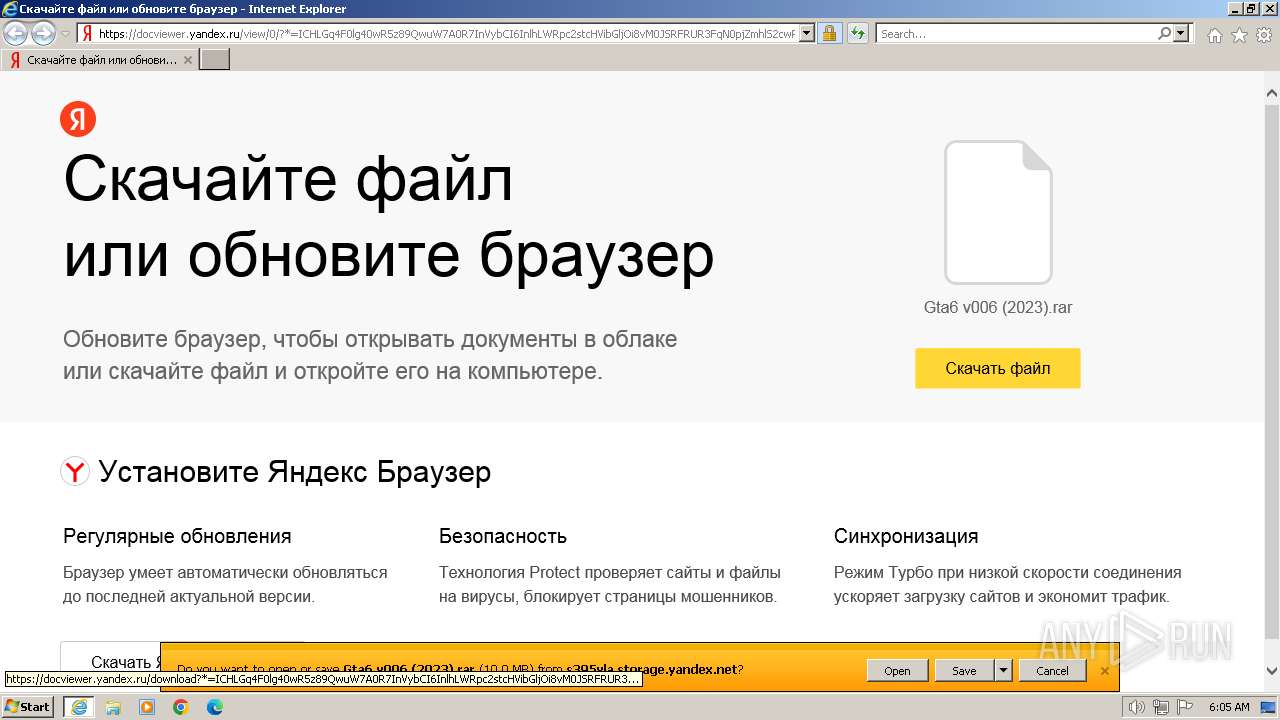
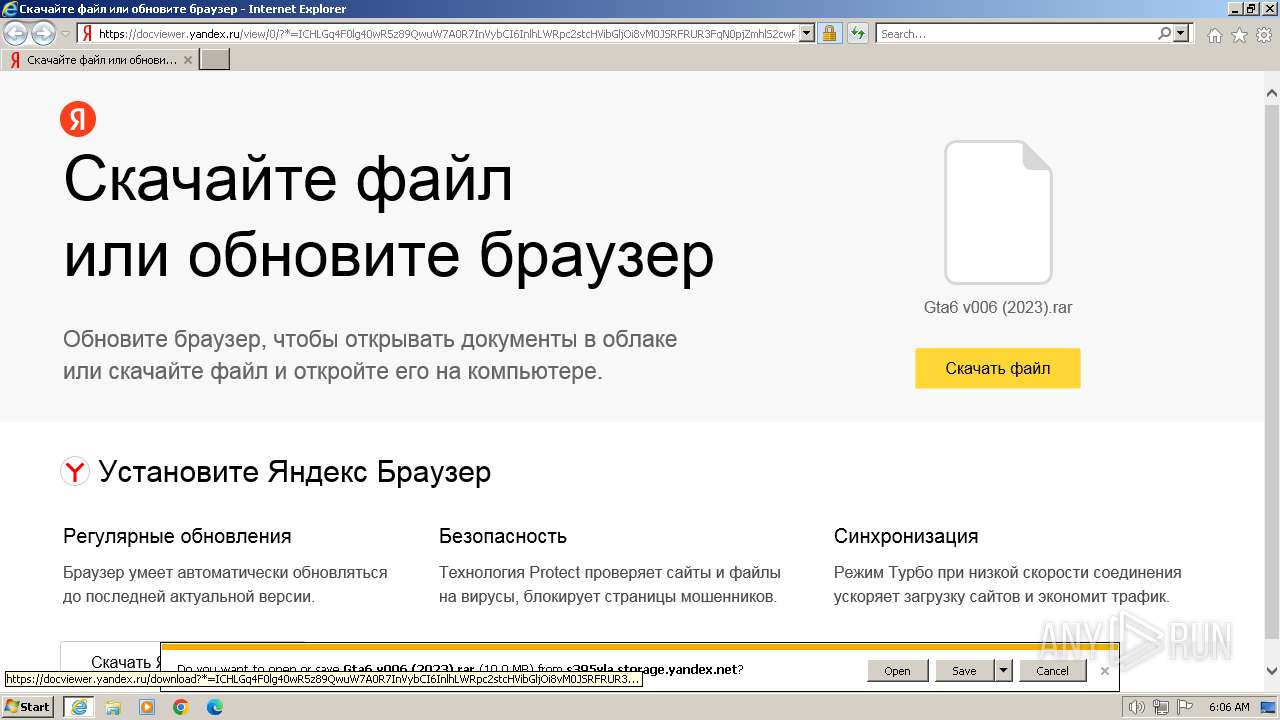
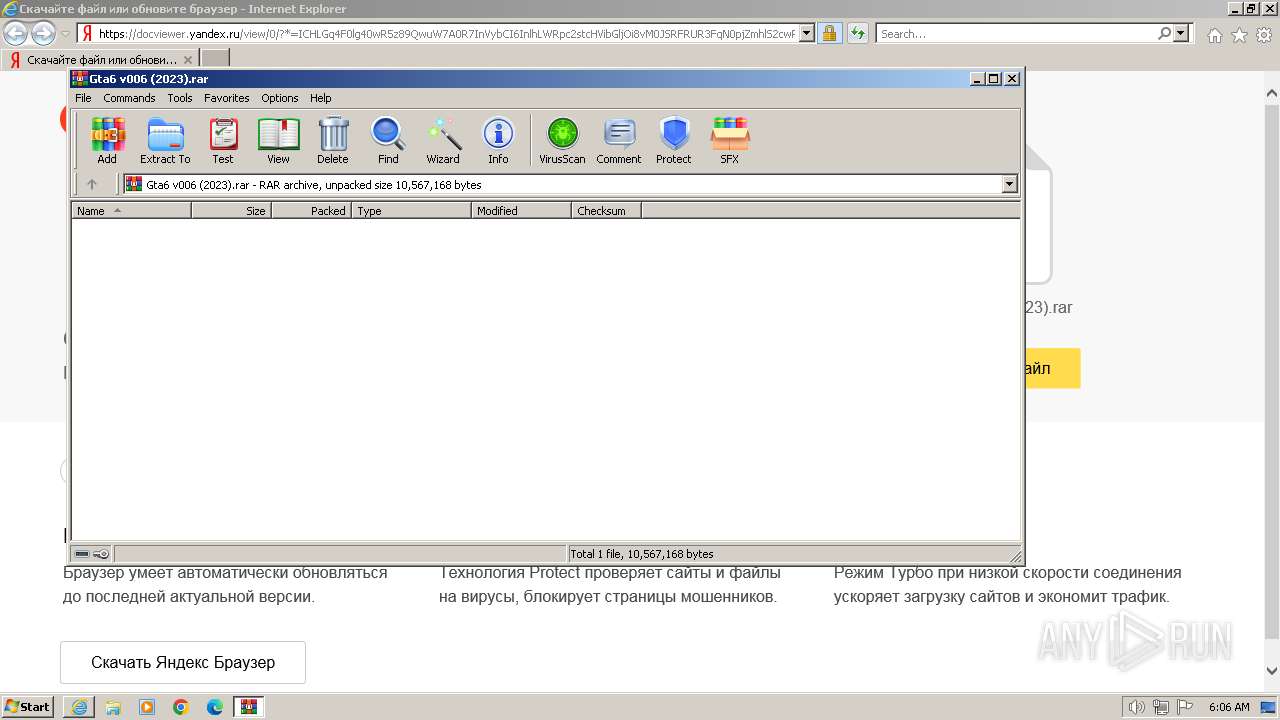
| URL: | https://docviewer.yandex.ru/view/0/?*=ICHLGq4F0lg40wR5z89QwuW7A0R7InVybCI6InlhLWRpc2stcHVibGljOi8vM0JSRFRUR3FqN0pjZmhlS2cwRzJNVVBGNWVwV2JEU2g5b3Ird0dsMzZrZStjb3JhaXUzQTZqd29lb25YaWxBd3EvSjZicG1SeU9Kb25UM1ZvWG5EYWc9PTovR3RhNiB2MDA2ICgyMDIzKS5yYXIiLCJ0aXRsZSI6Ikd0YTYgdjAwNiAoMjAyMykucmFyIiwibm9pZnJhbWUiOmZhbHNlLCJ1aWQiOiIwIiwidHMiOjE3MDMzOTc4Njk1NjMsInl1IjoiOTE3OTIzNjI4MTcwMjk5ODU5OSJ9 |
| Full analysis: | https://app.any.run/tasks/05745b60-ed9a-4edf-814c-802e254216d1 |
| Verdict: | Malicious activity |
| Analysis date: | December 24, 2023, 06:05:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6D6C33C587ECDE5246FC81B314706E7D |
| SHA1: | D87042F17E775A3848818FE2305CEDB3B4CBCB6D |
| SHA256: | 001EC9915F9C903D53AE42D15F613638ED4C3AF69064A029382566A6860C856D |
| SSDEEP: | 12:2MQdTHUgAUA5V4MqyzpQwkkb5m5ZvJfyN8HZw:29NH3k4NyNldbgv1yNsZw |
MALICIOUS
Changes the login/logoff helper path in the registry
- Topich.exe (PID: 292)
UAC/LUA settings modification
- Topich.exe (PID: 292)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 2776)
Changes appearance of the Explorer extensions
- Topich.exe (PID: 292)
Disables Windows Defender
- Topich.exe (PID: 292)
SUSPICIOUS
Reads the Internet Settings
- Topich.exe (PID: 292)
- Gta6.exe (PID: 2672)
- sipnotify.exe (PID: 1600)
- Run.exe (PID: 2332)
Starts CMD.EXE for commands execution
- Gta6.exe (PID: 2672)
- Topich.exe (PID: 292)
Reads settings of System Certificates
- sipnotify.exe (PID: 1600)
The system shut down or reboot
- cmd.exe (PID: 2776)
INFO
Application launched itself
- iexplore.exe (PID: 128)
Checks supported languages
- Gta6.exe (PID: 2672)
- Topich.exe (PID: 292)
- IMEKLMG.EXE (PID: 2068)
- IMEKLMG.EXE (PID: 2080)
- Run.exe (PID: 2332)
- wmpnscfg.exe (PID: 2644)
- wmpnscfg.exe (PID: 2664)
- Rndmsms.exe (PID: 2816)
- Rndmsms.exe (PID: 2912)
- Rndmsms.exe (PID: 3076)
- Gdi_Radial_Blur.exe (PID: 3100)
- Rndmsms.exe (PID: 2876)
- Rndmsms.exe (PID: 3148)
- Rndmsms.exe (PID: 3208)
- Rndmsms.exe (PID: 3284)
Reads the computer name
- Gta6.exe (PID: 2672)
- IMEKLMG.EXE (PID: 2080)
- Run.exe (PID: 2332)
- IMEKLMG.EXE (PID: 2068)
- wmpnscfg.exe (PID: 2644)
- Rndmsms.exe (PID: 2816)
- Rndmsms.exe (PID: 2876)
- Rndmsms.exe (PID: 2912)
- Rndmsms.exe (PID: 3076)
- wmpnscfg.exe (PID: 2664)
- Rndmsms.exe (PID: 3208)
- Gdi_Radial_Blur.exe (PID: 3100)
- Rndmsms.exe (PID: 3148)
- Rndmsms.exe (PID: 3284)
- Topich.exe (PID: 292)
The process uses the downloaded file
- WinRAR.exe (PID: 2332)
- iexplore.exe (PID: 128)
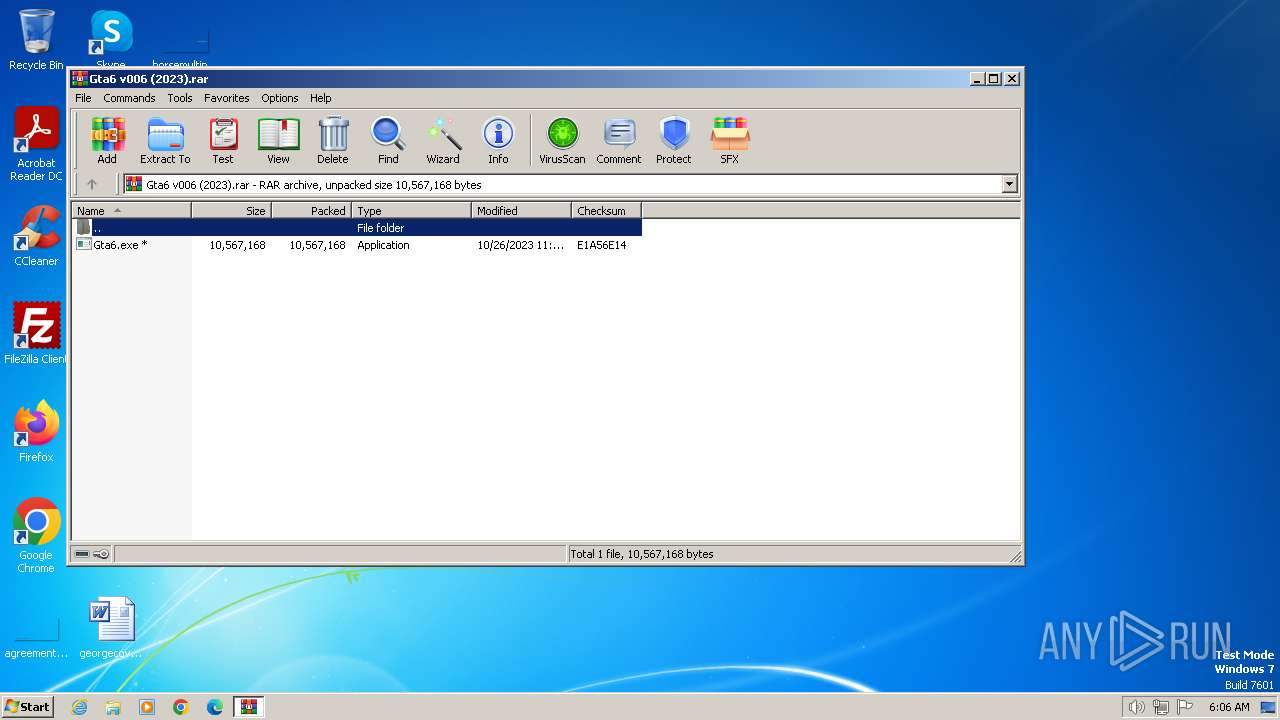
Drops the executable file immediately after the start
- Gta6.exe (PID: 2672)
- WinRAR.exe (PID: 2332)
- Topich.exe (PID: 292)
Reads the machine GUID from the registry
- Gta6.exe (PID: 2672)
- Run.exe (PID: 2332)
- Rndmsms.exe (PID: 2912)
- Rndmsms.exe (PID: 2816)
- Rndmsms.exe (PID: 2876)
- Rndmsms.exe (PID: 3148)
- Rndmsms.exe (PID: 3076)
- Rndmsms.exe (PID: 3208)
- Topich.exe (PID: 292)
- Rndmsms.exe (PID: 3284)
Manual execution by a user
- Gta6.exe (PID: 2672)
- IMEKLMG.EXE (PID: 2080)
- IMEKLMG.EXE (PID: 2068)
- wmpnscfg.exe (PID: 2644)
- wmpnscfg.exe (PID: 2664)
Process checks are UAC notifies on
- Topich.exe (PID: 292)
- IMEKLMG.EXE (PID: 2080)
- IMEKLMG.EXE (PID: 2068)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1804)
- sipnotify.exe (PID: 1600)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1600)
Reads Environment values
- Run.exe (PID: 2332)
Checks proxy server information
- Run.exe (PID: 2332)
Starts itself from another location
- Gta6.exe (PID: 2672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
115
Monitored processes
26
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://docviewer.yandex.ru/view/0/?*=ICHLGq4F0lg40wR5z89QwuW7A0R7InVybCI6InlhLWRpc2stcHVibGljOi8vM0JSRFRUR3FqN0pjZmhlS2cwRzJNVVBGNWVwV2JEU2g5b3Ird0dsMzZrZStjb3JhaXUzQTZqd29lb25YaWxBd3EvSjZicG1SeU9Kb25UM1ZvWG5EYWc9PTovR3RhNiB2MDA2ICgyMDIzKS5yYXIiLCJ0aXRsZSI6Ikd0YTYgdjAwNiAoMjAyMykucmFyIiwibm9pZnJhbWUiOmZhbHNlLCJ1aWQiOiIwIiwidHMiOjE3MDMzOTc4Njk1NjMsInl1IjoiOTE3OTIzNjI4MTcwMjk5ODU5OSJ9" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
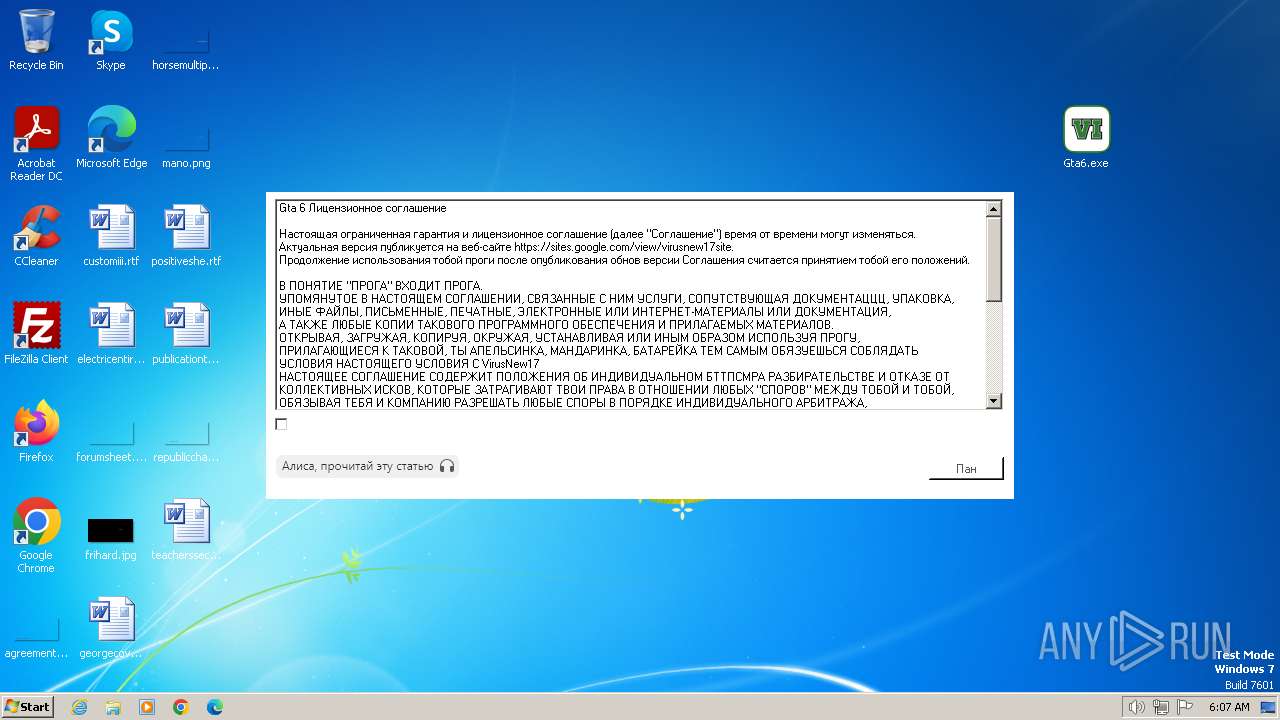
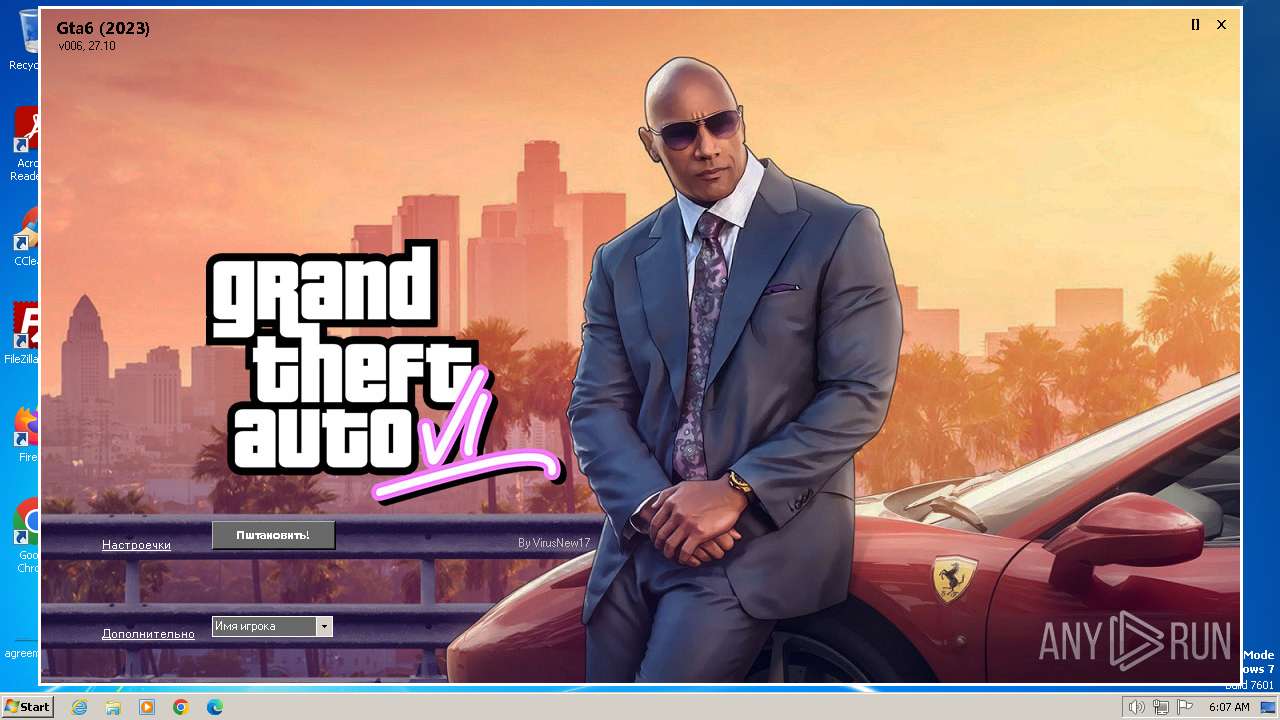
| 292 | "C:\Windows\Setup\State\Topich.exe" | C:\Windows\Setup\State\Topich.exe | Gta6.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Gta6 Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:128 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1600 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1804 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2080 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2104 | bcdedit /set {globalsettings} advancedoptions false | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
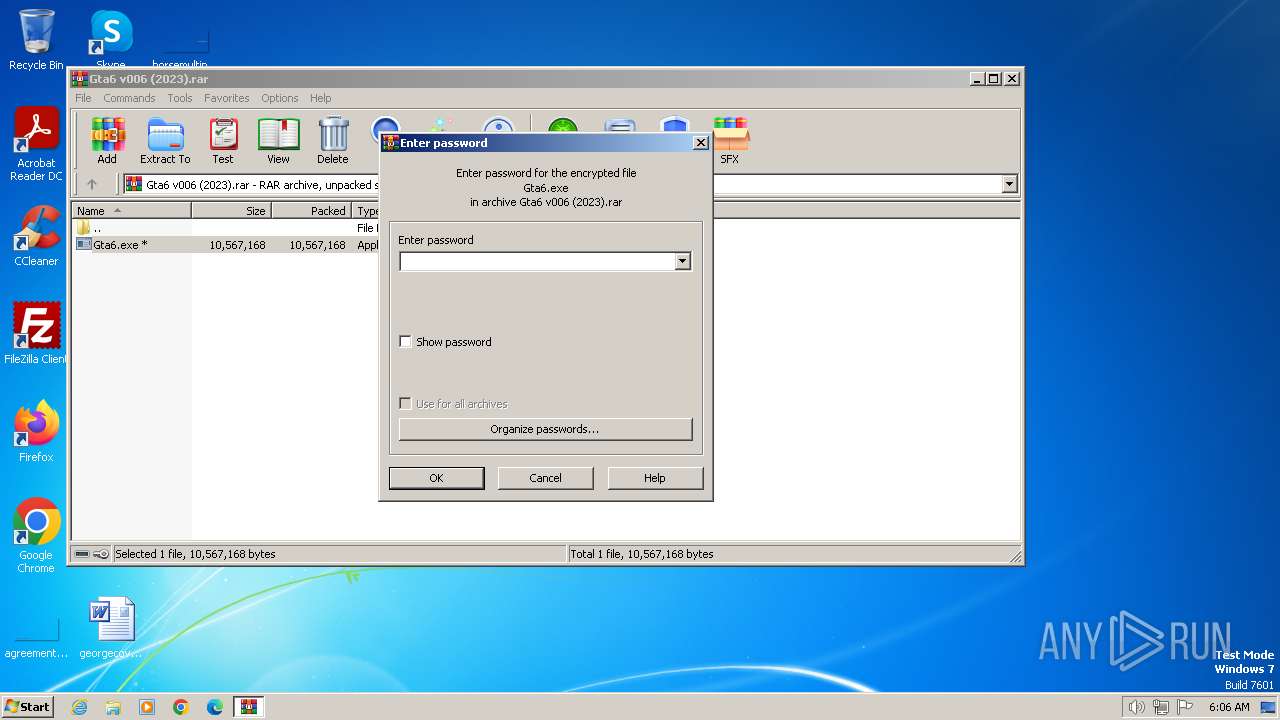
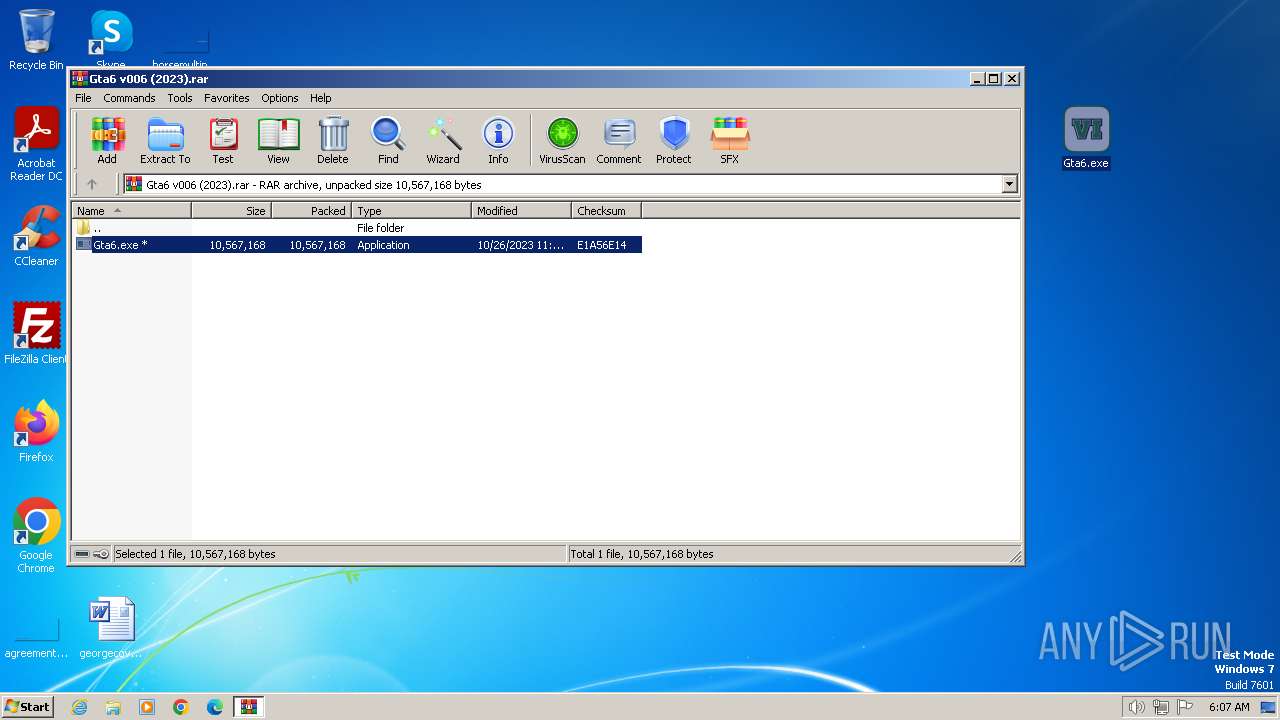
| 2332 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Gta6 v006 (2023).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2332 | "C:\VirusNew17\Topich\Run.exe" | C:\VirusNew17\Topich\Run.exe | — | Topich.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Run Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
22 461
Read events
22 253
Write events
182
Delete events
26
Modification events
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
9
Suspicious files
61
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:C1F7304EDBFB0F7BD1E632089BDF9706 | SHA256:2A4514B87E7E132AD1D7EF0BBE5261215C34C80FCD4EF5359CB80EC21FADB41D | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:5460898F536ECB258319AB8DC96C50A7 | SHA256:70B7FE9D795A9280B40F6C2B648AB99106FB9635D5C5452FD5A75CB1B942518F | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:0E65D90249EE9849DBE8C652C0FEFED1 | SHA256:6E5CA01410D67E748B4AAB5F1C7BBA3C3ED466FF1336FF7C6A1FEC2499D9E3A2 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\349D186F1CB5682FA0194D4F3754EF36_24189A5ADBE6F590307BAA21110D145D | binary | |
MD5:DBF4058D46AA6E74637E75EA89B3A015 | SHA256:747BC27A316C05642DD1E50C6FCAE8B8DC2326228805322C0E682A86AEE61E09 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_7DAD5545724AA2C98C55095F428499FB | binary | |
MD5:636C12325A08A9D2926850E432F7B9E8 | SHA256:880CDF0B3D9D5EF9162F822D9E2EEFB4F36754FF5C7CC70DBA768225552CA9A6 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:766CA97EE637ADA127BC0EF12FA79BAB | SHA256:DA39C10F9DD5F1C966B2F1599CF06C7A3C81F1CBC404674580F2E32A7BBBA981 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\81B9B36F9ABC4DA631A4713EE66FAEC6_D0EECC40864A7E2AABBD4325CBB7C9B5 | binary | |
MD5:1E14EC9AAC89323D54FD859048472059 | SHA256:2089898E1D4E694CEB7414539DABF1A9DCD0BC6B0D38B7882E8D913DE292A8E8 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2C09EEZD.txt | text | |
MD5:D90BA5F8EBC8616C61D1D76E971CF77F | SHA256:5D8B9C87A5EE9A337362512BF81AD8C72AEB87A73D2126FF9D55F4A274F8A746 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ZMJ1NFZA.txt | text | |
MD5:1ED99C6BD28EEB8F0976368250FCC810 | SHA256:2C2E7DFE0536ED3939055DF31645173A46E6EAEA8F6CC14F9399044055B79B9C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
35
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
324 | iexplore.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?129d20c84d8c4223 | unknown | compressed | 4.66 Kb | unknown |
324 | iexplore.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
324 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDCcZrQuON5%2BRFGXczQ%3D%3D | unknown | binary | 1.40 Kb | unknown |
324 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | binary | 1.41 Kb | unknown |
324 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHUeP1PjGFkz6V8I7O6tApc%3D | unknown | binary | 1.41 Kb | unknown |
324 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | binary | 1.40 Kb | unknown |
128 | iexplore.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a85e8d0c2f0a71a5 | unknown | — | — | unknown |
324 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr5/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQiD0S5cIHyfrLTJ1fvAkJWflH%2B2QQUPeYpSJvqB8ohREom3m7e0oPQn1kCDQHuXyKVQkkF%2BQGRqNw%3D | unknown | binary | 1.25 Kb | unknown |
324 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDGR9zAVCqD3GmxxJUg%3D%3D | unknown | binary | 938 b | unknown |
324 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDDeQwBkGHaRwgVLWqQ%3D%3D | unknown | binary | 938 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
324 | iexplore.exe | 77.88.21.148:443 | docviewer.yandex.ru | YANDEX LLC | RU | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
324 | iexplore.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
324 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
324 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
324 | iexplore.exe | 87.250.251.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
324 | iexplore.exe | 93.158.134.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
128 | iexplore.exe | 77.88.21.148:443 | docviewer.yandex.ru | YANDEX LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
docviewer.yandex.ru |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
mc.yandex.com |
| whitelisted |
yastatic.net |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |