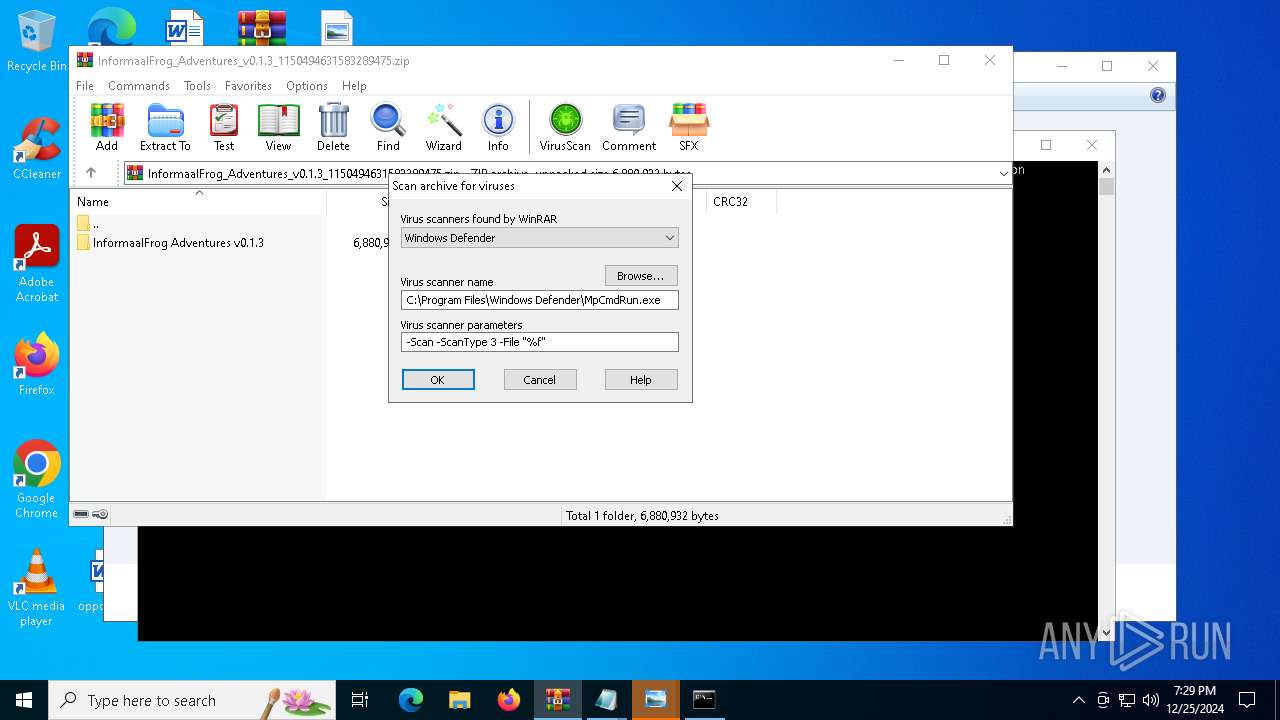
| File name: | InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip |
| Full analysis: | https://app.any.run/tasks/10d2af22-6486-4a66-b7c4-1d1f940e48ef |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2024, 19:28:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F2D916EC8E5ADFCAB7D7A6C871AD71C0 |
| SHA1: | E4C677D1958DDE76E0027B896285AD9EB48456E0 |
| SHA256: | 0047FB3093FC06FB424CF032217575CA1CFB36C59A0043B60751D6B9A78D8A36 |
| SSDEEP: | 98304:aQJEonX2XQFAeXyryNUkQqkr84MR/bP7hURTb6HZsYDOcVOxNo7xfUroCex8x4kK:ZDA2toUc3fE |
MALICIOUS
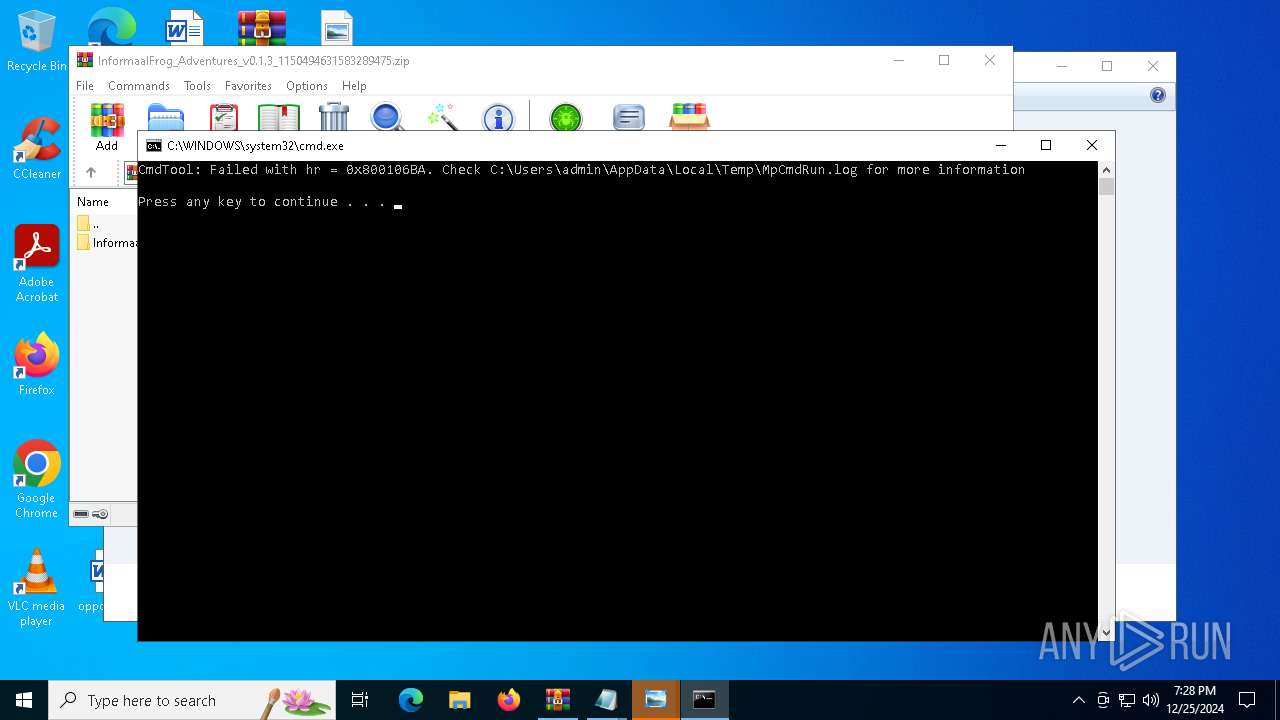
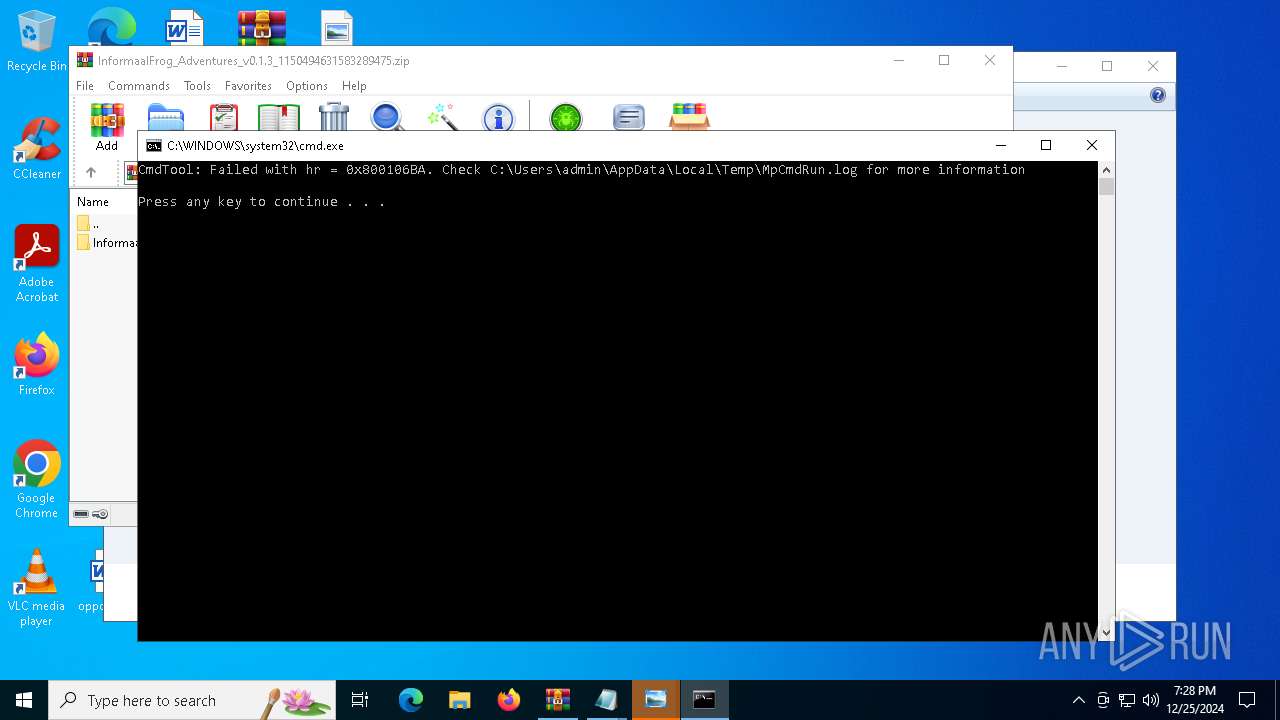
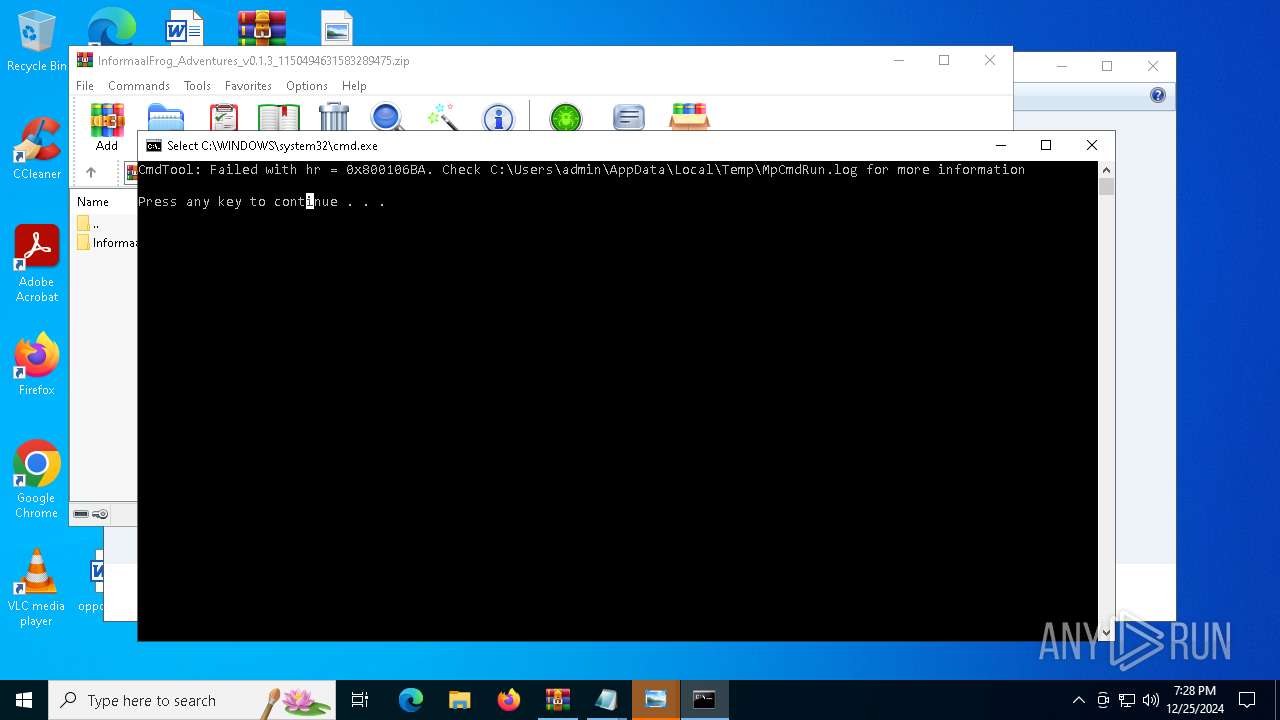
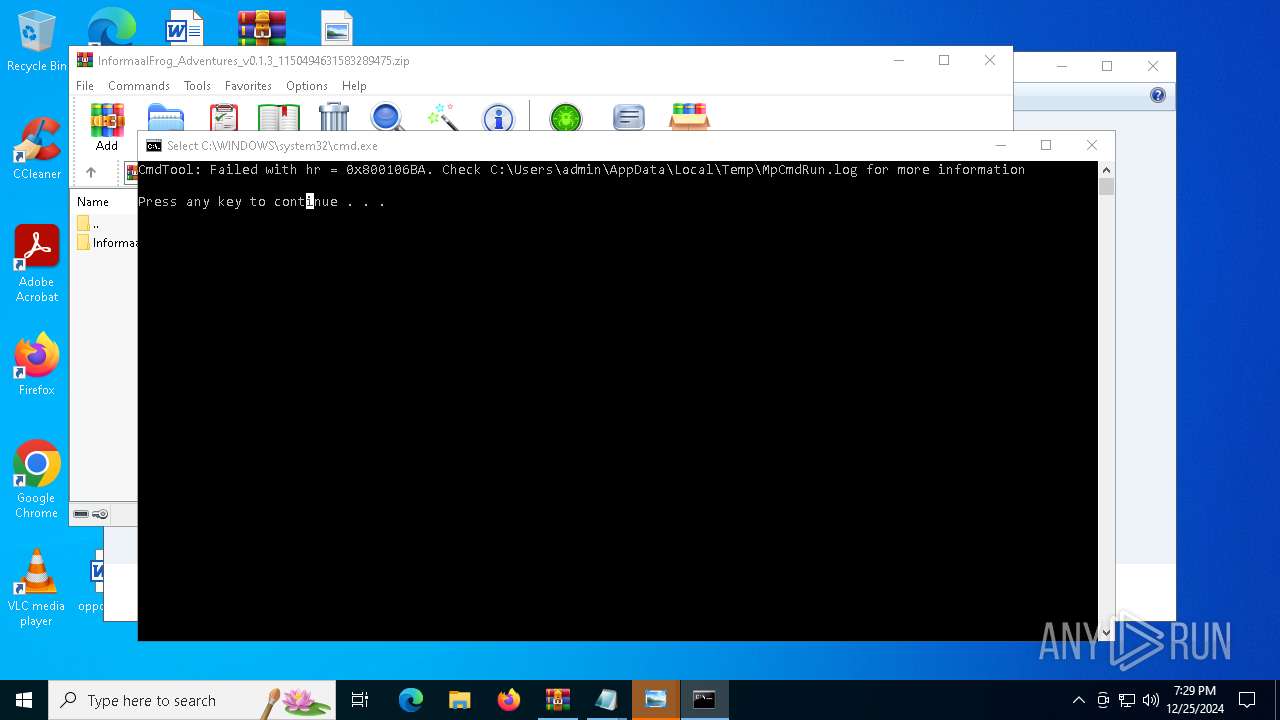
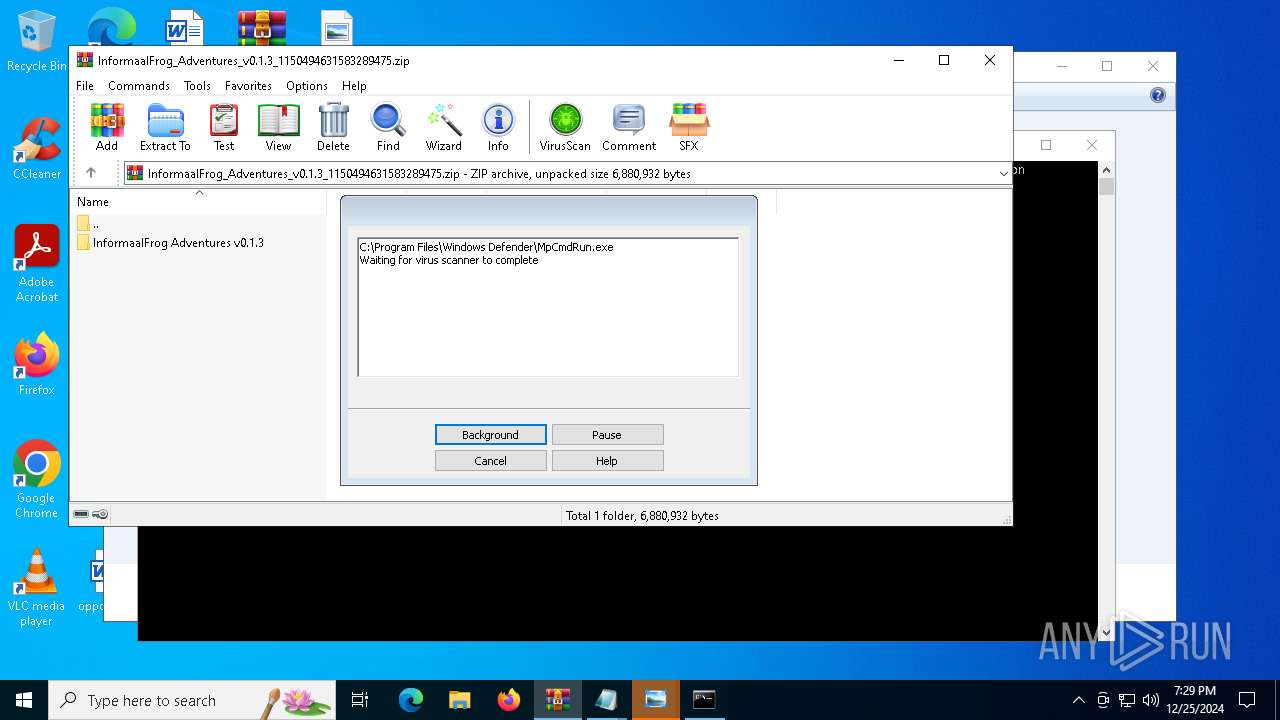
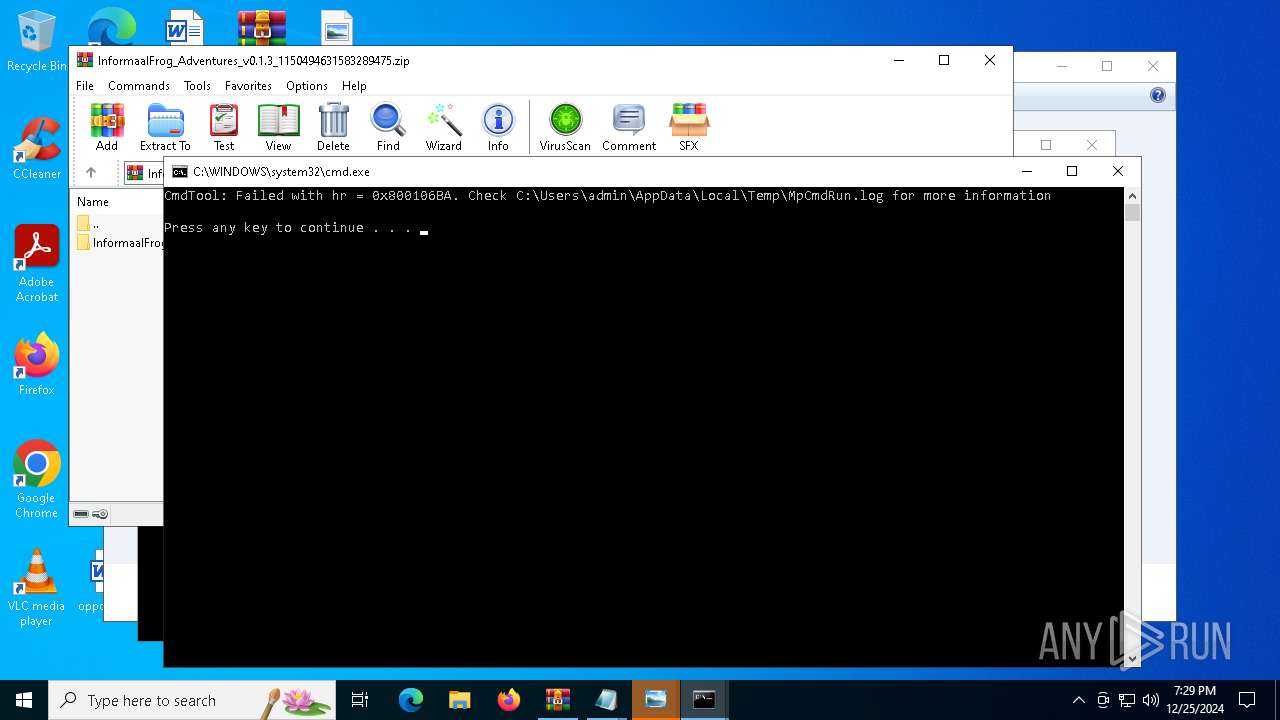
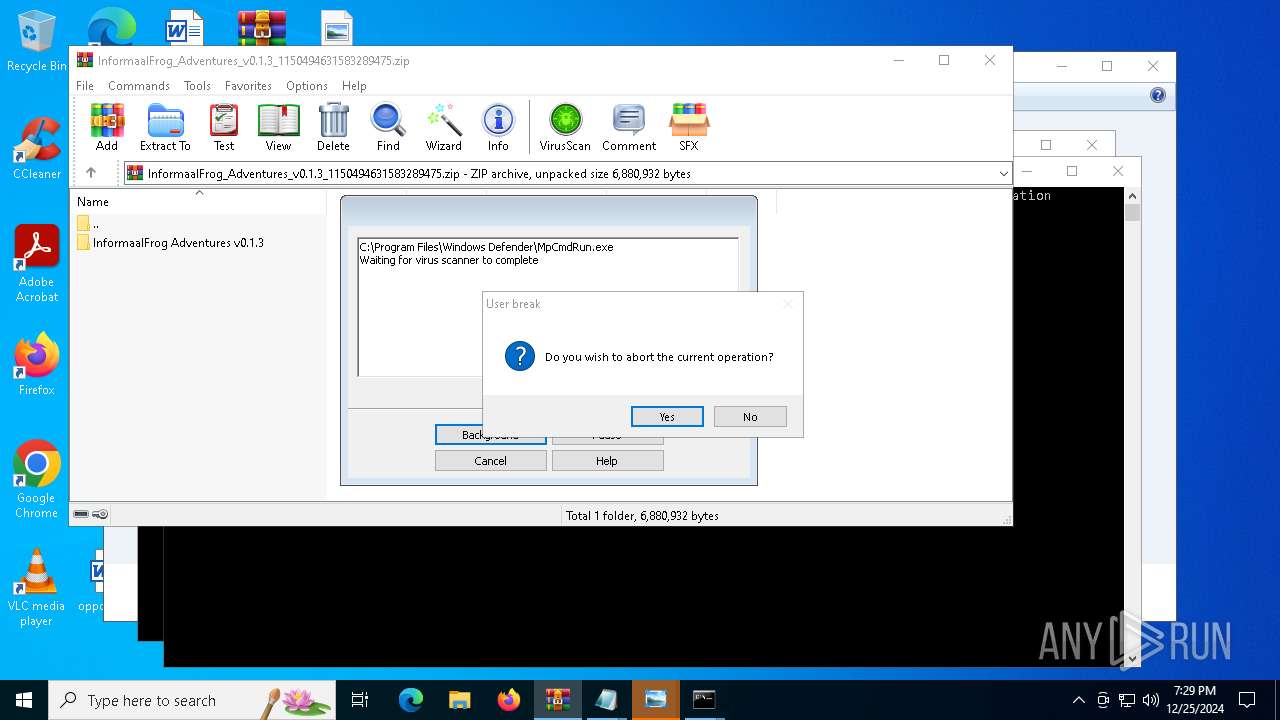
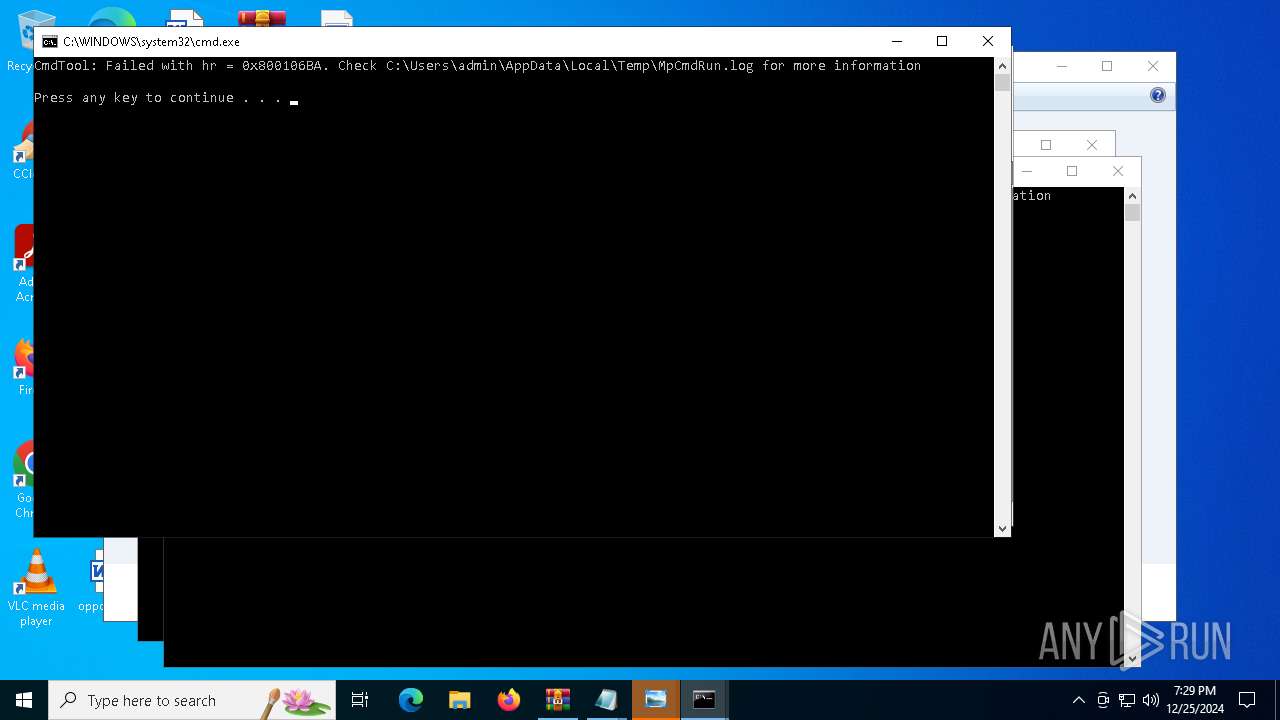
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 6156)
- MpCmdRun.exe (PID: 6332)
- MpCmdRun.exe (PID: 6468)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4504)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4504)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4504)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4504)
INFO
Manual execution by a user
- notepad.exe (PID: 3952)
- notepad.exe (PID: 5592)
- rundll32.exe (PID: 644)
- notepad.exe (PID: 5236)
- notepad.exe (PID: 5888)
- notepad.exe (PID: 4528)
- rundll32.exe (PID: 5208)
- rundll32.exe (PID: 1144)
- rundll32.exe (PID: 5720)
- rundll32.exe (PID: 3076)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5888)
- notepad.exe (PID: 4528)
- notepad.exe (PID: 3952)
- notepad.exe (PID: 5592)
- notepad.exe (PID: 5236)
The sample compiled with english language support
- WinRAR.exe (PID: 4504)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4504)
Reads the computer name
- MpCmdRun.exe (PID: 6156)
- MpCmdRun.exe (PID: 6468)
- MpCmdRun.exe (PID: 6332)
Checks supported languages
- MpCmdRun.exe (PID: 6468)
- MpCmdRun.exe (PID: 6156)
- MpCmdRun.exe (PID: 6332)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6156)
The process uses the downloaded file
- WinRAR.exe (PID: 4504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:25 18:50:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | InformaalFrog Adventures v0.1.3/Images/ |
Total processes
139
Monitored processes
20
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\mapMask.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\upgrade1.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\circleTEST1.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\uiFORMAT.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4504 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4528 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\WebhookSettings.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5208 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\circleTEST3.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\temp.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\PlanetSettings.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\upgrade8.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 068
Read events
5 057
Write events
11
Delete events
0
Modification events
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
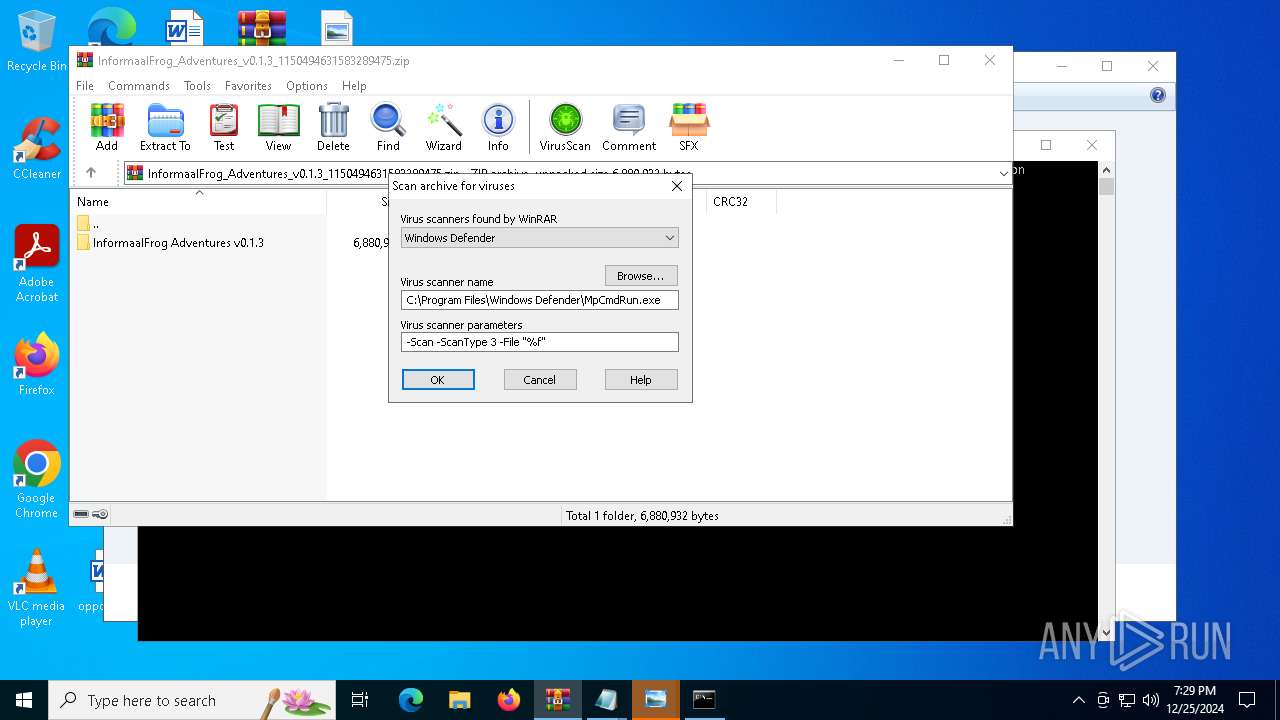
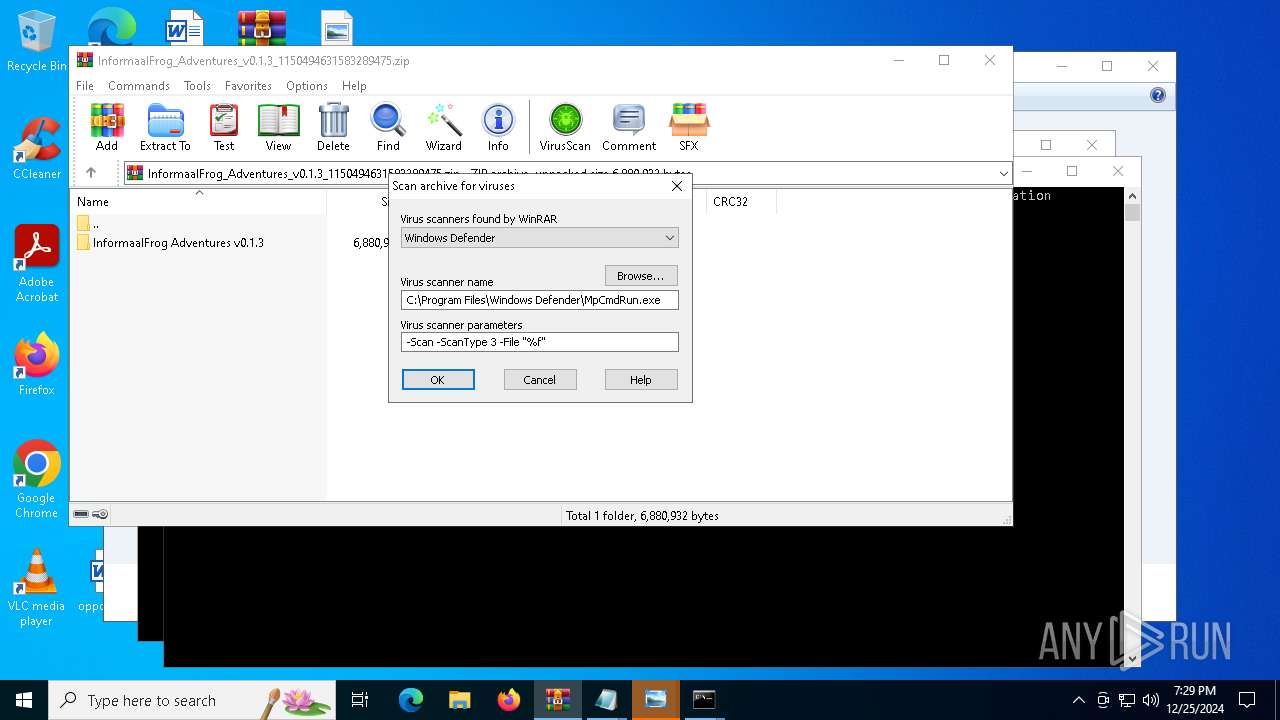
| (PID) Process: | (4504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
3
Suspicious files
0
Text files
139
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Other\send_webhook.py | text | |
MD5:ECFB77C40BA3F9C4E74AE1DC22C76570 | SHA256:9E6D2949AC78641DF1490E6AB23B3ABABE315842723B8AF47519E4D91AD2C39F | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Other\transLogo.png | image | |
MD5:D4E8593269ADD6ED08208FC28A1C4C96 | SHA256:08418CCB90B8EBBBC79667E7CB5B346E5FECC62233F522E869C1DE5968DBB73C | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Other\Logo.png | image | |
MD5:7B20F5ACC459A54E0B042B5A67A25D66 | SHA256:222130D074804EB586FEEA50E67062135D27433A0BE30D0DDF3F4DF659647829 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Reconnect\reconnectLeave.png | image | |
MD5:86BC3E7779AA33A6CDBAD06C6905D5D1 | SHA256:FD0D0F22D6B0E360EF2DA83D0A27D3418254B3B31F5EF63FF72B7A9CC679A622 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Upgrades\upgrade11.png | image | |
MD5:84BA07E5DE6F1EA0F0B8428072F6AA2D | SHA256:F0F3B3D56081F770DC438549F037F1AF56AC18ECD5ED6FCA5B0E460352B35A9D | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Upgrades\upgrade12.png | image | |
MD5:FD96AB9B349A79AC868B01363205C243 | SHA256:DC0D94CA4B013F7227AFE45530CF34DF30626AB7F0D9927E10CE90DC686879E2 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Upgrades\upgrade14.png | image | |
MD5:78242B02FC8B5A1AFA2385DFCA67CBDC | SHA256:C68684781B044AD96AFF05D79BD88D644810DC9B36B4E8E9FEB64828360CBE7E | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Upgrades\upgrade4.png | image | |
MD5:D02F160AEDAD6ADC337AB904BE98DA7E | SHA256:04AD6034947DAD8604EA79CB3E88C1120B9F178524AA6AA51E213C14BFC1ADF1 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Upgrades\upgrade2.png | image | |
MD5:57F5B122BDAD2B3A544F08278C28062D | SHA256:9F139214CBC9199CC1E970D598FBD2FBE1D023CDB7A41B9755554730EB52EC20 | |||
| 4504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4504.22296\InformaalFrog_Adventures_v0.1.3_1150494631583289475.zip\InformaalFrog Adventures v0.1.3\Images\Other\Reconnect\Reconnect.png | image | |
MD5:77720798DB5559669AF1671ADC431E7D | SHA256:7439D4CD020F3BC871A429280369BACFECCB2D87938FD193E9DA963A9AF2C4F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
244 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1856 | RUXIMICS.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
244 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1856 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
244 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1856 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.59:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
244 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1856 | RUXIMICS.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
244 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |