| File name: | en-us_windows_11_consumer_editions_version_23h2_updated_jan_2025_x64_dvd_f078c50e.iso.cmd |
| Full analysis: | https://app.any.run/tasks/7152ee55-e864-4366-8ea1-ab1df2892ef5 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 10:41:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | C3506B665EF2C2664CD2277EC8C8AAFE |
| SHA1: | 0213E8602BF8E7D901914B0ADC5EB1E1E93D3E93 |
| SHA256: | 002BB776120A094252EEF3C73F1FAD207EDFF754D8155EEDF3AB5D2B38222981 |
| SSDEEP: | 48:z/sWwWfC0Uymve1bIJOepRSY0y1Wg7rwekEny3fRvbuLL8Ui:z7wWfpukleSY06Xwe/yvluLIUi |
MALICIOUS
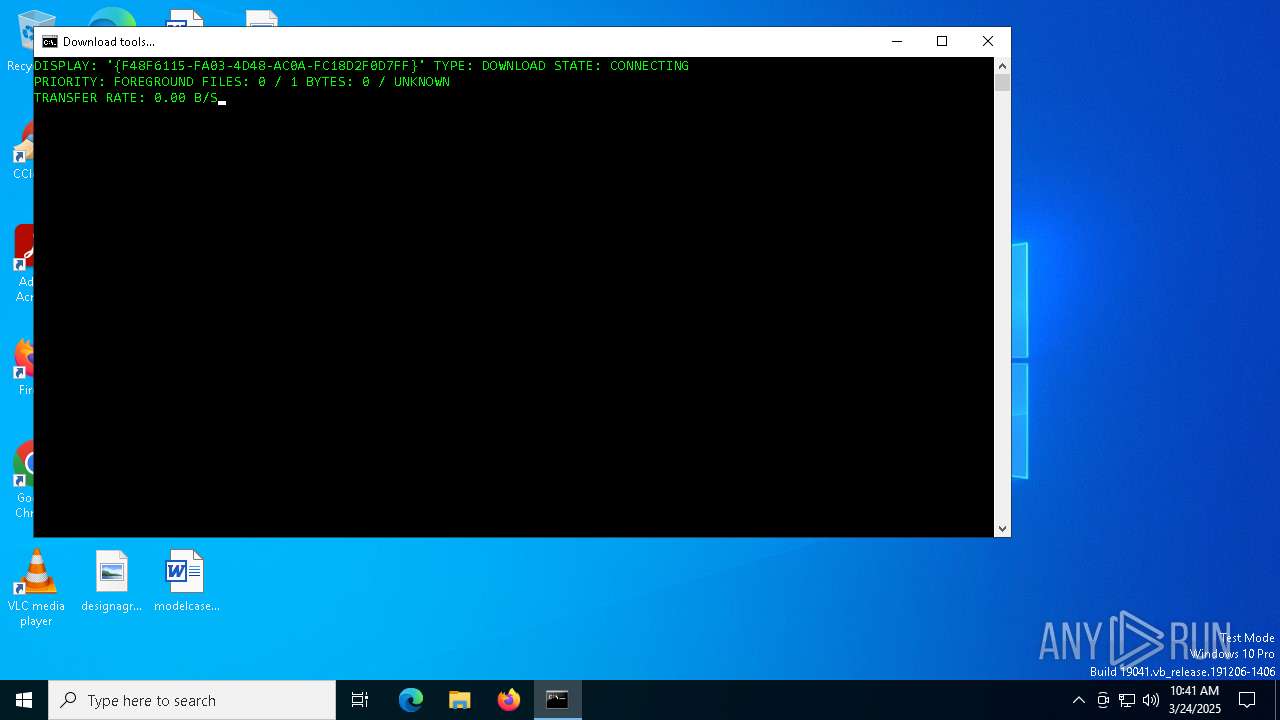
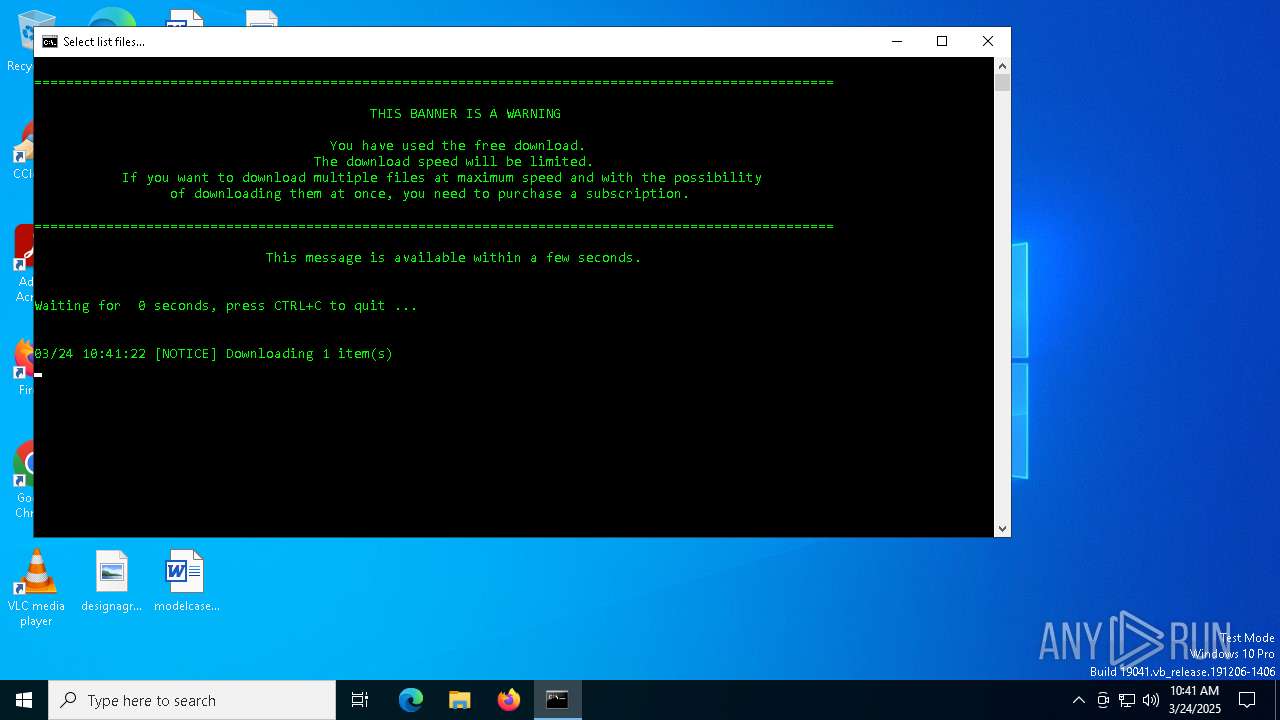
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 5972)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5972)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7184)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5972)
Drops 7-zip archiver for unpacking
- expand.exe (PID: 8120)
Executable content was dropped or overwritten
- expand.exe (PID: 8120)
The executable file from the user directory is run by the CMD process
- aria2c.exe (PID: 4608)
Application launched itself
- cmd.exe (PID: 5972)
INFO
Uses BITSADMIN.EXE
- cmd.exe (PID: 7184)
Reads the machine GUID from the registry
- expand.exe (PID: 8120)
Create files in a temporary directory
- aria2c.exe (PID: 4608)
- expand.exe (PID: 8120)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 1532)
Checks supported languages
- expand.exe (PID: 8120)
The sample compiled with english language support
- expand.exe (PID: 8120)
Checks operating system version
- cmd.exe (PID: 5972)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1532)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4944)
- BackgroundTransferHost.exe (PID: 1532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
156
Monitored processes
20
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | C:\WINDOWS\system32\cmd.exe /c type "C:\Users\admin\AppData\Local\Temp\16212\list.txt" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | "C:\Users\admin\AppData\Local\Temp\bin\aria2c.exe" -x1 -s1 -d"C:\Users\admin\AppData\Local\Temp\16212" -o"list.txt" "https://files.rg-adguard.net/file/5bdd7dfb-55d0-930c-dc3d-296b106a9aa1/list" --disable-ipv6 | C:\Users\admin\AppData\Local\Temp\bin\aria2c.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\system32\cmd.exe /c type "C:\Users\admin\AppData\Local\Temp\16212\list.txt" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
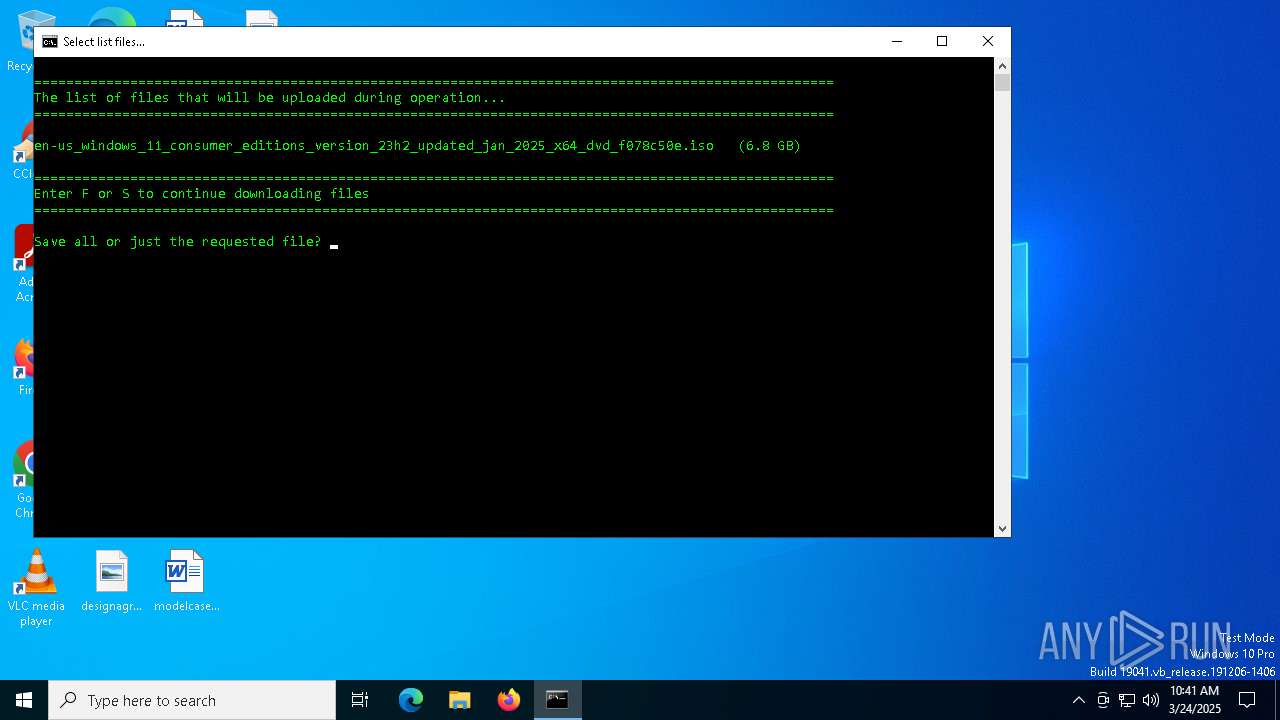
| 5392 | CHOICE /c fs /n /m "Save all or just the requested file?" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5972 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\en-us_windows_11_consumer_editions_version_23h2_updated_jan_2025_x64_dvd_f078c50e.iso.cmd.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7184 | C:\WINDOWS\system32\cmd.exe /c bitsadmin.exe /CREATE /DOWNLOAD "Download Tools" | findstr "Created job" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7200 | bitsadmin.exe /CREATE /DOWNLOAD "Download Tools" | C:\Windows\System32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.8.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 163
Read events
2 148
Write events
15
Delete events
0
Modification events
| (PID) Process: | (4944) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4944) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4944) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1532) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1532) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1532) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7780) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7780) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7780) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8060) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
8
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\0e32f44c-2922-41b2-830d-bec97aaee1db.down_data | — | |
MD5:— | SHA256:— | |||
| 8120 | expand.exe | C:\Users\admin\AppData\Local\Temp\bin\7z.exe | executable | |
MD5:9A1DD1D96481D61934DCC2D568971D06 | SHA256:8CEBB25E240DB3B6986FCAED6BC0B900FA09DAD763A56FB71273529266C5C525 | |||
| 8120 | expand.exe | C:\Users\admin\AppData\Local\Temp\bin\smv.exe | executable | |
MD5:F3C45AE821B803E521B9E14B4B87EB1A | SHA256:93FBA2D50921565BCF283075BB3B8195F2B9B10719EC5123FBF06EA596A782B4 | |||
| 1532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:ED43BC5747817645AC7B39D87F1C3EF4 | SHA256:F90E8B06011505AE3C0C16884410170C7AF734B40127F9998BF27E2C47F2F312 | |||
| 8120 | expand.exe | C:\Users\admin\AppData\Local\Temp\bin\7z.dll | executable | |
MD5:4E35A902CA8ED1C3D4551B1A470C4655 | SHA256:77222E81CB7004E8C3E077AADA02B555A3D38FB05B50C64AFD36CA230A8FD5B9 | |||
| 1532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 4608 | aria2c.exe | C:\Users\admin\AppData\Local\Temp\16212\list.txt | text | |
MD5:D5BBFE263DB73512322AE3700C6C817A | SHA256:5E86909D401809A2FB79A67B926B61E84CA899B81BF12EC27CC767680507E330 | |||
| 8120 | expand.exe | C:\Users\admin\AppData\Local\Temp\bin\aria2c.exe | executable | |
MD5:8C71B86BF407C05BAF11E8D296B9C8B8 | SHA256:BE2099C214F63A3CB4954B09A0BECD6E2E34660B886D4C898D260FEBFE9D70C2 | |||
| 8120 | expand.exe | C:\Users\admin\AppData\Local\Temp\bin\7z.cmd | text | |
MD5:5DD57ED7AFC26FFC598AF730B224CF52 | SHA256:25C5A15960D922036F863879914C891A93830E773630F6E7EA4FCE35398AA440 | |||
| 8120 | expand.exe | C:\Users\admin\AppData\Local\Temp\bin\smv.cmd | text | |
MD5:4DD25E07C4506DB89FE59962235E5CD4 | SHA256:732B5B32C38AB6BADDAB060B2DF2BF21A75F97E8B9F7055DCDB245D10FE74A90 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.41.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.41.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7620 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5344 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5344 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1532 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.53.41.90:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.41.90:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3812 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
files.rg-adguard.net |
| whitelisted |
arc.msn.com |
| whitelisted |
c.pki.goog |
| whitelisted |
www.bing.com |
| whitelisted |