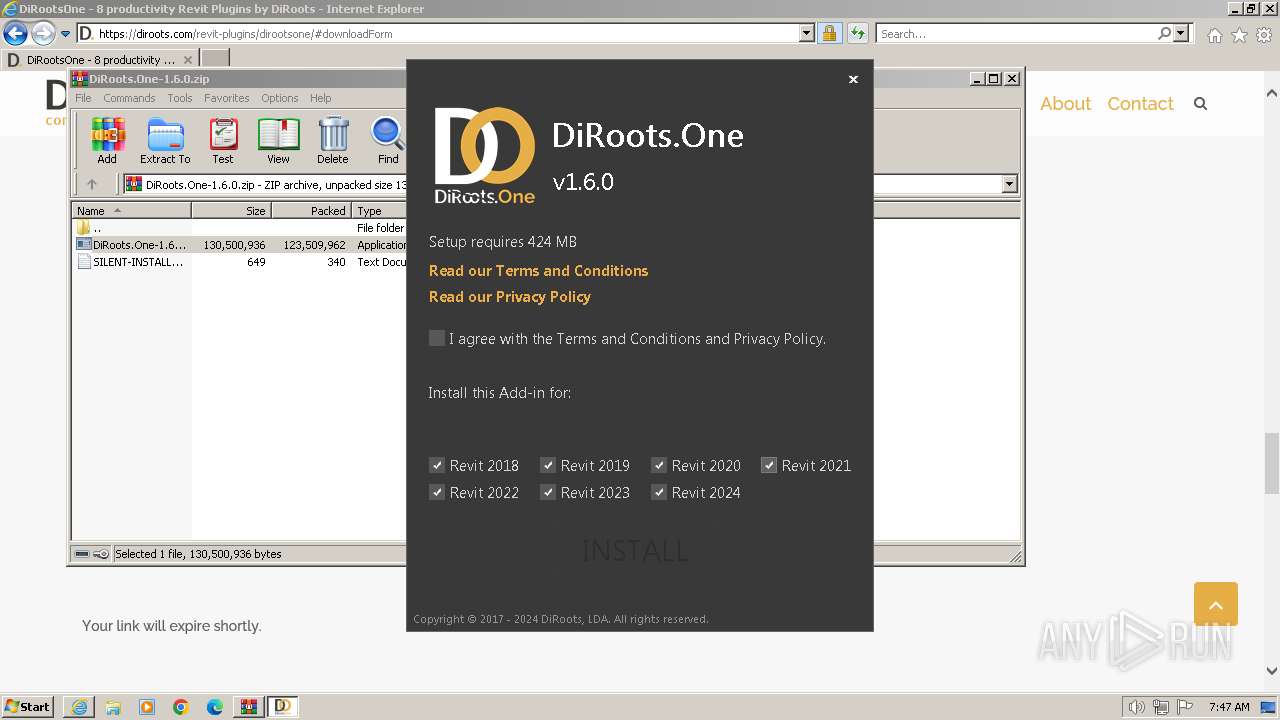
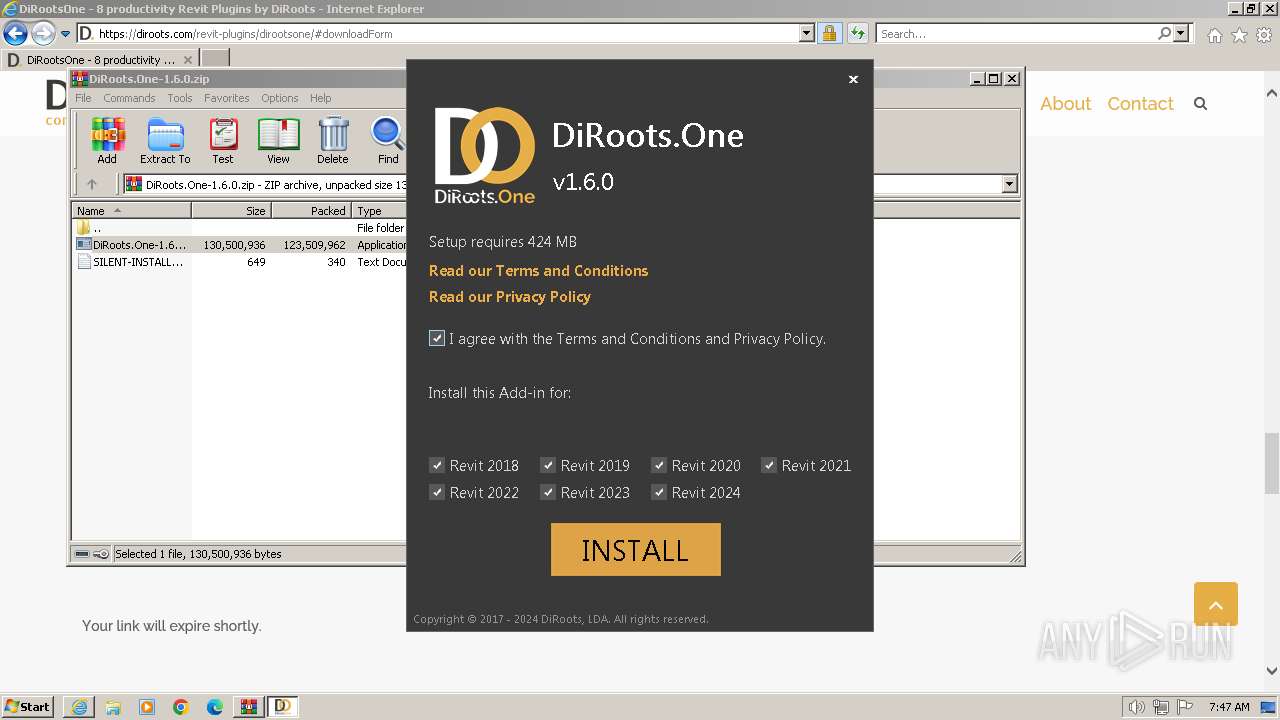
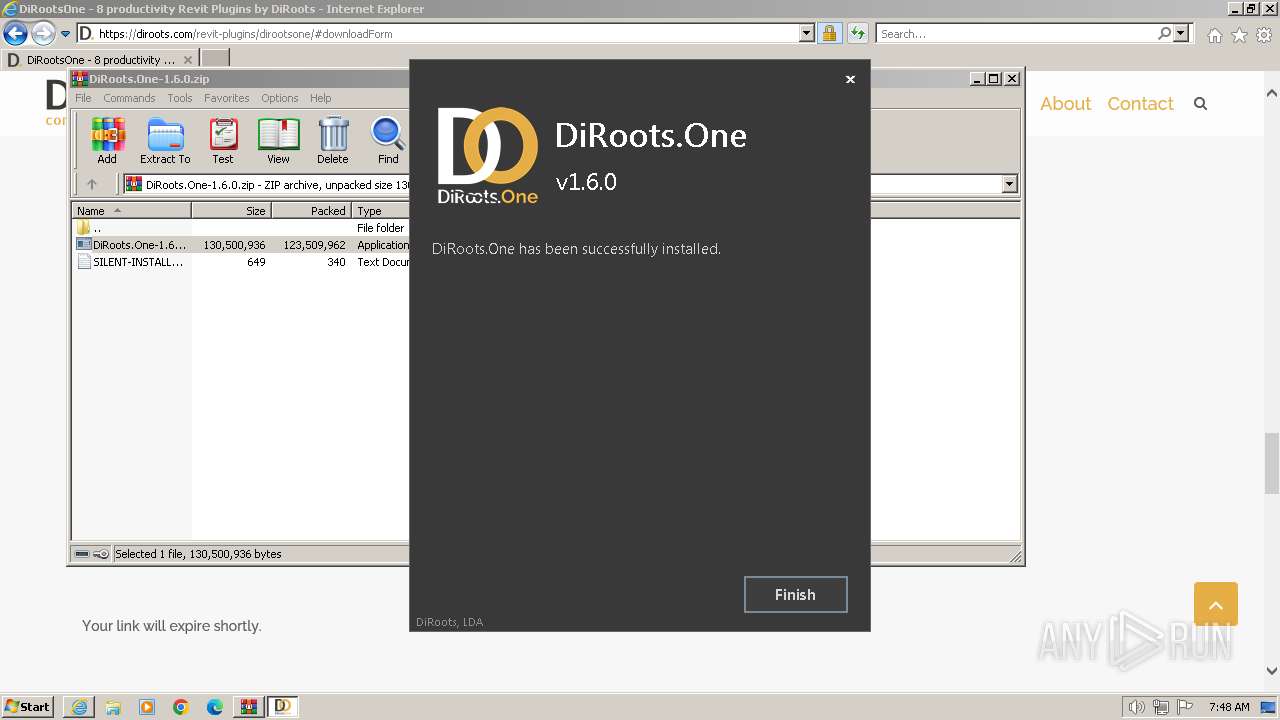
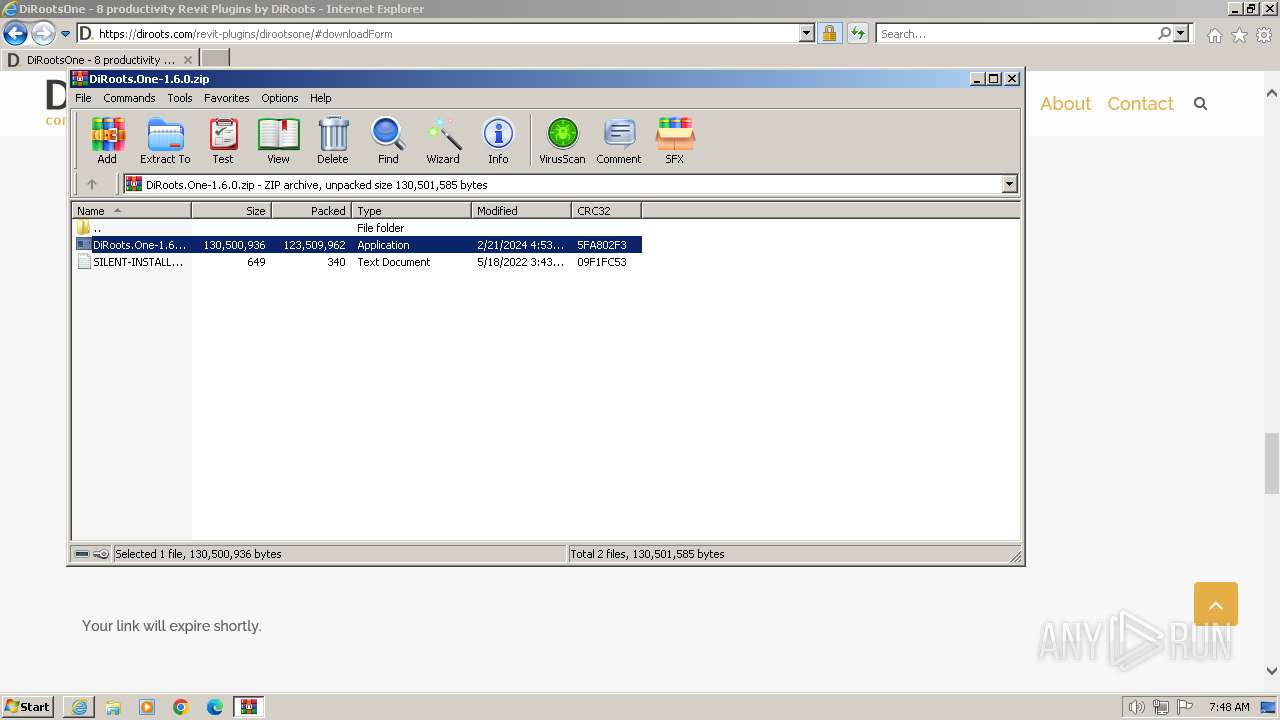
| URL: | https://diroots.com/revit-plugins/dirootsone/#downloadForm |
| Full analysis: | https://app.any.run/tasks/3c29fde1-cdce-4b53-afe9-2fb4679d4b12 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 07:44:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4853D11A629D3F9FA58E0A99FAC786D8 |
| SHA1: | 66088174CF0BC7C96769C062811619A8A000927F |
| SHA256: | 0040CDA48525D05F22FF0B11AF992649E630E52C63F72F4DEBF4DF48CF64D32D |
| SSDEEP: | 3:N8UaKmXGvNqXJNJ:2UnxvNqfJ |
MALICIOUS
Drops the executable file immediately after the start
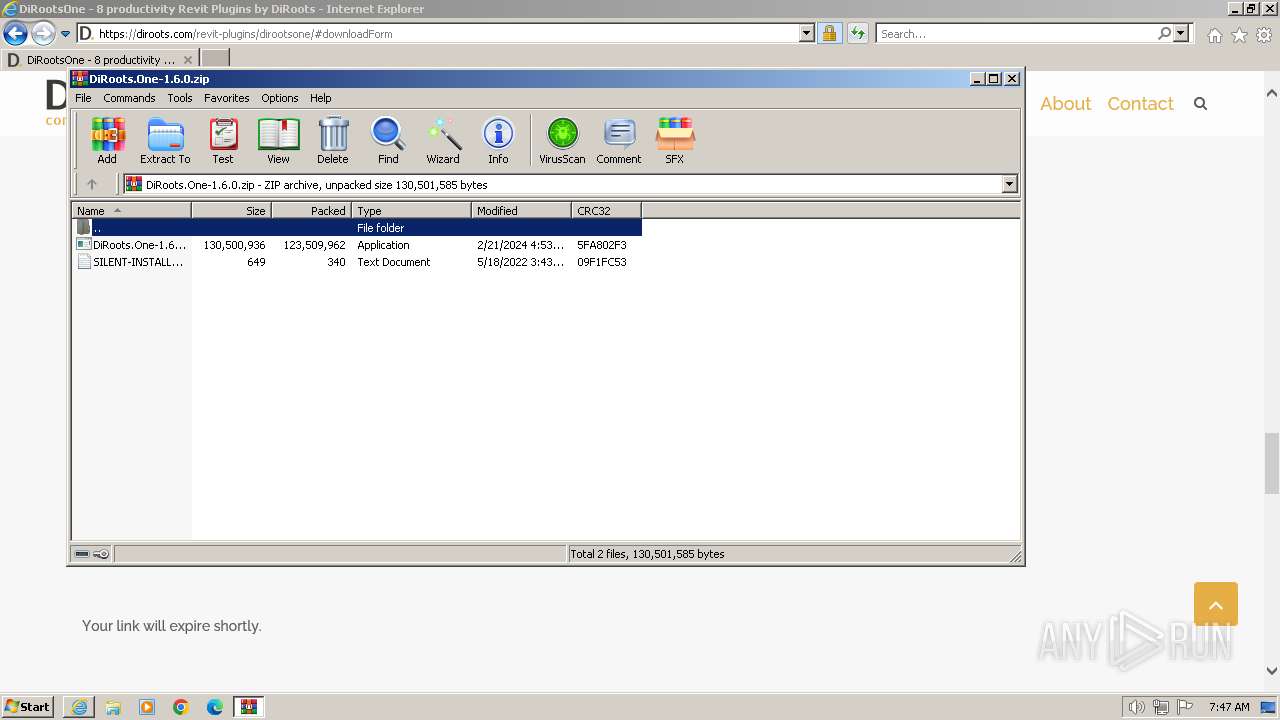
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2576)
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Checks Windows Trust Settings
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Reads settings of System Certificates
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Reads the Windows owner or organization settings
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Executable content was dropped or overwritten
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Reads Internet Explorer settings
- DiRoots.One-1.6.0.exe (PID: 448)
Reads the Internet Settings
- DiRoots.One-1.6.0.exe (PID: 448)
Application launched itself
- DiRoots.One-1.6.0.exe (PID: 448)
Executes as Windows Service
- VSSVC.exe (PID: 2656)
INFO
Modifies the phishing filter of IE
- iexplore.exe (PID: 1384)
Application launched itself
- iexplore.exe (PID: 1384)
The process uses the downloaded file
- WinRAR.exe (PID: 2576)
- iexplore.exe (PID: 1384)
Reads the computer name
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Reads the machine GUID from the registry
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Checks supported languages
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Reads Environment values
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Creates files in the program directory
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Reads the software policy settings
- DiRoots.One-1.6.0.exe (PID: 448)
- DiRoots.One-1.6.0.exe (PID: 2956)
Create files in a temporary directory
- DiRoots.One-1.6.0.exe (PID: 448)
Manual execution by a user
- explorer.exe (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
59
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe | WinRAR.exe | ||||||||||||
User: admin Company: DiRoots, LDA Integrity Level: HIGH Description: DiRoots.One Installer Exit code: 0 Version: 1.6.0 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://diroots.com/revit-plugins/dirootsone/#downloadForm" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2576 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\DiRoots.One-1.6.0.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2656 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe" /i "C:\ProgramData\DiRoots, LDA\DiRoots.One 1.6.0\install\DiRoots.One-1.6.0.msi" AI_EUIMSI=1 APPDIR="C:\Program Files\DiRoots, LDA\DiRoots.One" SECONDSEQUENCE="1" CLIENTPROCESSID="448" CHAINERUIPROCESSID="448Chainer" ACTION="INSTALL" EXECUTEACTION="INSTALL" CLIENTUILEVEL="0" ADDLOCAL="MainFeature,DiFeature_2018,DiFeature_2019,DiFeature_2020,DiFeature_2024,DiFeature_2021,DiFeature_2023,DiFeature_2022" AGREE_CHECKBOX="Yes" PRIMARYFOLDER="APPDIR" ROOTDRIVE="C:\" AI_SETUPEXEPATH="C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\" EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1708672713 " AI_SETUPEXEPATH_ORIGINAL="C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe" TARGETDIR="C:\" AI_INSTALL="1" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe | DiRoots.One-1.6.0.exe | ||||||||||||
User: admin Company: DiRoots, LDA Integrity Level: HIGH Description: DiRoots.One Installer Exit code: 0 Version: 1.6.0 Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.45247\DiRoots.One-1.6.0.exe | — | WinRAR.exe | |||||||||||
User: admin Company: DiRoots, LDA Integrity Level: MEDIUM Description: DiRoots.One Installer Exit code: 3221226540 Version: 1.6.0 Modules
| |||||||||||||||
| 3392 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1384 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
42 392
Read events
41 953
Write events
390
Delete events
49
Modification events
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 710264880 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090220 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090220 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
17
Suspicious files
38
Text files
234
Unknown types
46
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:8797729D14A2E7D63859BE1CF8BEB5F5 | SHA256:57360788459D813523DBBDD966408C9E10725483EB1C985B7AADAE6D3D182847 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\dirootsone[1].htm | html | |
MD5:FE773B4F40D7E13C17F7805F48B2EC6C | SHA256:6B7B73124C314AAAF2AAE8BD053AE79A7D14A9C31AAA7CE0900C2DF6DADD458E | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery-migrate.min[1].js | text | |
MD5:9FFEB32E2D9EFBF8F70CAABDED242267 | SHA256:5274F11E6FB32AE0CF2DFB9F8043272865C397A7C4223B4CFA7D50EA52FBDE89 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:49A0FA8988C9AD73DF3F0489747EED03 | SHA256:014EA4D9F776B384C1BCB5846453ACF340598289DB5C5A9DE4430FF09771D8E5 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\311823F8DC8E77451D475A57C39369AE_51C3A05DD5A2C07A22F753210DB2A560 | binary | |
MD5:9F30CE4B74A15ECCD5BB6012F7B535FD | SHA256:DD26E352501DE143617B3DBDC5E9A6005FBA6EE017F9A0158FF049911A4E9C8D | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\virtual-scroll.min[1].js | text | |
MD5:C02ED13C67EC5A4C9E67790223F1210B | SHA256:AFCDD184F8541A698CE191543E8B1259B9E2F8188DC08480D6EFA517E7CDA0F3 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\311823F8DC8E77451D475A57C39369AE_51C3A05DD5A2C07A22F753210DB2A560 | binary | |
MD5:3B011A4EC92F197D10C31A8F61B30D51 | SHA256:6F37F20CCBF9C4622EE1C76E705C534A3ABF5770A113A0C2C8A70E7E487AAF41 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\hammer.min[1].js | text | |
MD5:15065981497259D972918A646AB771E0 | SHA256:8A1B58D624EEB47E9E3073531A5D364E41A2E7853C052873A79917F97DD0BB44 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\autoptimize_single_f89263c0c2f24398a1df52eead69f5f8[1].js | text | |
MD5:819BD98310ED4C6DD18D65E707A8C983 | SHA256:37F75916DC83887D0BDD7C9790C5EBEBF25B8B77614888E7BB356CEBC7C7CC0B | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\autoptimize_single_b400f6e5c15ed72b7e9f85850d9b4308[1].js | text | |
MD5:F4E4652C193F39943F860E69D800E705 | SHA256:54600C948C5C0C09ADCCF1A2D07865A46E0556B5740A1699203110DB711BA26D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
78
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3536 | iexplore.exe | GET | 304 | 23.32.238.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c70275e956f241e7 | unknown | — | — | unknown |
3536 | iexplore.exe | GET | 304 | 23.32.238.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
3536 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | binary | 2.01 Kb | unknown |
3536 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDCsSZm9KrWgg%3D%3D | unknown | binary | 2.06 Kb | unknown |
3536 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3536 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3536 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH1ZfRmkcbmIEJt1GKpWSOU%3D | unknown | binary | 471 b | unknown |
3536 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCRs%2Fkp3S0EjBKeXx2SMJsz | unknown | binary | 472 b | unknown |
3536 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFXRaa0xCYMwCsaHL3qLKxQ%3D | unknown | binary | 471 b | unknown |
3536 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDWcu1vhm%2F7Dgq%2BMnSH3EBn | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3536 | iexplore.exe | 192.124.249.78:443 | diroots.com | SUCURI-SEC | US | unknown |
3536 | iexplore.exe | 23.32.238.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3536 | iexplore.exe | 192.124.249.36:80 | ocsp.godaddy.com | SUCURI-SEC | US | unknown |
3536 | iexplore.exe | 142.250.181.238:443 | www.googleoptimize.com | GOOGLE | US | whitelisted |
3536 | iexplore.exe | 172.217.16.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3536 | iexplore.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
3536 | iexplore.exe | 142.250.186.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
diroots.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
www.googleoptimize.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
snap.licdn.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |