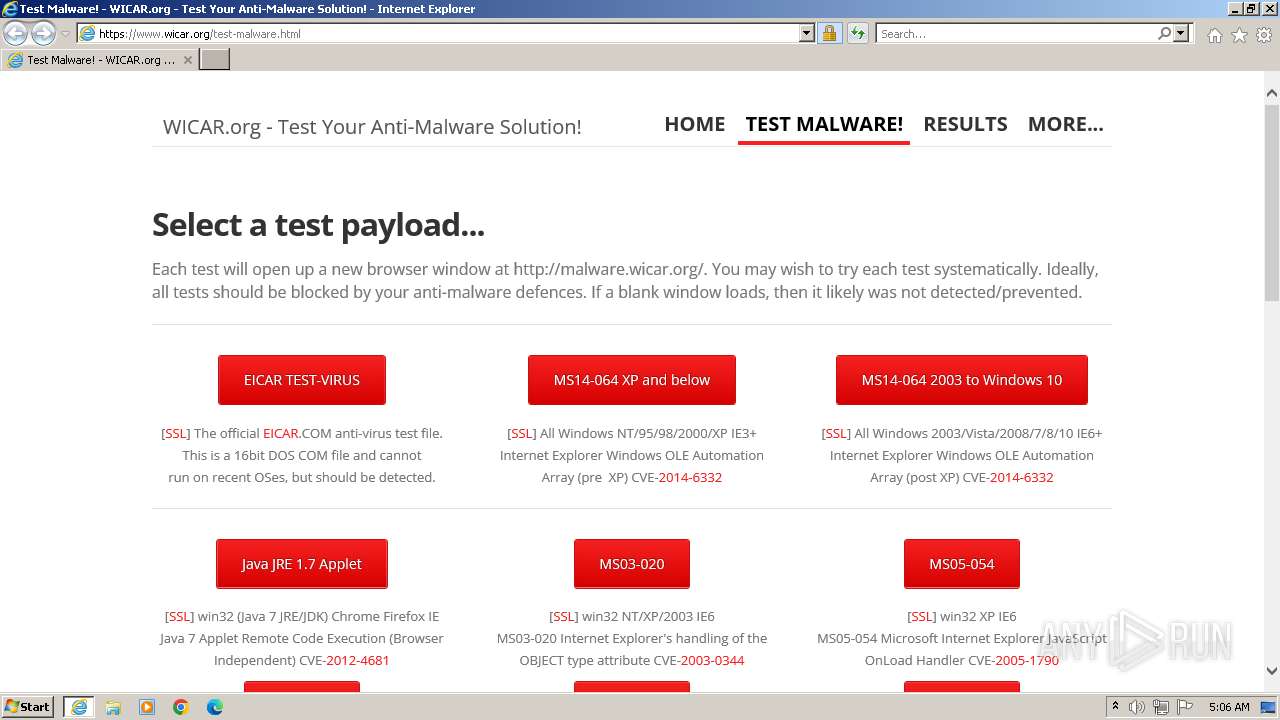
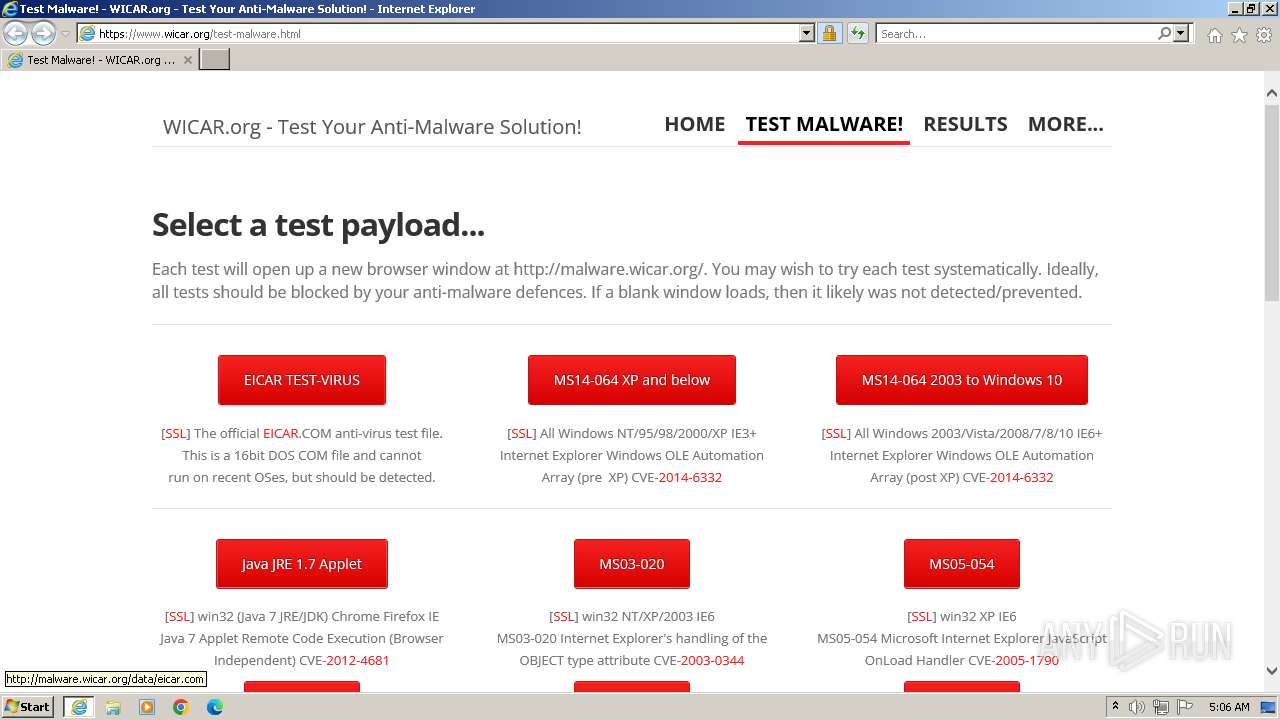
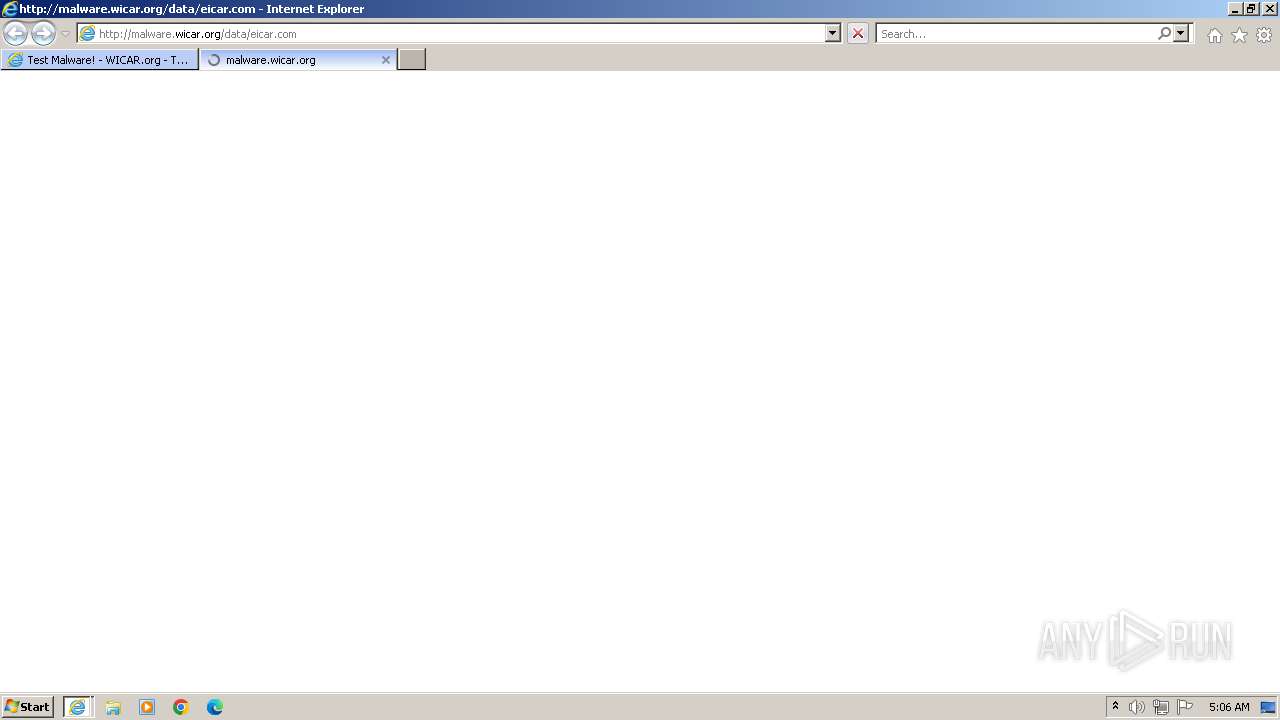
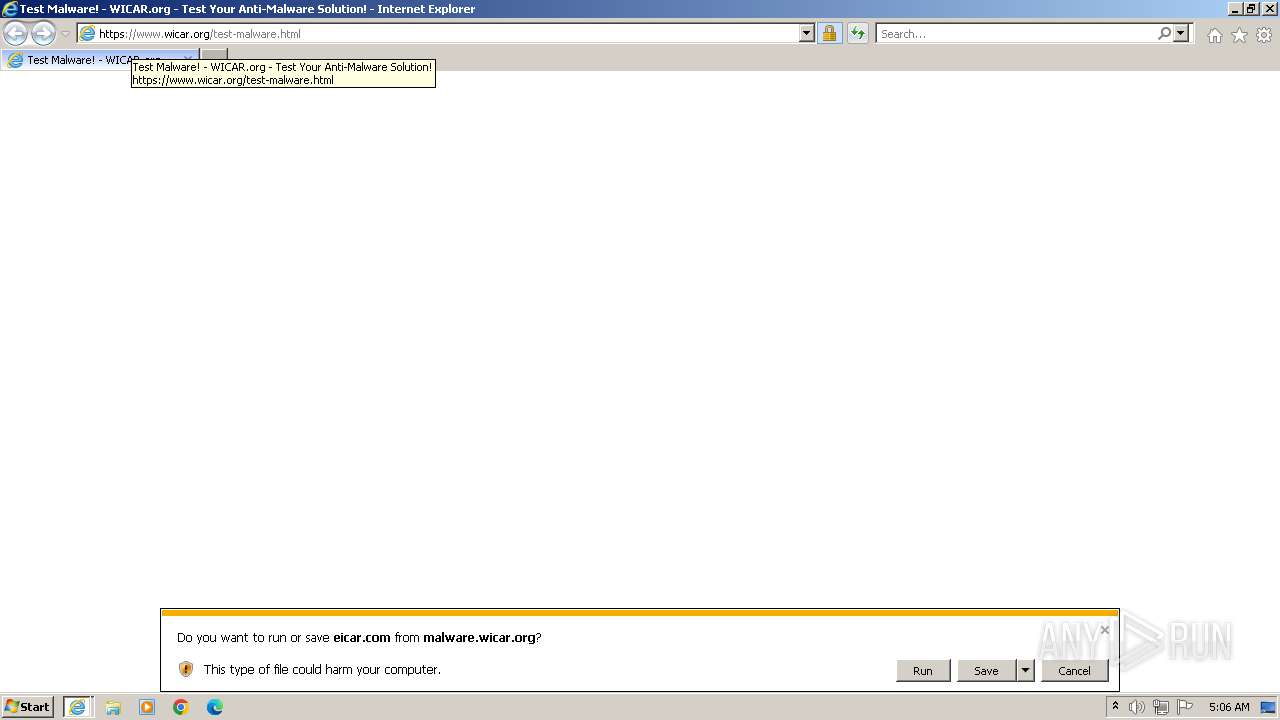
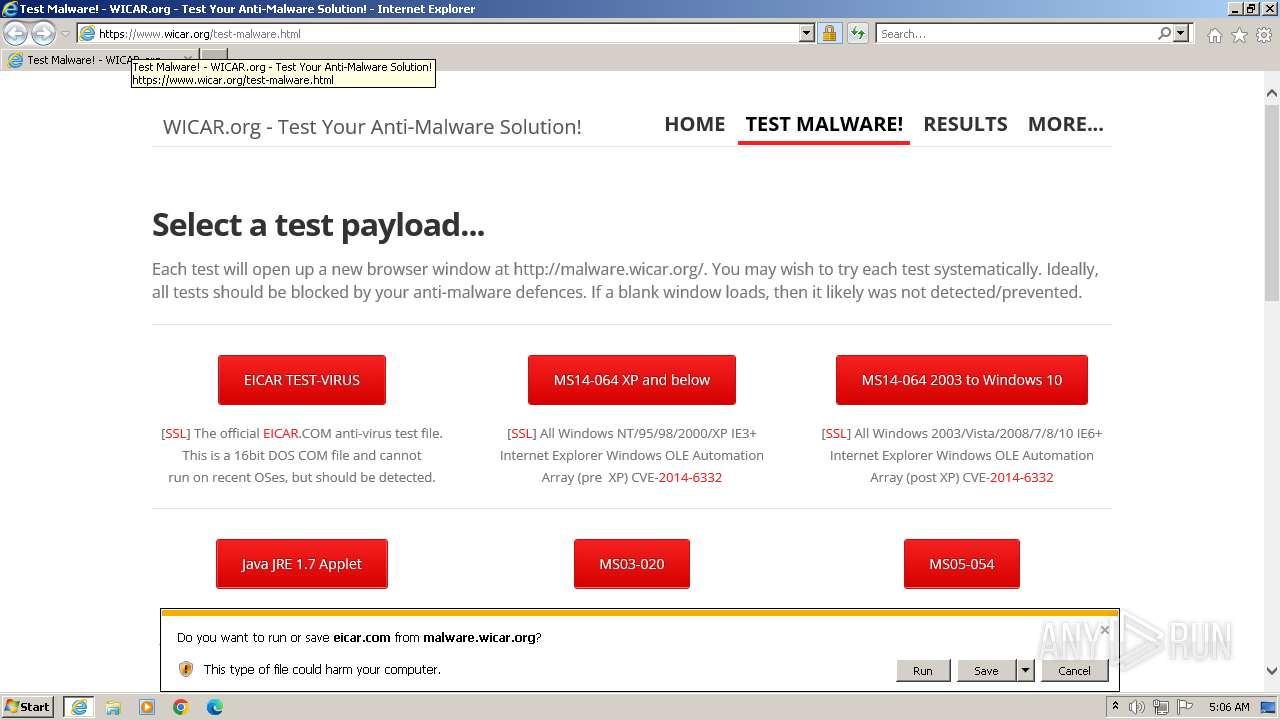
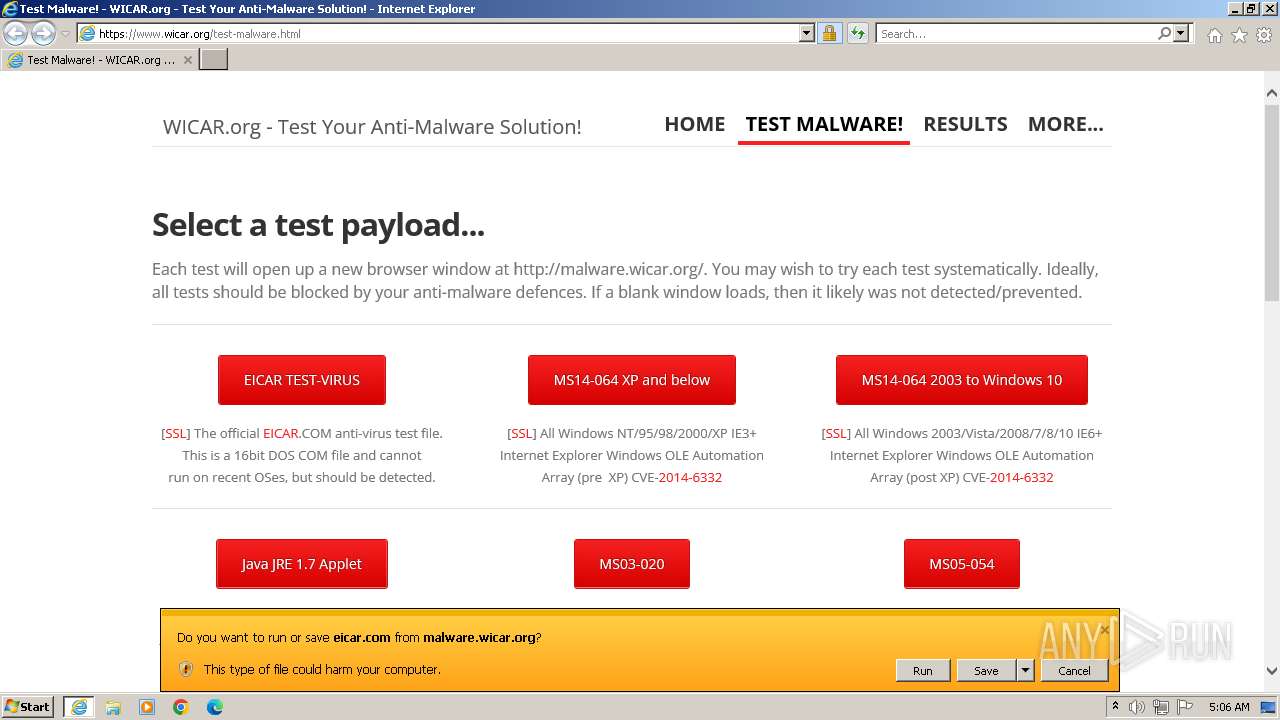
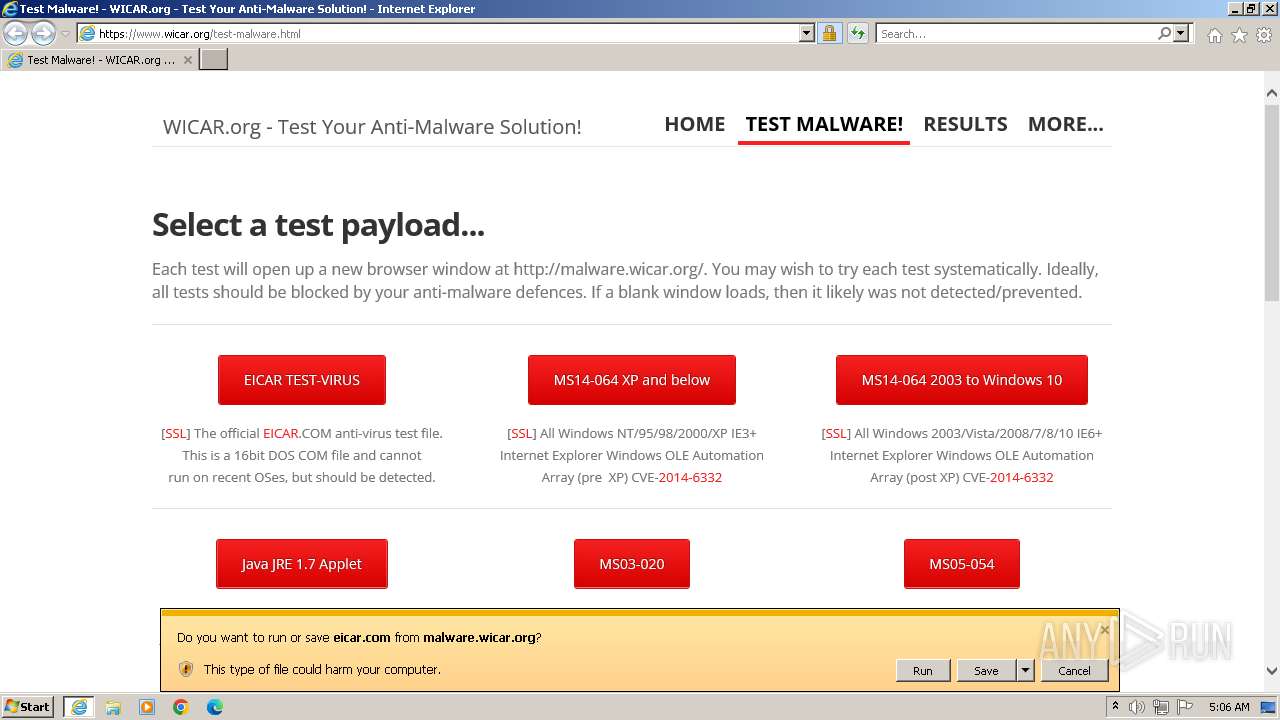
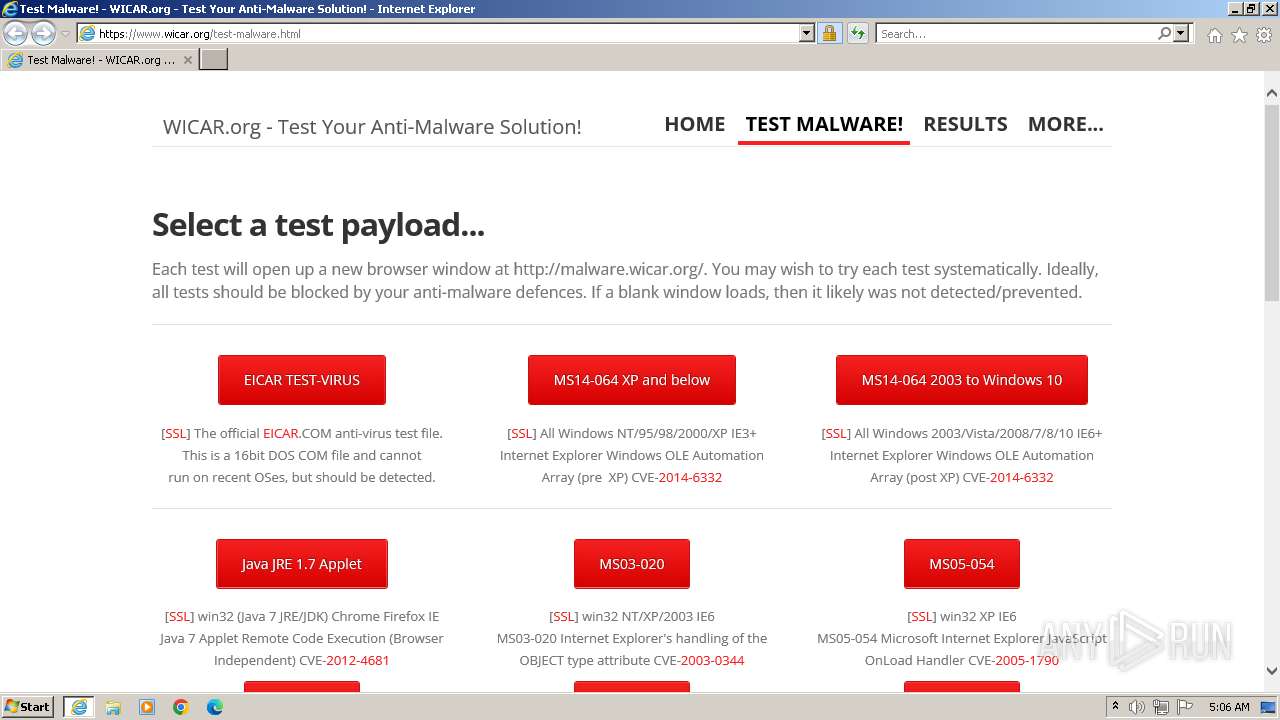
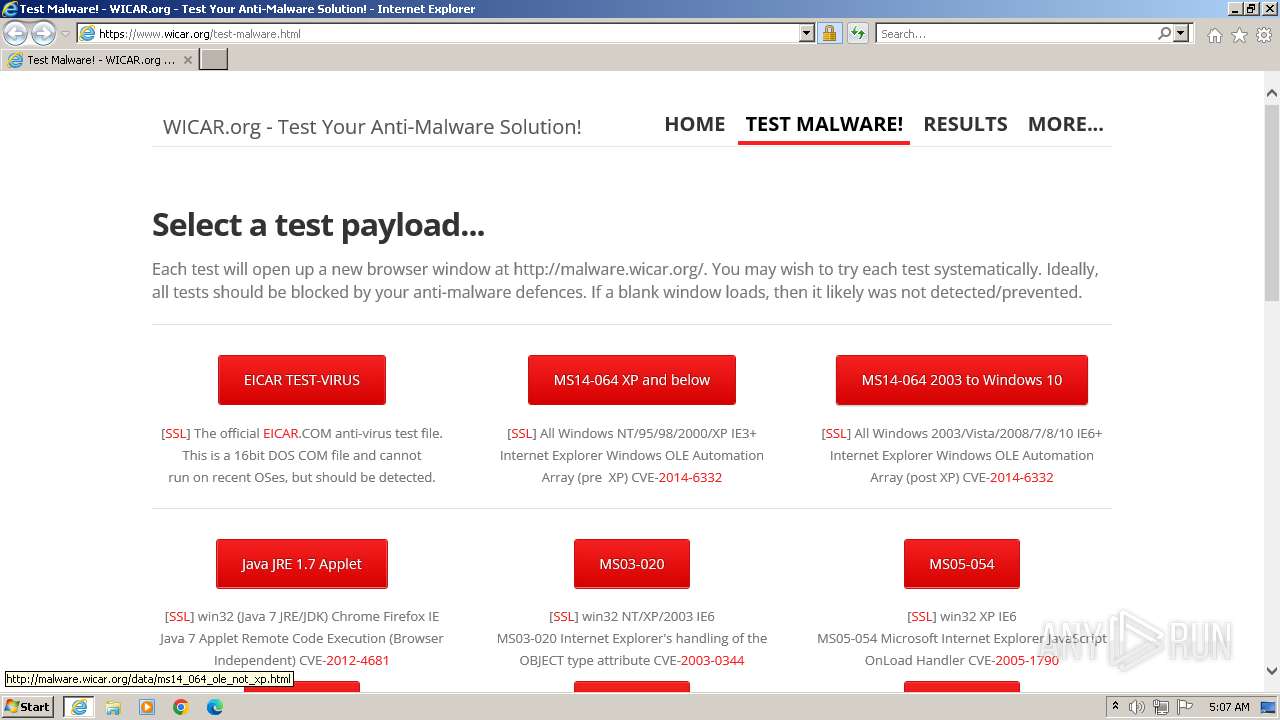
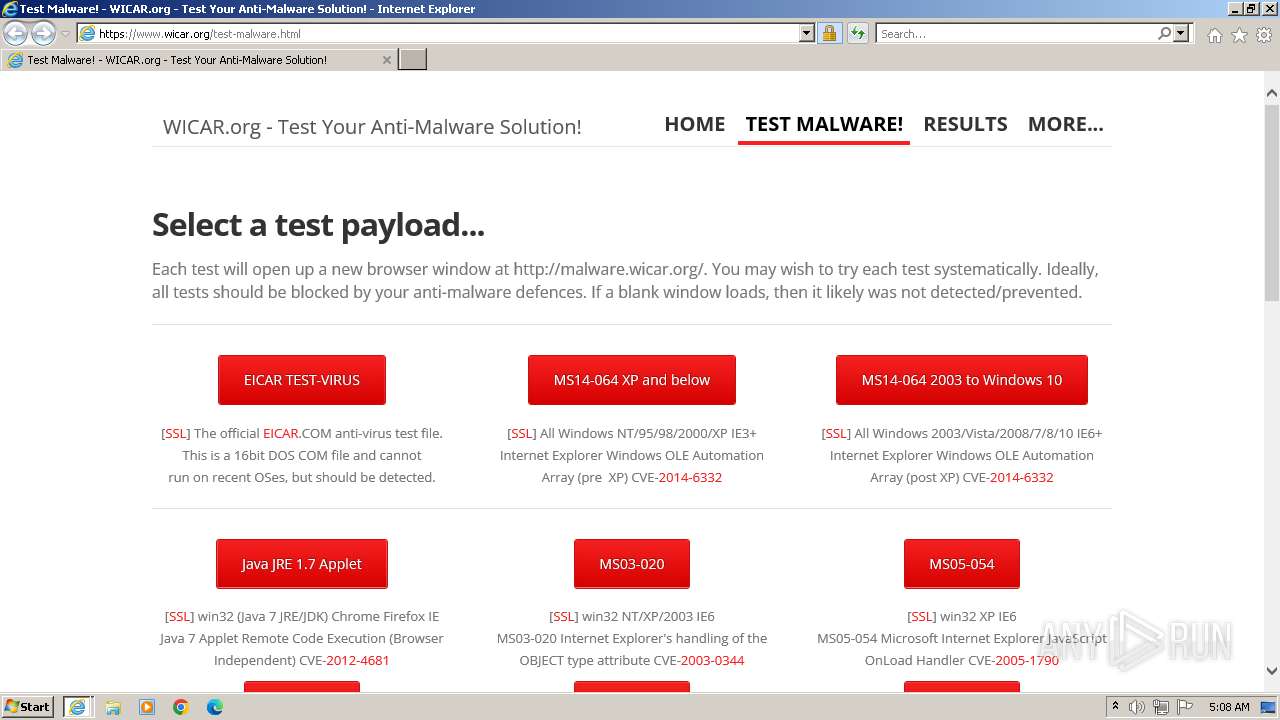
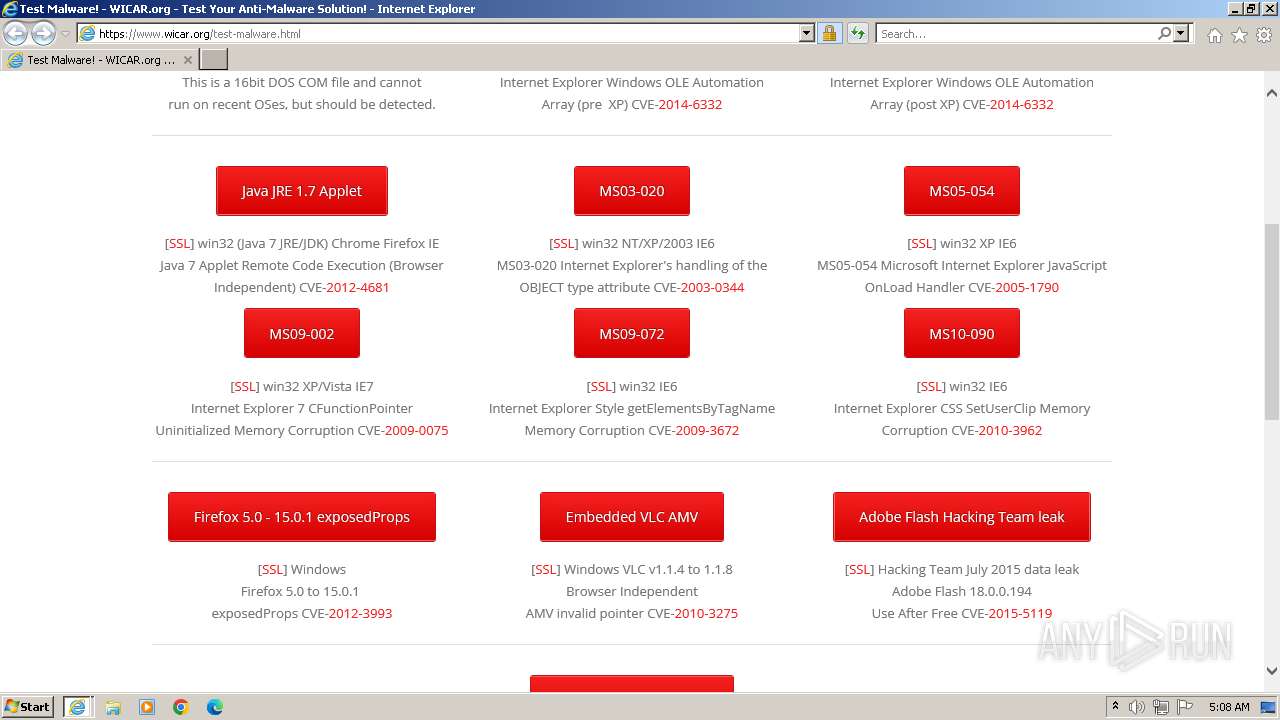
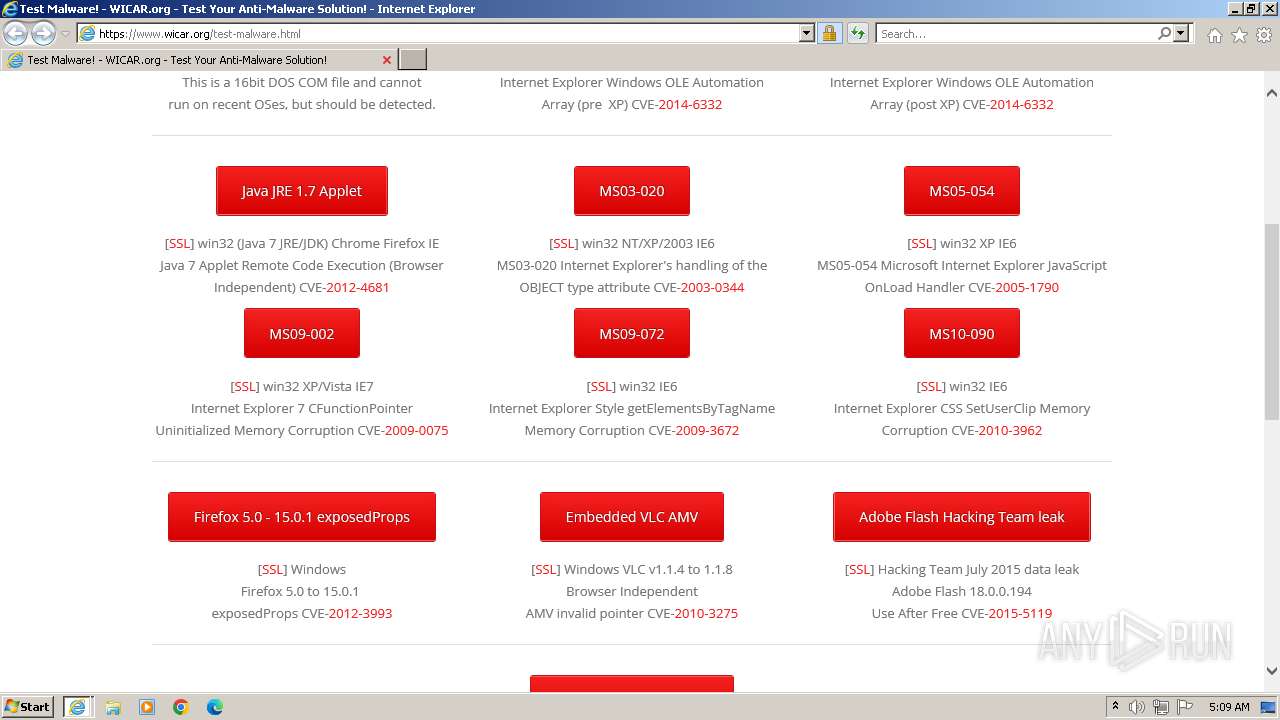
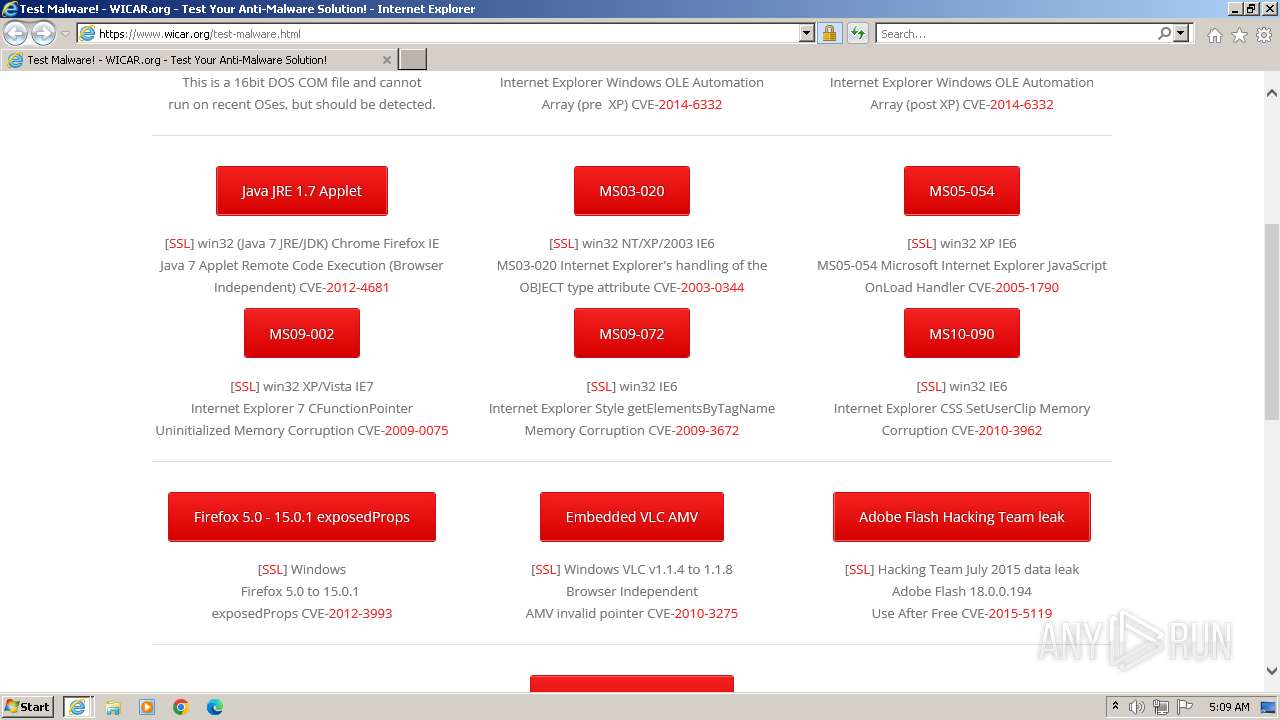
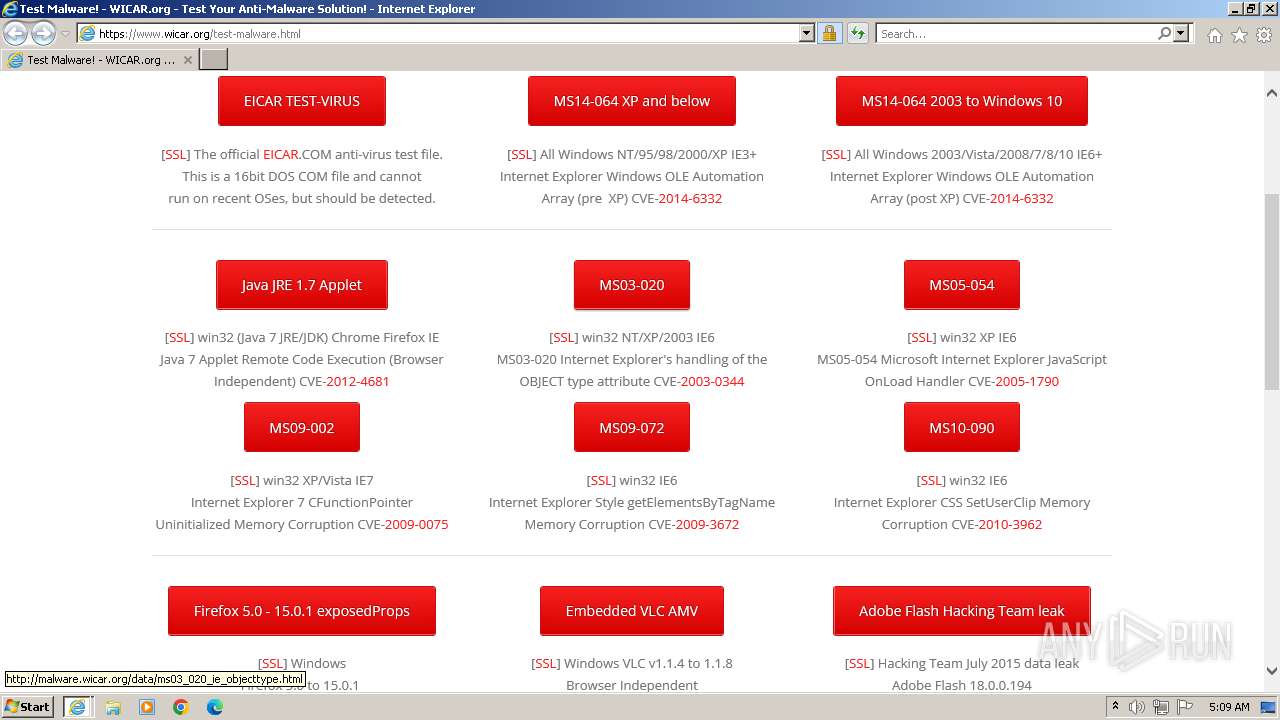
| URL: | www.wicar.org/test-malware.html |
| Full analysis: | https://app.any.run/tasks/499d1b7d-3a54-41bd-84b4-895454ad5be2 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 04:05:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | 6398D01FFFF9A563DE6FE5BF5D5327A8F7B79B62 |
| SHA256: | 0073A1A2A1579FE63B9BBDD2EF0350E791773B0EE4DD7CF9894E0A0845511938 |
| SSDEEP: | 3:EHYf9OkIJn:ZoBJ |
MALICIOUS
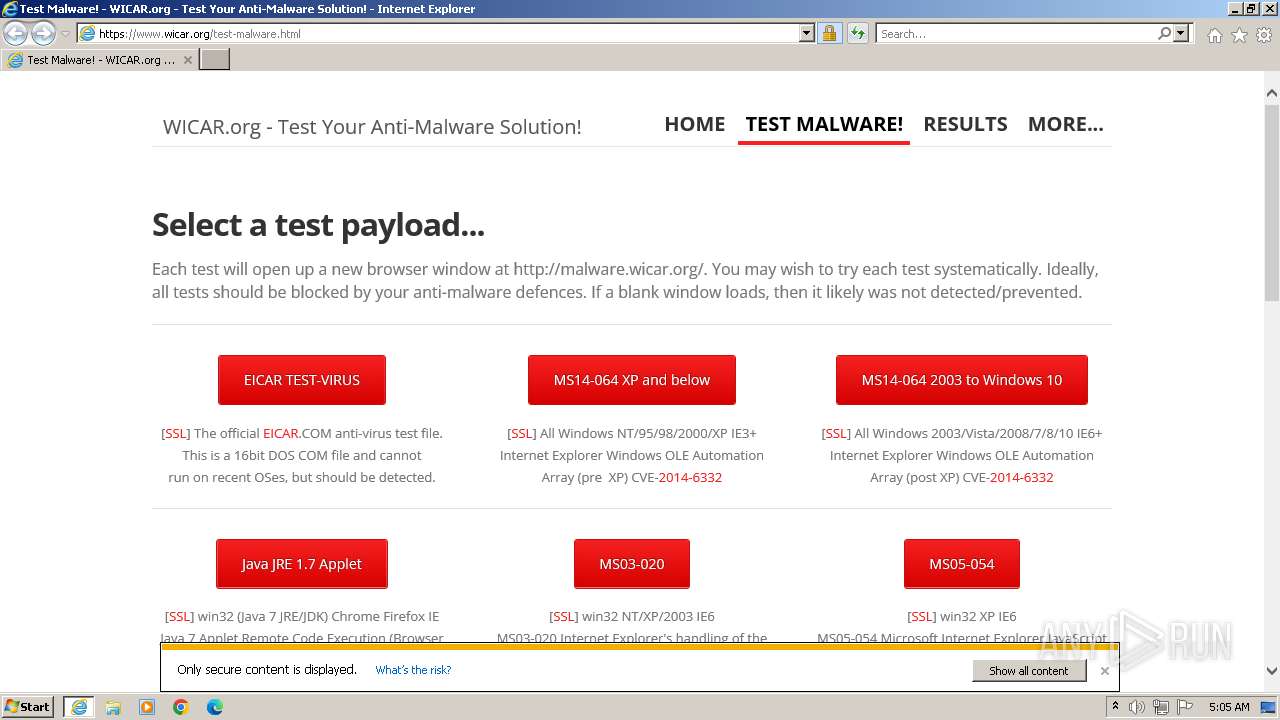
The EICAR Standard Anti-Virus Test File is detected
- iexplore.exe (PID: 1884)
- iexplore.exe (PID: 3692)
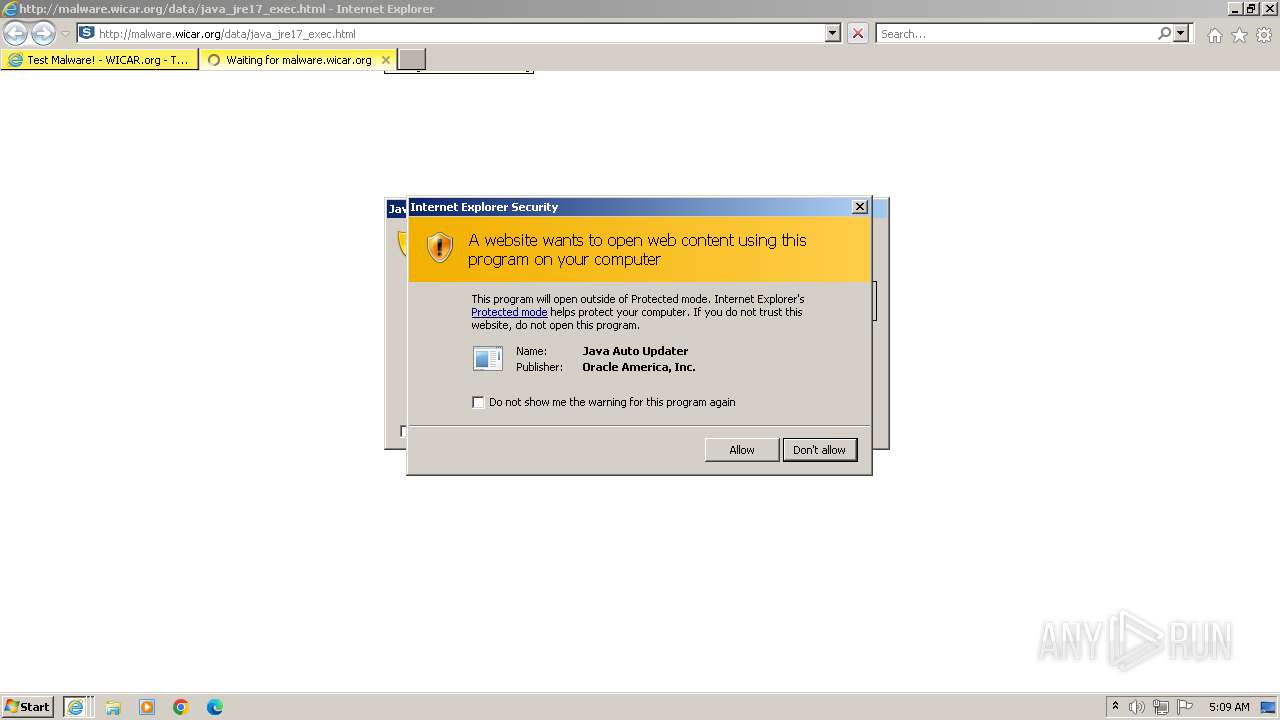
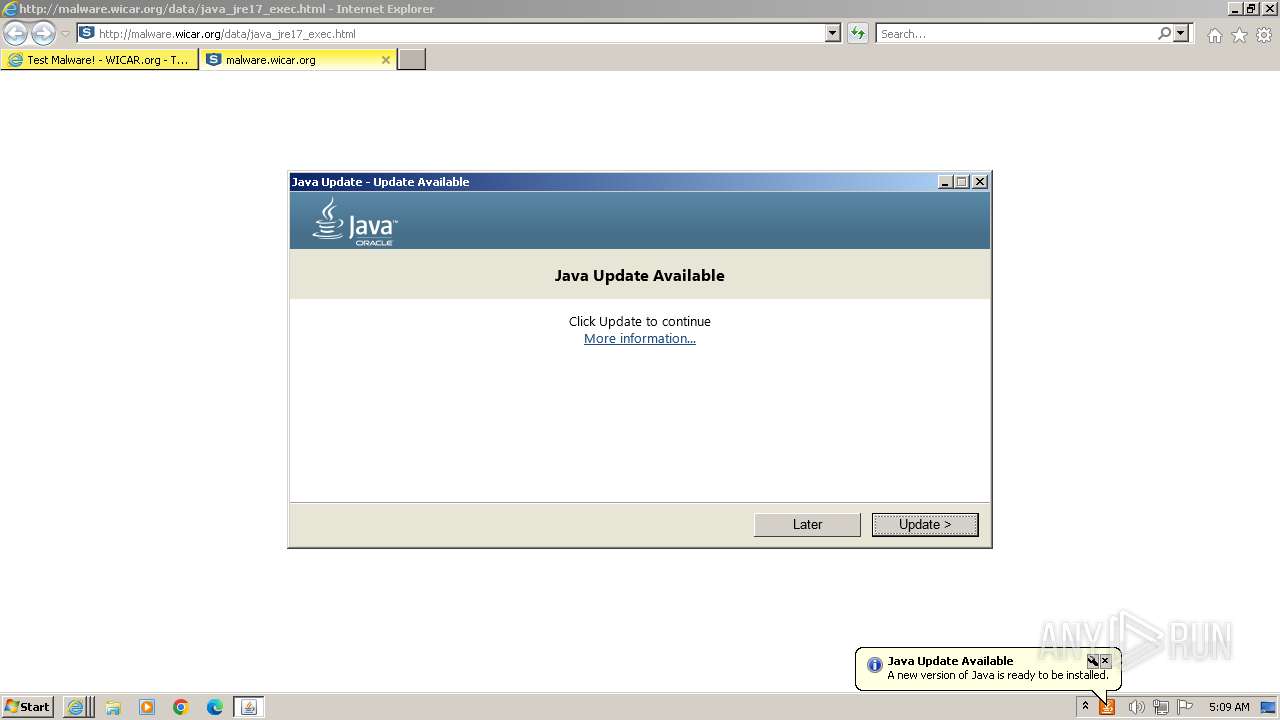
Drops the executable file immediately after the start
- jucheck.exe (PID: 3356)
- jre-8u391-windows-au.exe (PID: 3684)
- jre-8u391-windows-au.exe (PID: 2600)
- msiexec.exe (PID: 2016)
Application was dropped or rewritten from another process
- jre-8u391-windows-au.exe (PID: 2600)
- jre-8u391-windows-au.exe (PID: 3684)
- LZMA_EXE (PID: 1980)
- LZMA_EXE (PID: 3728)
Loads dropped or rewritten executable
- msiexec.exe (PID: 948)
SUSPICIOUS
Checks for Java to be installed
- jp2launcher.exe (PID: 2688)
- javaw.exe (PID: 312)
- javaw.exe (PID: 1920)
- javaw.exe (PID: 3980)
- jp2launcher.exe (PID: 1796)
- jucheck.exe (PID: 3356)
Reads security settings of Internet Explorer
- jucheck.exe (PID: 3356)
- jre-8u391-windows-au.exe (PID: 2600)
Reads the Internet Settings
- jucheck.exe (PID: 3356)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 2600)
Checks Windows Trust Settings
- jucheck.exe (PID: 3356)
- jre-8u391-windows-au.exe (PID: 2600)
- msiexec.exe (PID: 2016)
Reads Internet Explorer settings
- jucheck.exe (PID: 3356)
- jre-8u391-windows-au.exe (PID: 2600)
Reads Microsoft Outlook installation path
- jucheck.exe (PID: 3356)
- jre-8u391-windows-au.exe (PID: 2600)
Reads settings of System Certificates
- jucheck.exe (PID: 3356)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 2600)
Starts application with an unusual extension
- jre-8u391-windows-au.exe (PID: 2600)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2016)
INFO
Application launched itself
- iexplore.exe (PID: 1884)
- chrome.exe (PID: 3748)
- msiexec.exe (PID: 2016)
Checks supported languages
- jp2launcher.exe (PID: 2688)
- javaw.exe (PID: 312)
- javaw.exe (PID: 1920)
- javaw.exe (PID: 3980)
- jucheck.exe (PID: 3356)
- javaws.exe (PID: 1876)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 3684)
- jre-8u391-windows-au.exe (PID: 2600)
- LZMA_EXE (PID: 1980)
- msiexec.exe (PID: 2016)
- LZMA_EXE (PID: 3728)
- msiexec.exe (PID: 948)
The process uses the downloaded file
- iexplore.exe (PID: 1884)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3428)
Reads the computer name
- javaw.exe (PID: 312)
- javaw.exe (PID: 1920)
- javaw.exe (PID: 3980)
- jp2launcher.exe (PID: 1796)
- jucheck.exe (PID: 3356)
- jre-8u391-windows-au.exe (PID: 3684)
- jre-8u391-windows-au.exe (PID: 2600)
- msiexec.exe (PID: 2016)
- msiexec.exe (PID: 948)
Create files in a temporary directory
- javaw.exe (PID: 312)
- javaw.exe (PID: 1920)
- javaw.exe (PID: 3980)
- jucheck.exe (PID: 3356)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 3684)
Creates files in the program directory
- javaw.exe (PID: 312)
Checks proxy server information
- jucheck.exe (PID: 3356)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 2600)
Reads the machine GUID from the registry
- jucheck.exe (PID: 3356)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 2600)
- msiexec.exe (PID: 2016)
- msiexec.exe (PID: 948)
Creates files or folders in the user directory
- jucheck.exe (PID: 3356)
- jp2launcher.exe (PID: 1796)
- jre-8u391-windows-au.exe (PID: 2600)
- LZMA_EXE (PID: 1980)
- LZMA_EXE (PID: 3728)
Manual execution by a user
- chrome.exe (PID: 3748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
84
Monitored processes
37
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.271.2" "update" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | jp2launcher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1884 CREDAT:1840409 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 948 | C:\Windows\system32\MsiExec.exe -Embedding 71961B2951F4E1B68117C143DCDC42B1 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Internet Explorer\iexplore.exe" "www.wicar.org/test-malware.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1697688583" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | jp2launcher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1980 | "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_391\LZMA_EXE" d "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_391\au.msi" "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_391\msi.tmp" | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_391\LZMA_EXE | — | jre-8u391-windows-au.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2016 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2076 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: LOW Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
Total events
43 407
Read events
43 006
Write events
377
Delete events
24
Modification events
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
13
Suspicious files
134
Text files
96
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCBBA.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:66BD8185C28267537CB7D694F2A29521 | SHA256:DA02B99C5A8EC965372D01632E3F0443958499492E94EFD51FF552441C922E85 | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:0D20DB1D06F41F737E326D66069FDBFB | SHA256:993AEE52EE14B79350D294105735C6102FA70CB0C91F013B03CB9F24E9A41511 | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6666F84B2D8915EF278DCA4D78A5631E | binary | |
MD5:CC067F69F66A1EE0E732686F8E3823FF | SHA256:502F1EFA2869A966DD806DB489228D39730956A0B999042A6DC8C62BCFCDD10E | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:237C0371D8737B699D6C8E624806E37E | SHA256:5E5BB5A6ECD6D4A4EEF259E261A1EA42DA46FE30F37E7ED655B859BD07FBFD61 | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarCBBB.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6666F84B2D8915EF278DCA4D78A5631E | binary | |
MD5:545739121FF1ED8C55A39E302BFE37F6 | SHA256:4DDBEF3B8351F6E71F279C3780906EB15BB1604E5D314AFCCB56898D32BDBC53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
89
DNS requests
57
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
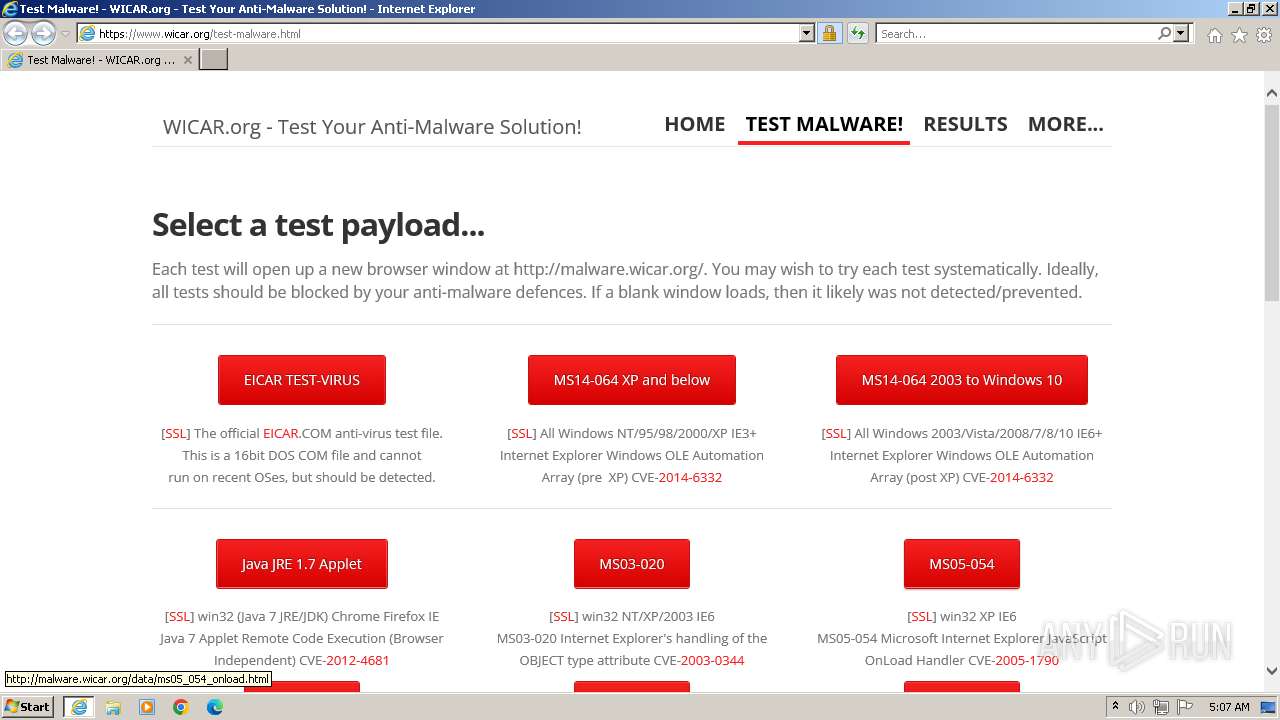
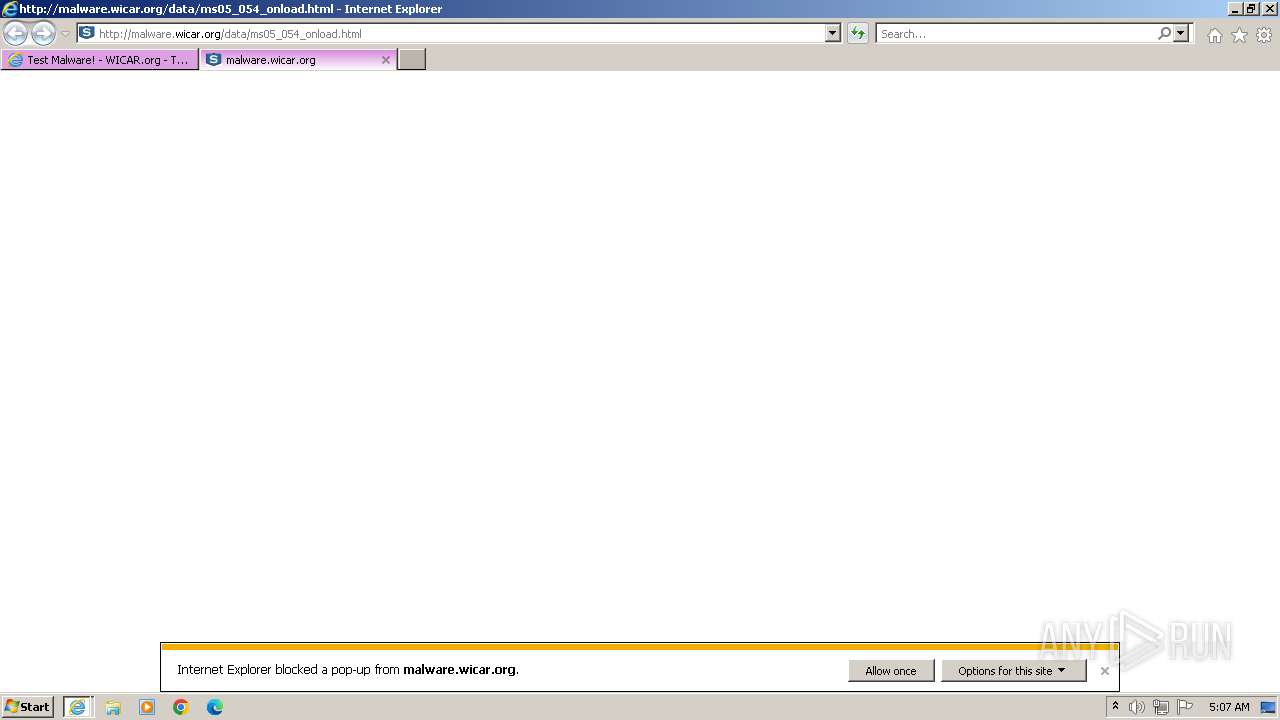
2612 | iexplore.exe | GET | 304 | 208.94.116.21:80 | http://malware.wicar.org/data/ms05_054_onload.html | unknown | — | — | unknown |
3692 | iexplore.exe | GET | 200 | 208.94.116.21:80 | http://malware.wicar.org/data/eicar.com | unknown | text | 89 b | unknown |
2828 | iexplore.exe | GET | 301 | 13.32.99.29:80 | http://w.sharethis.com/button/buttons.js | unknown | html | 167 b | unknown |
2828 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | der | 1.41 Kb | unknown |
2612 | iexplore.exe | GET | 200 | 208.94.116.21:80 | http://malware.wicar.org/data/ms05_054_onload.html | unknown | html | 5.20 Kb | unknown |
2828 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
844 | iexplore.exe | GET | 200 | 208.94.116.21:80 | http://malware.wicar.org/data/ms05_054_onload.html?p=HfYUJnIkydDkTXGdtUilxfyLkEtkuVjByjBComoudwRFhUnzpQFVbiCVsVFMnFnzSDqL</iframe | unknown | html | 5.20 Kb | unknown |
1884 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1884 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
1884 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2828 | iexplore.exe | 199.34.228.69:80 | www.wicar.org | WEEBLY | US | unknown |
2828 | iexplore.exe | 199.34.228.69:443 | www.wicar.org | WEEBLY | US | unknown |
2828 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2828 | iexplore.exe | 23.37.41.57:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2828 | iexplore.exe | 95.101.54.107:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2828 | iexplore.exe | 151.101.193.46:443 | cdn2.editmysite.com | FASTLY | US | unknown |
2828 | iexplore.exe | 13.32.99.29:80 | w.sharethis.com | AMAZON-02 | US | unknown |
2828 | iexplore.exe | 142.250.185.104:443 | www.googletagmanager.com | GOOGLE | US | unknown |
2828 | iexplore.exe | 13.32.99.29:443 | w.sharethis.com | AMAZON-02 | US | unknown |
2828 | iexplore.exe | 104.18.20.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.wicar.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
cdn2.editmysite.com |
| whitelisted |
w.sharethis.com |
| shared |
www.googletagmanager.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2612 | iexplore.exe | A Network Trojan was detected | ET EXPLOIT Metasploit Random Base CharCode JS Encoded String |
844 | iexplore.exe | A Network Trojan was detected | ET EXPLOIT Metasploit Random Base CharCode JS Encoded String |
844 | iexplore.exe | A Network Trojan was detected | ET EXPLOIT Metasploit Random Base CharCode JS Encoded String |
1796 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
1796 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
1 ETPRO signatures available at the full report