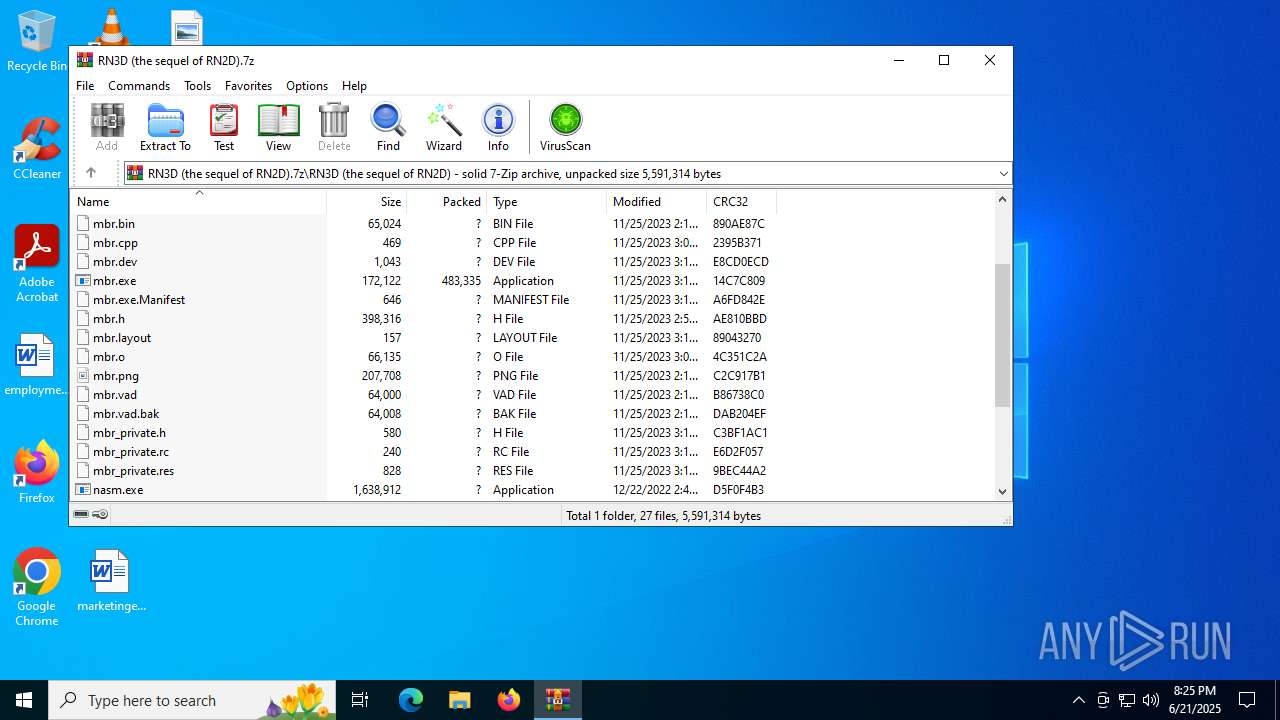
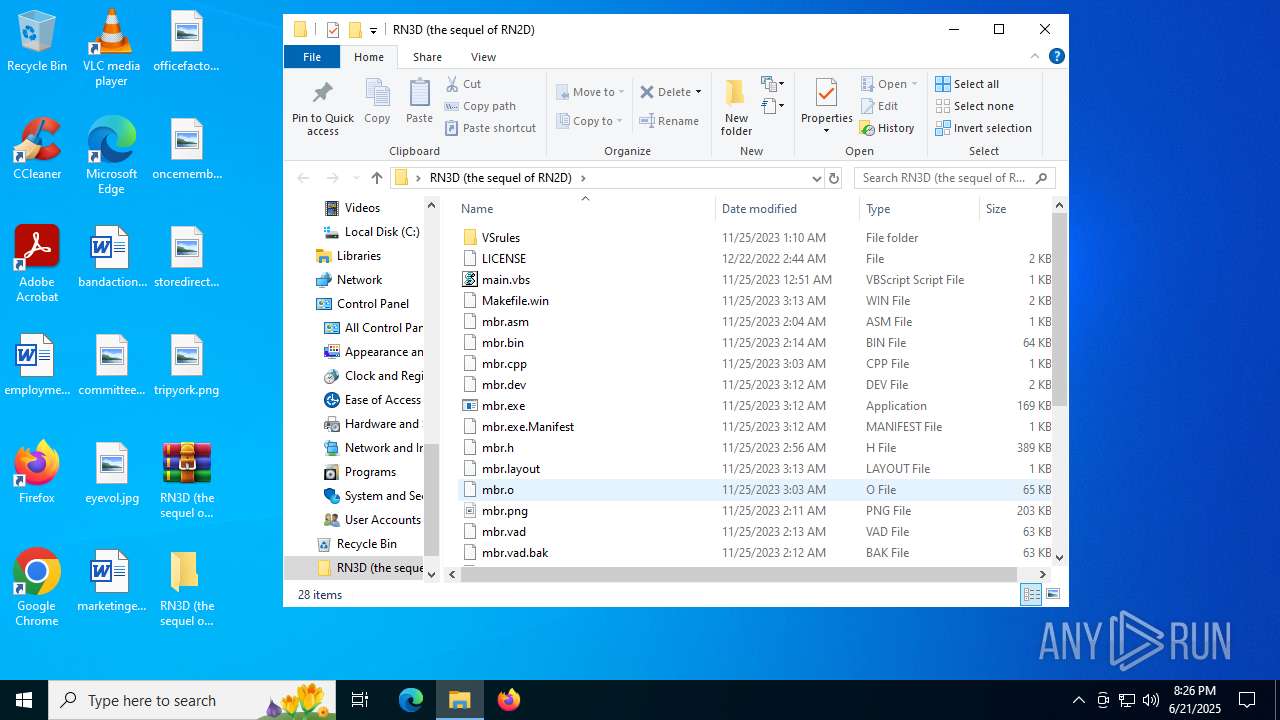
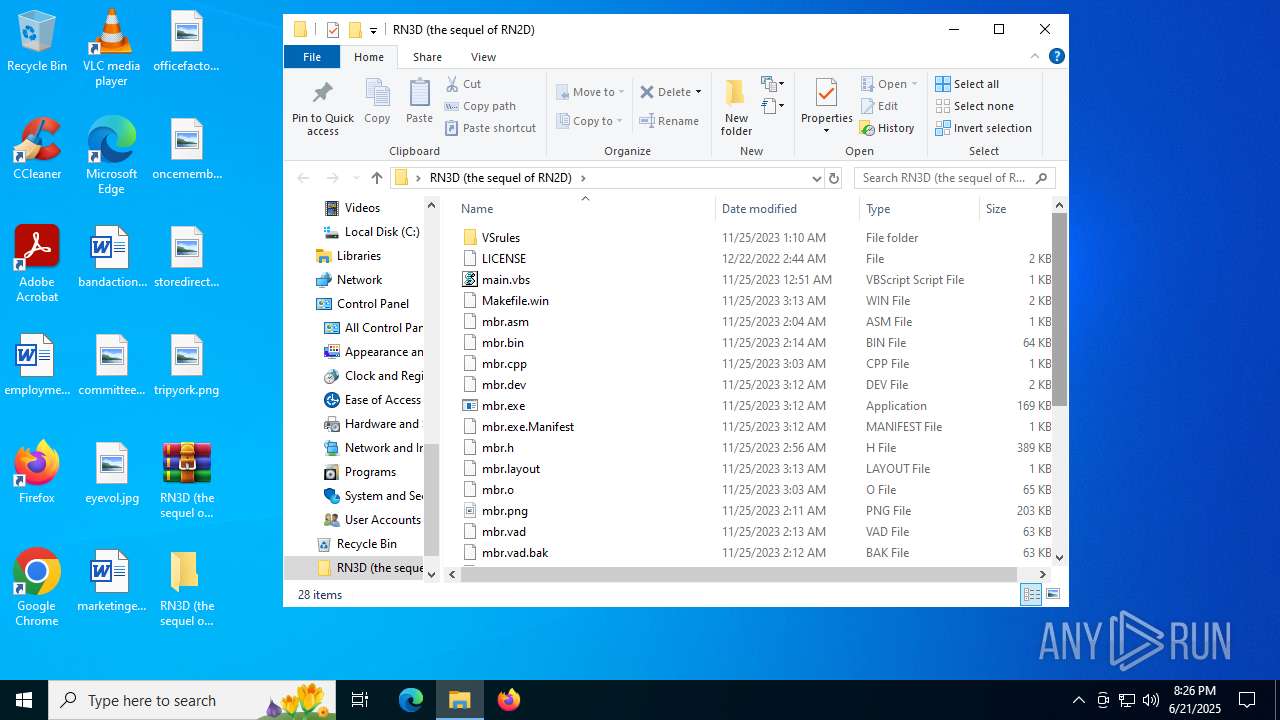
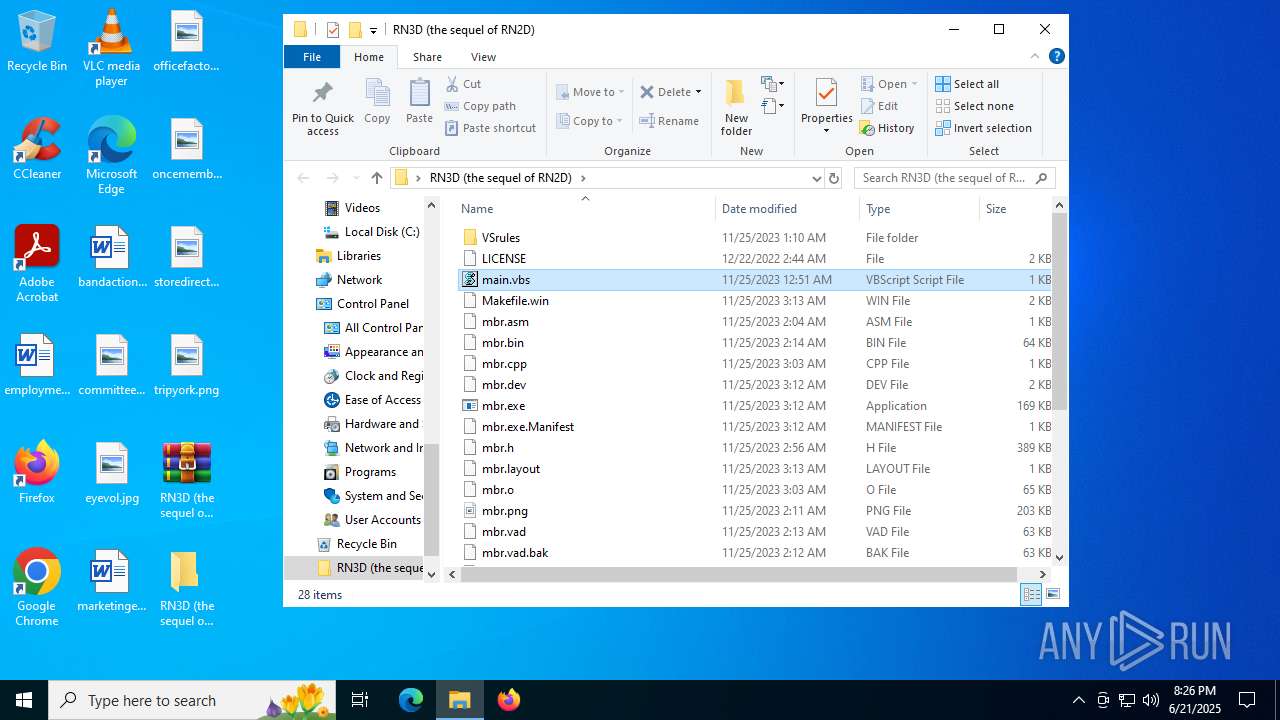
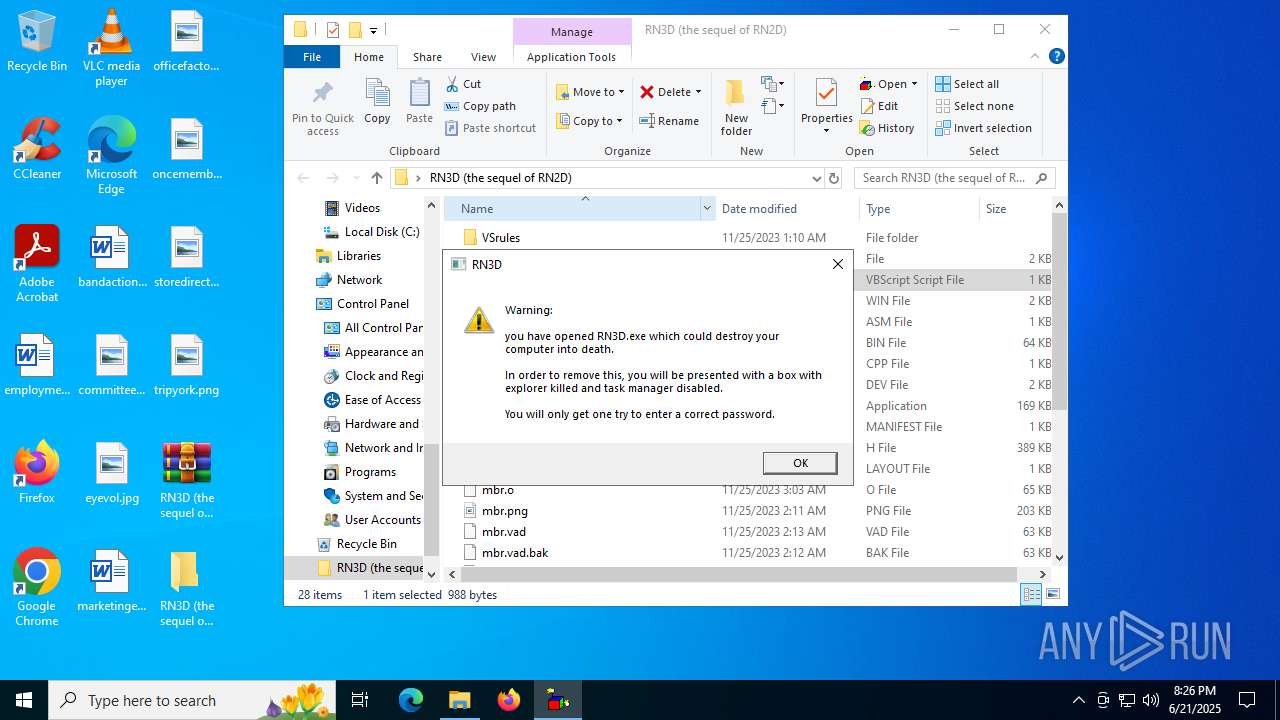
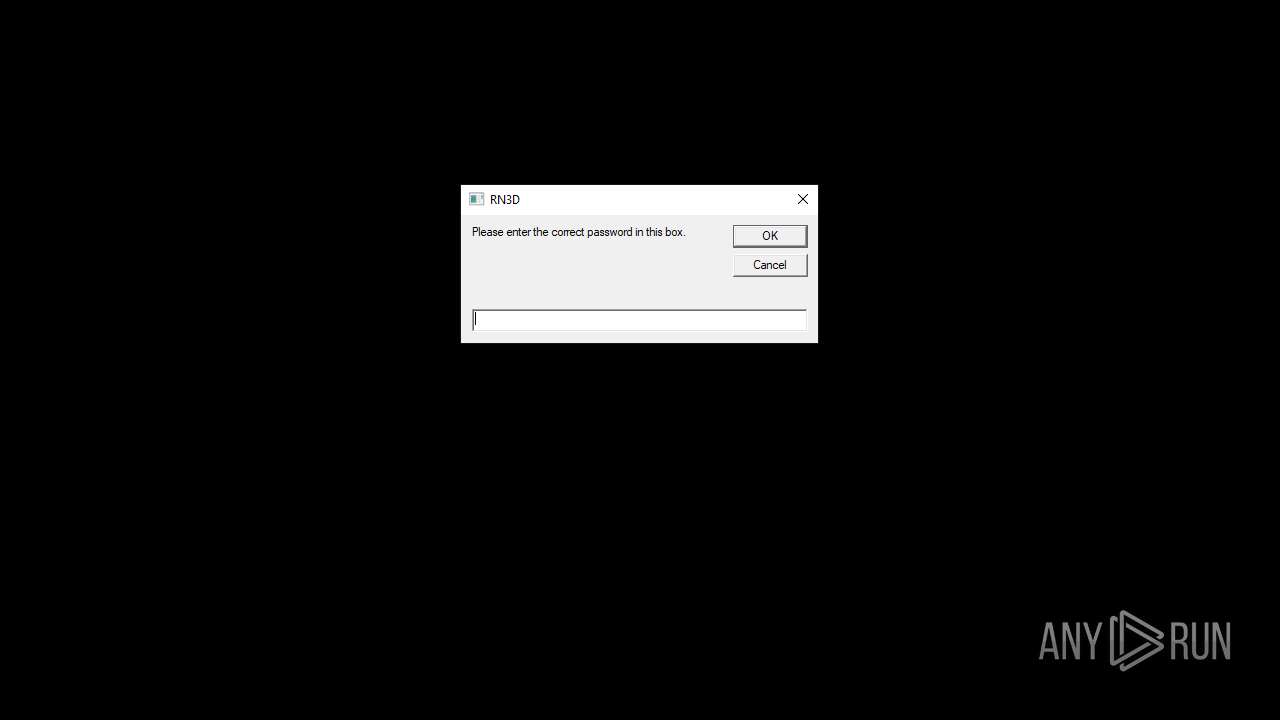
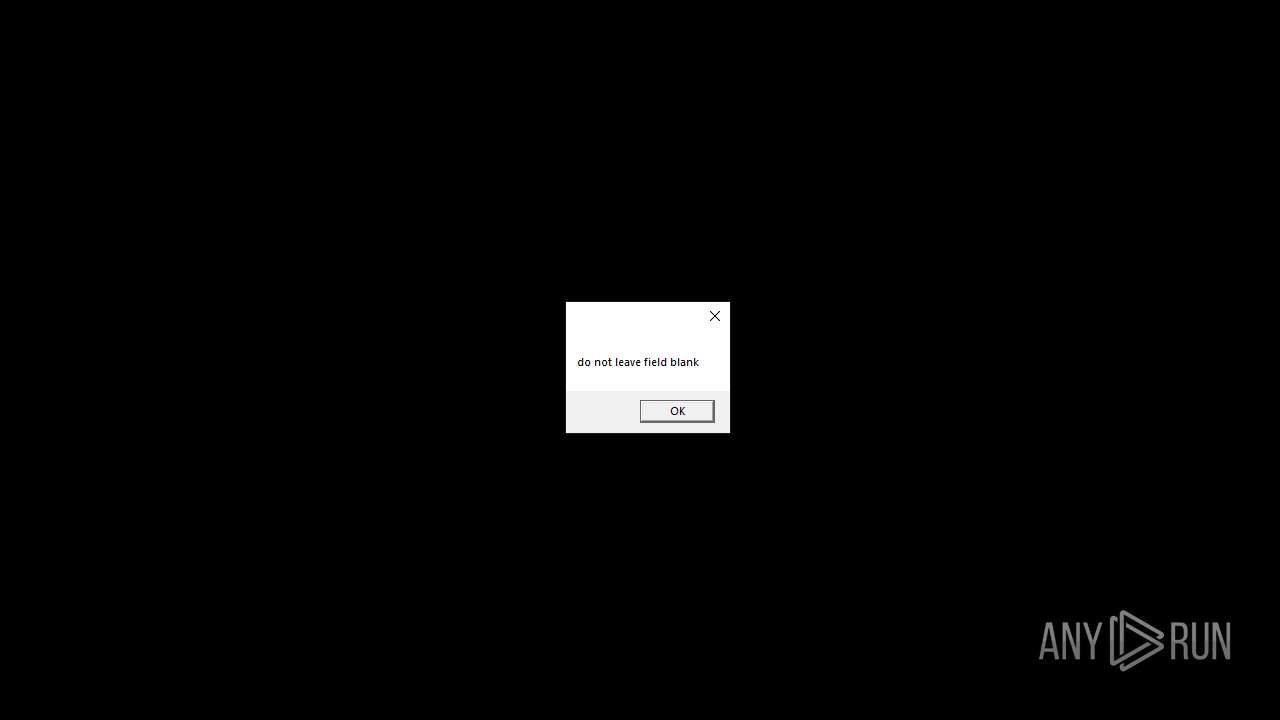
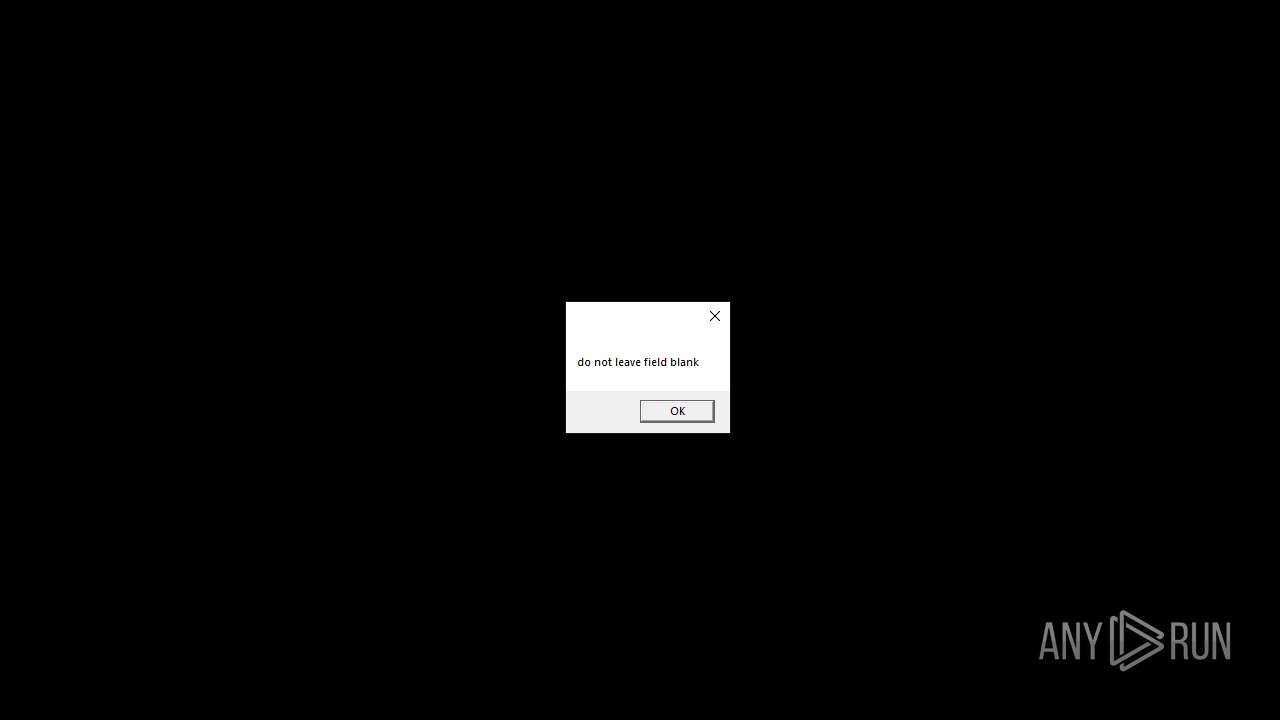
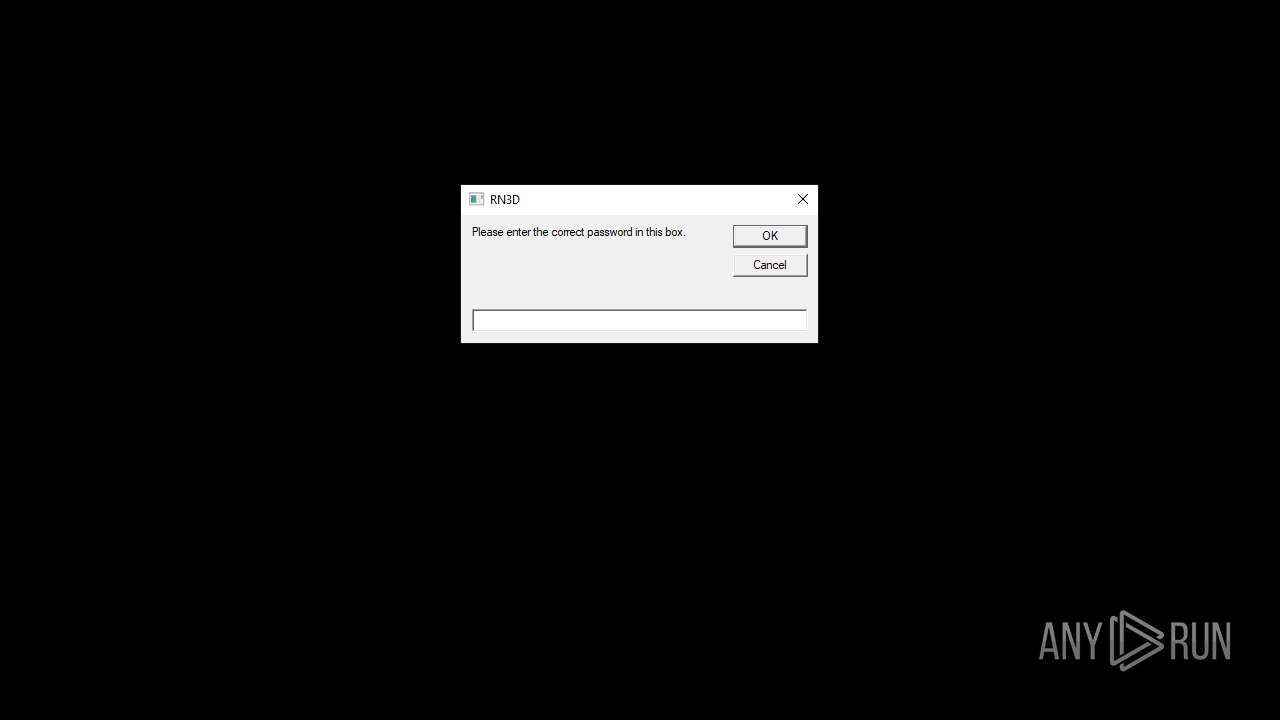
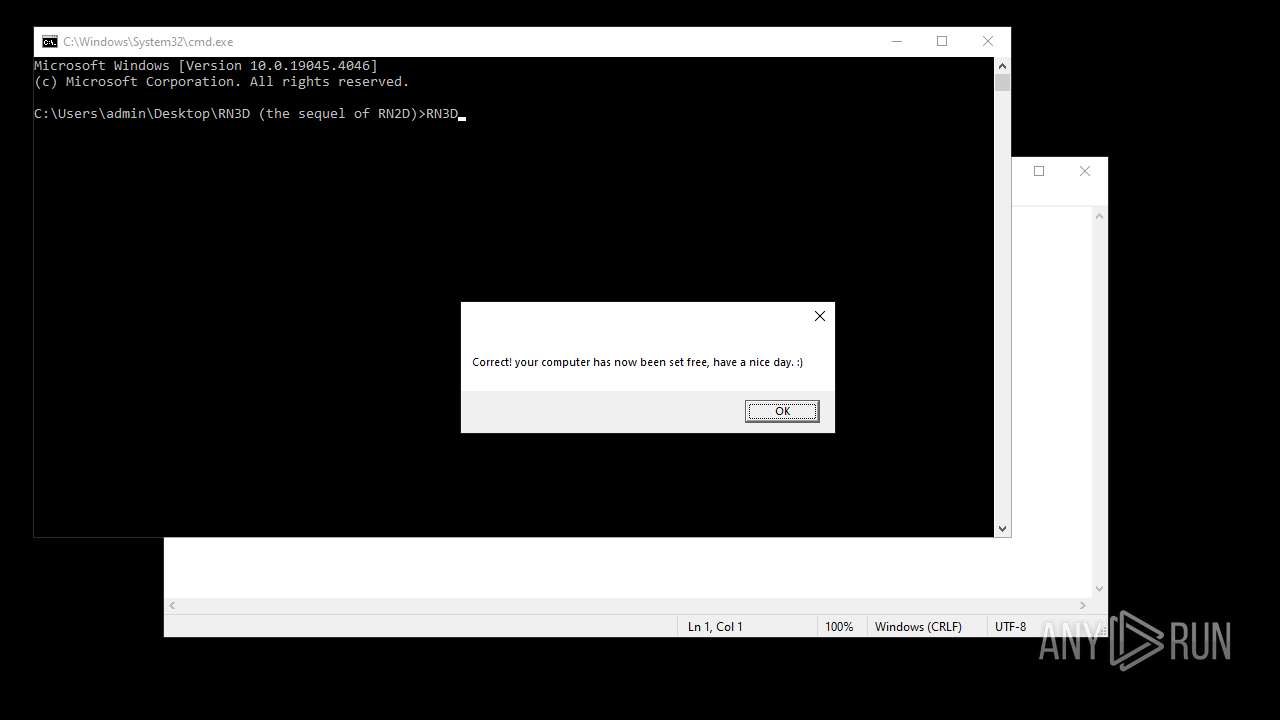
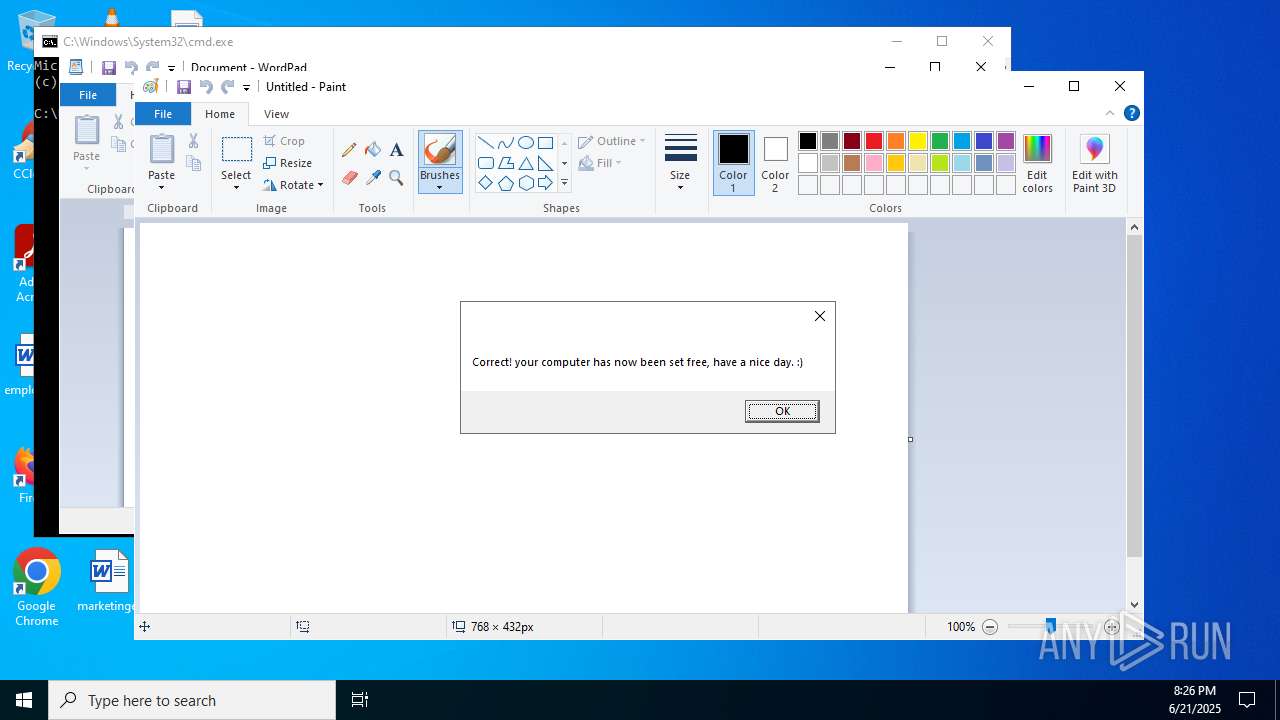
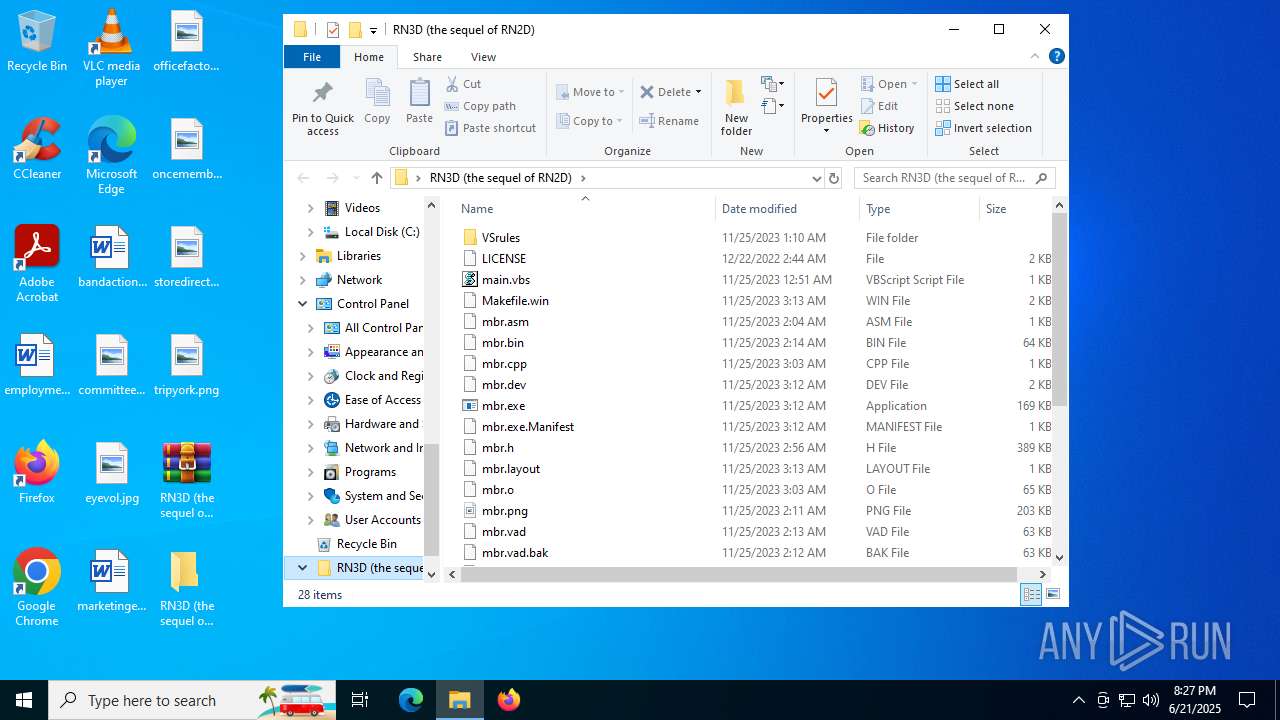
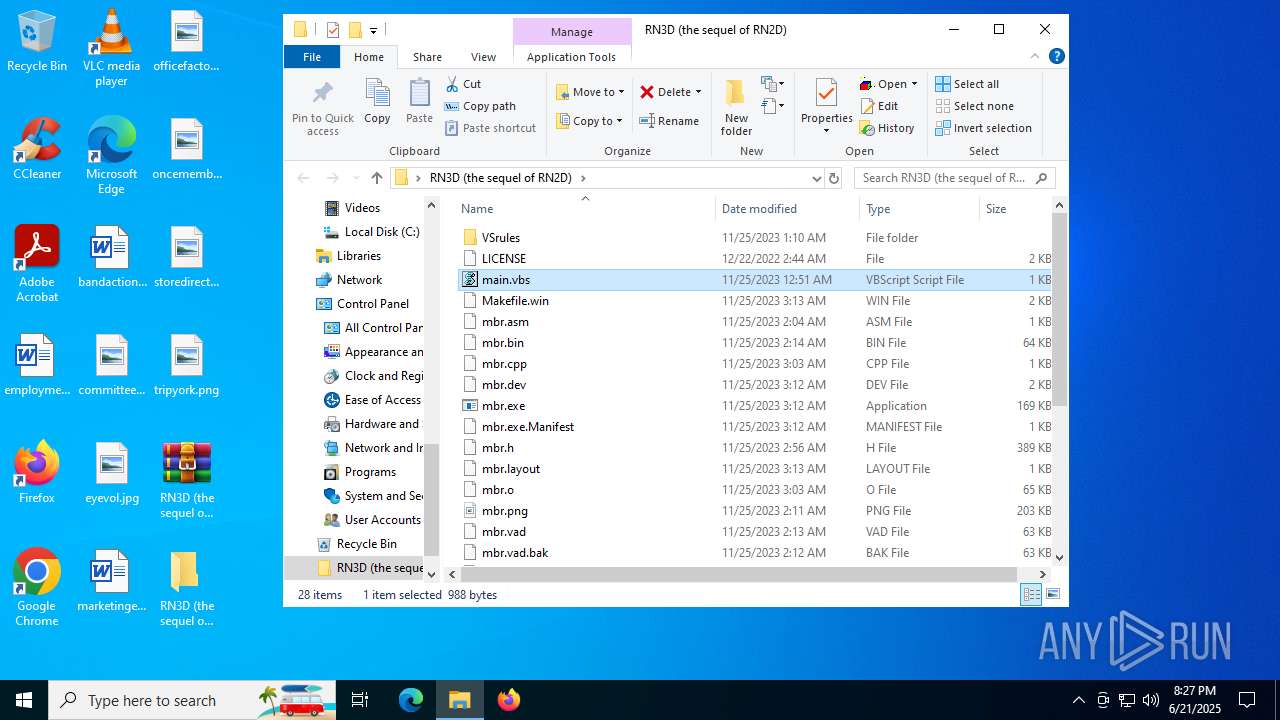
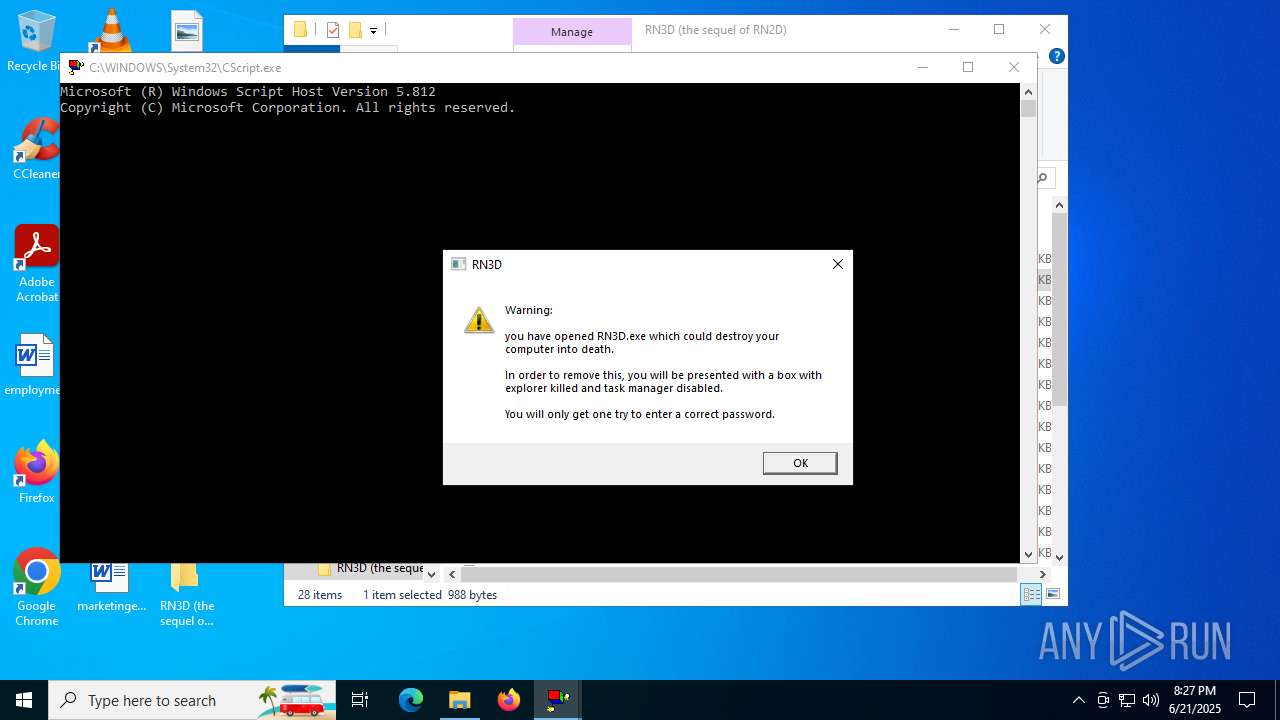
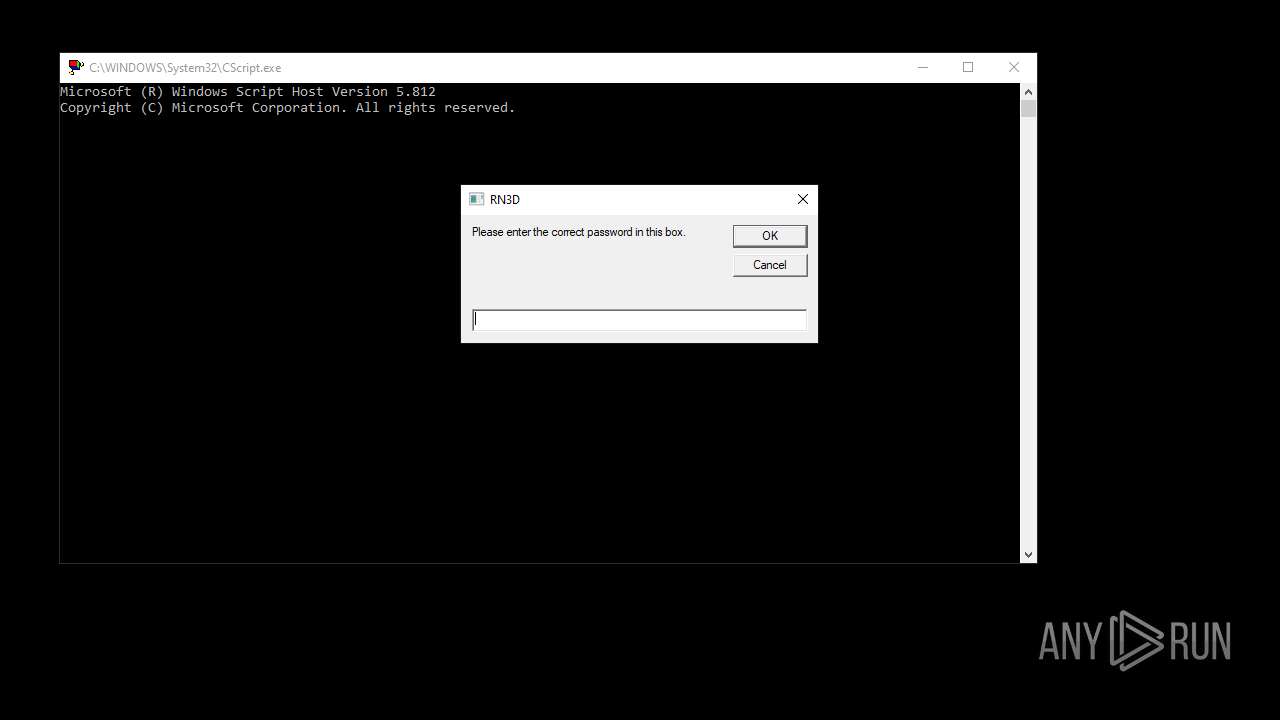
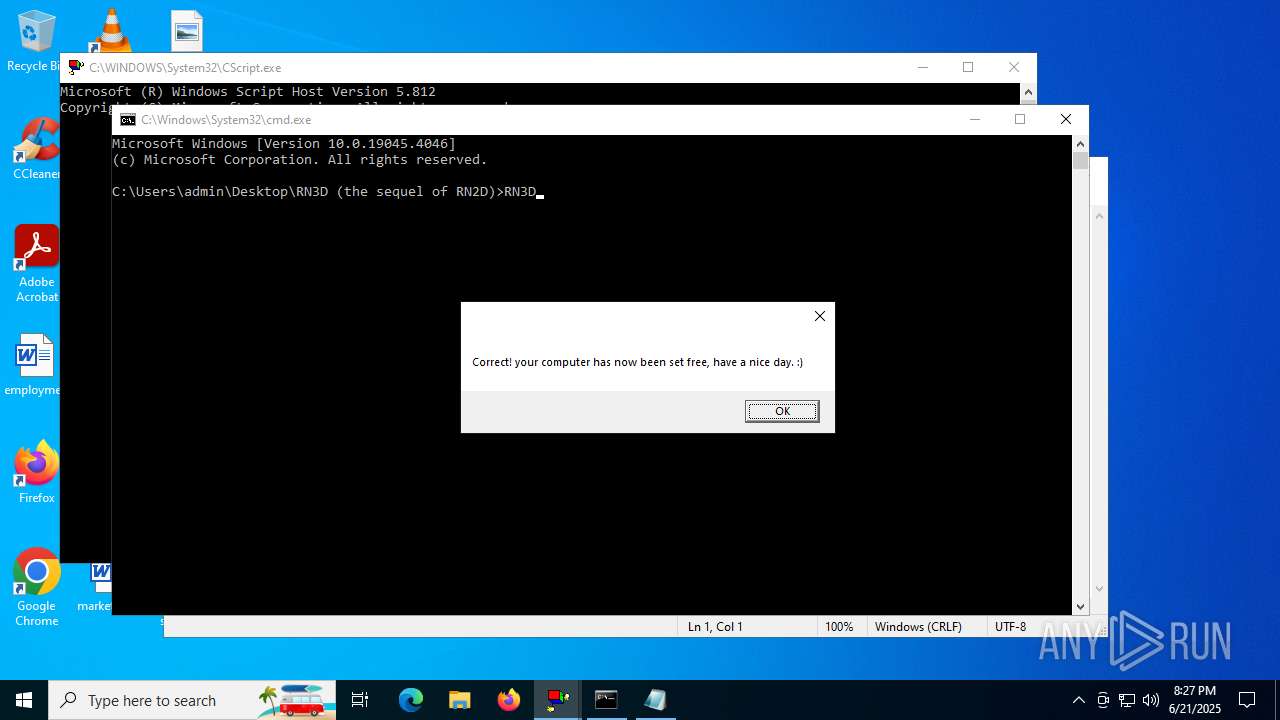
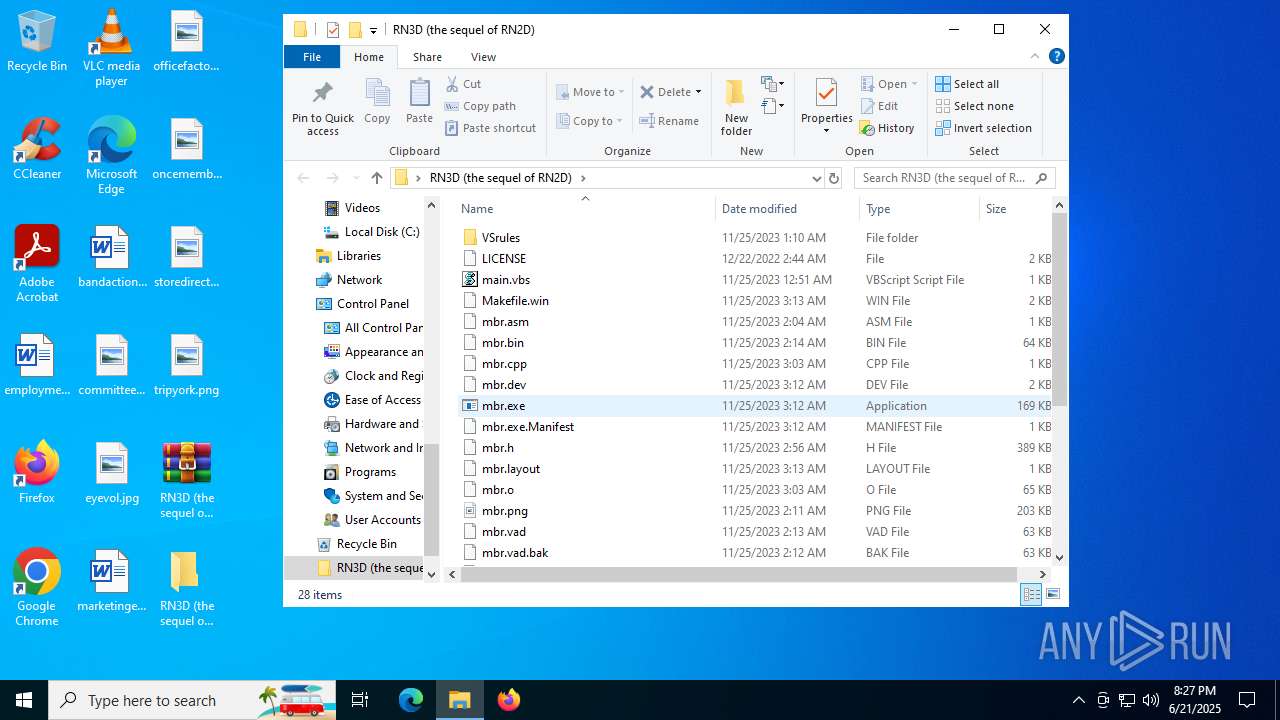
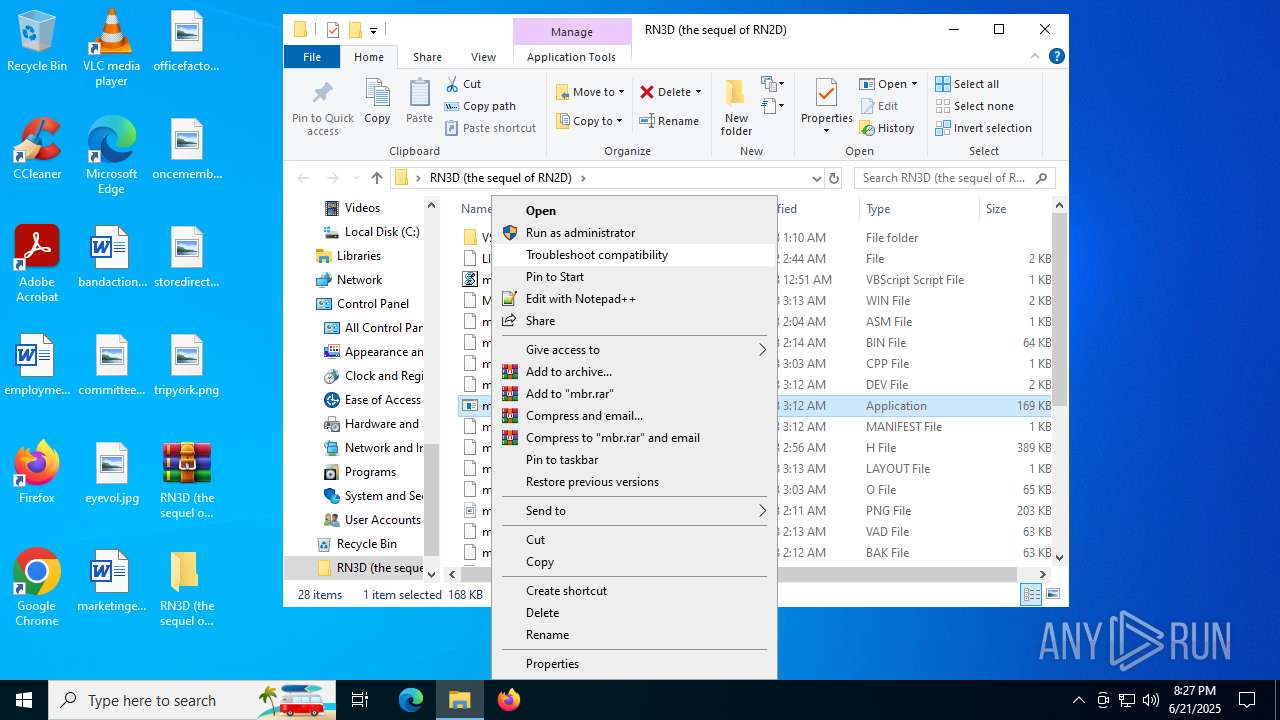
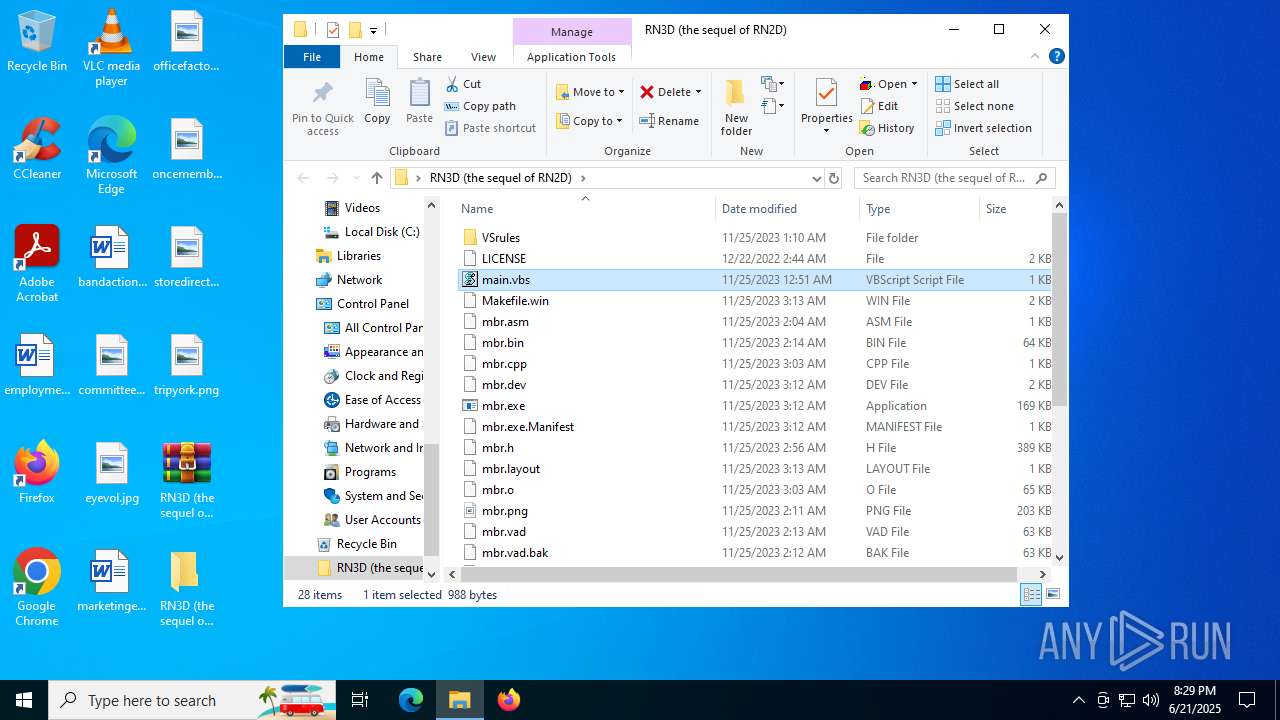
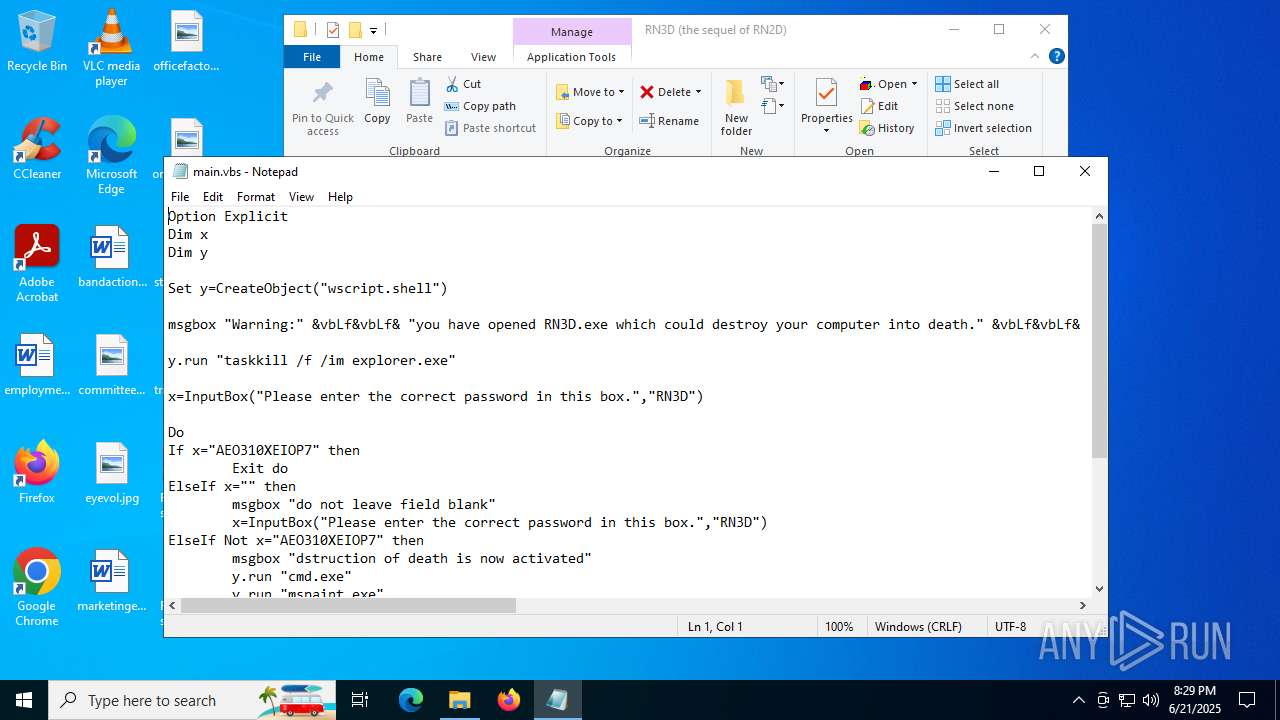
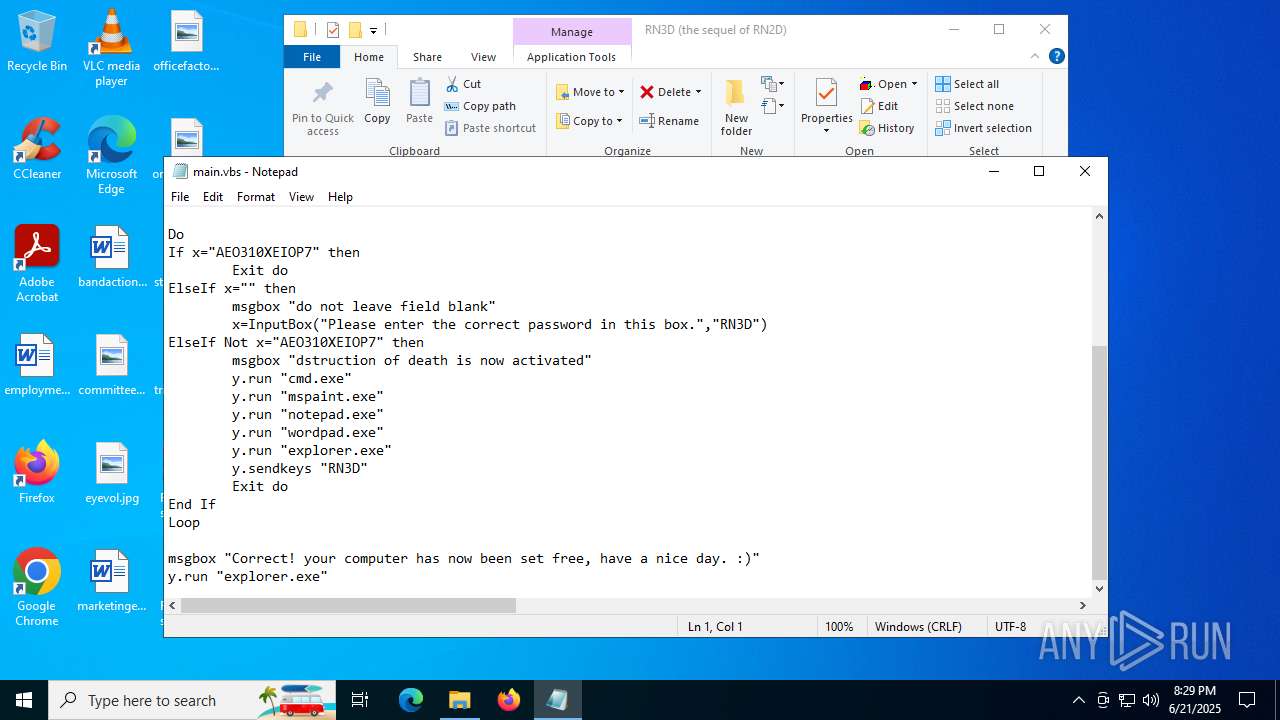
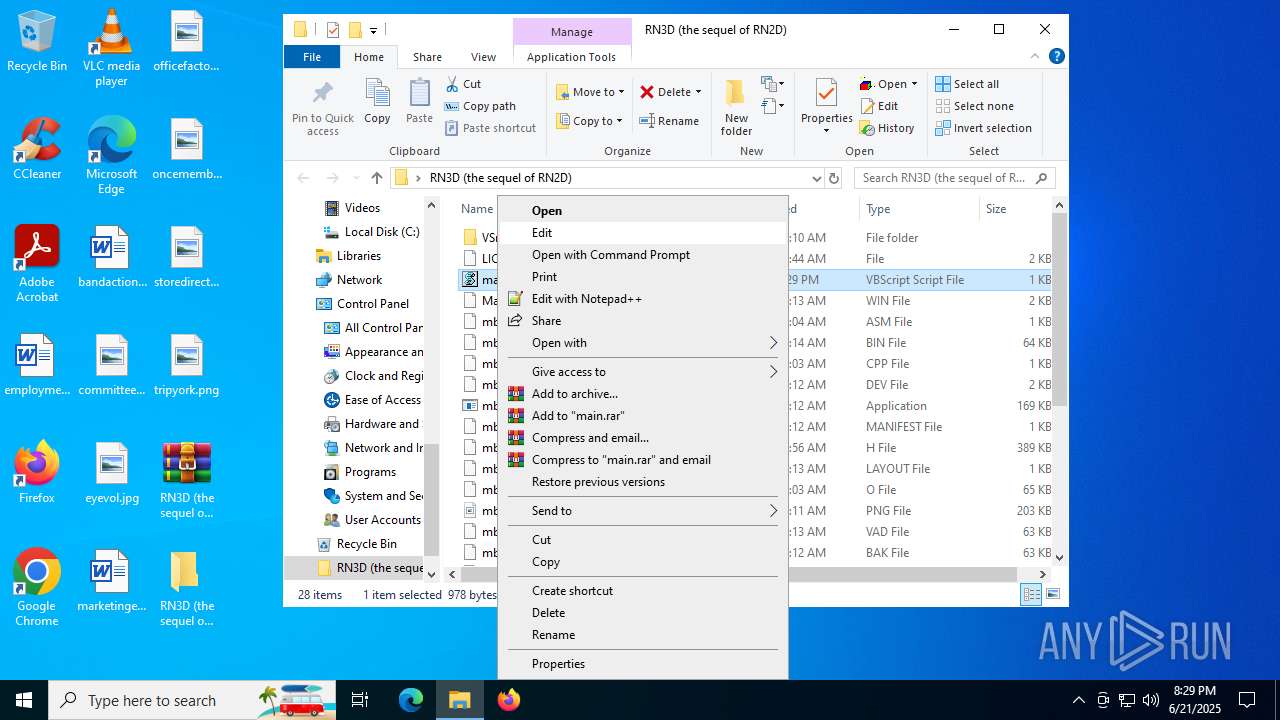
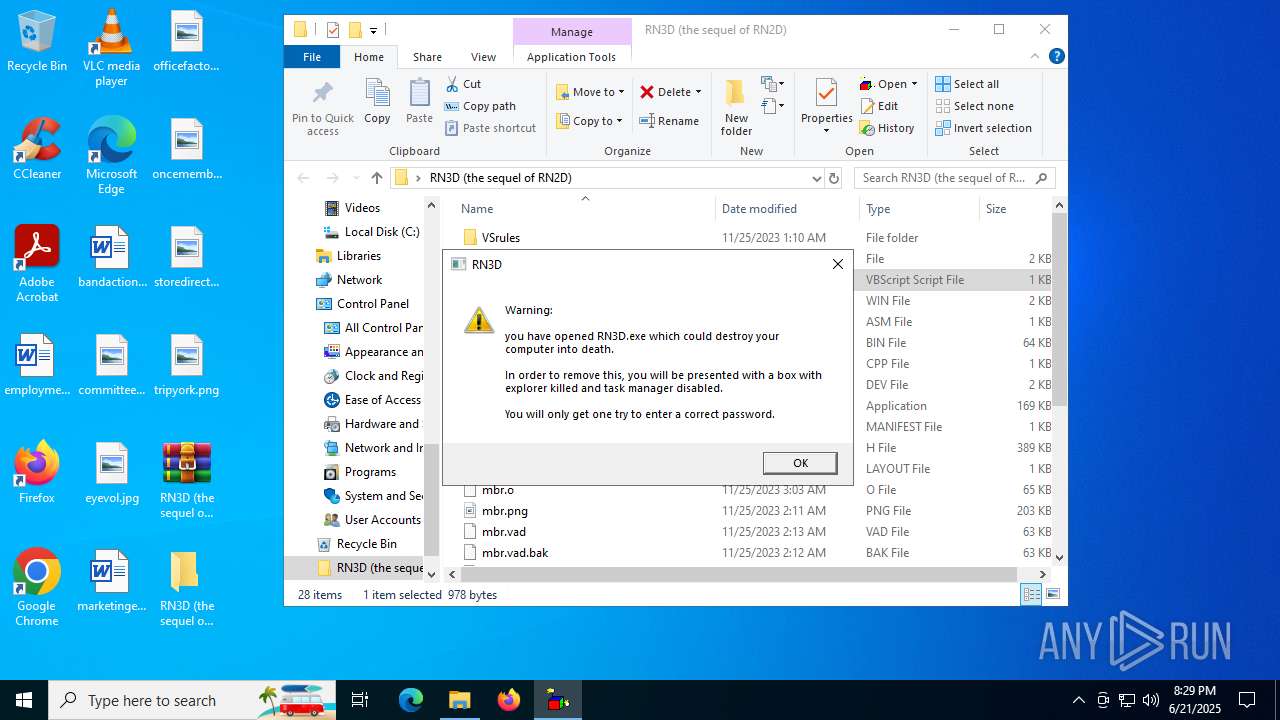
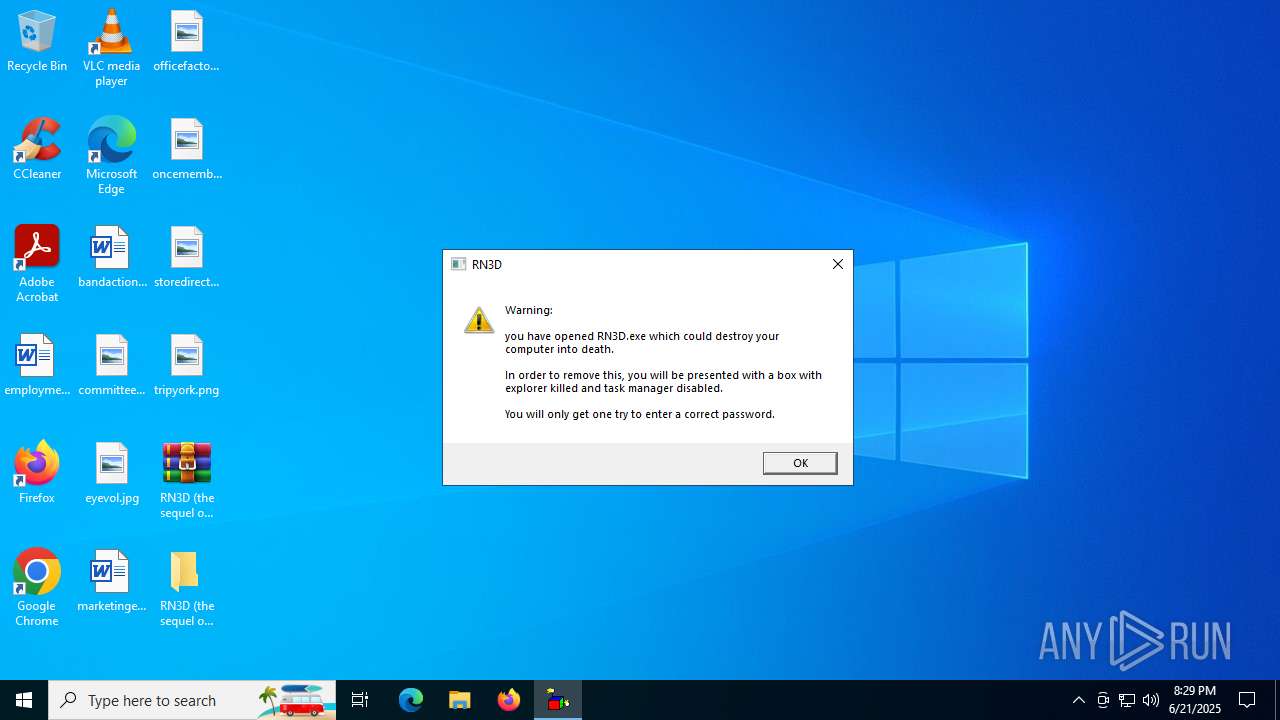
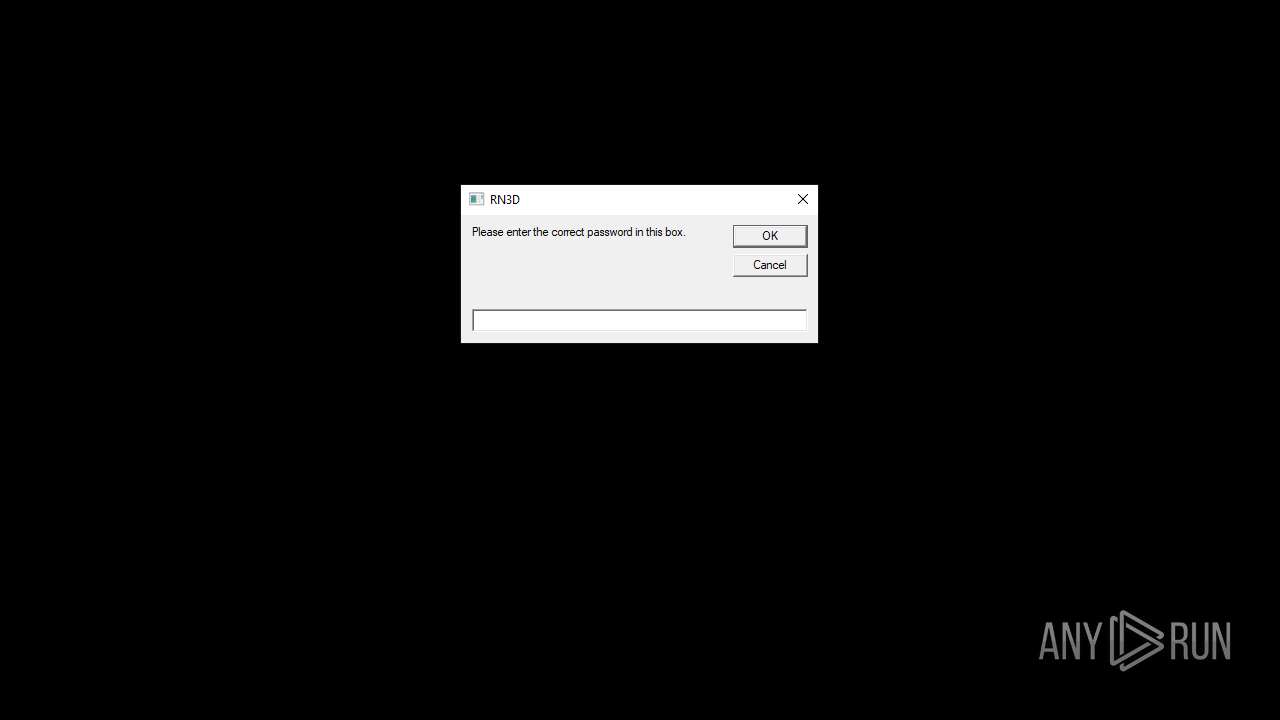
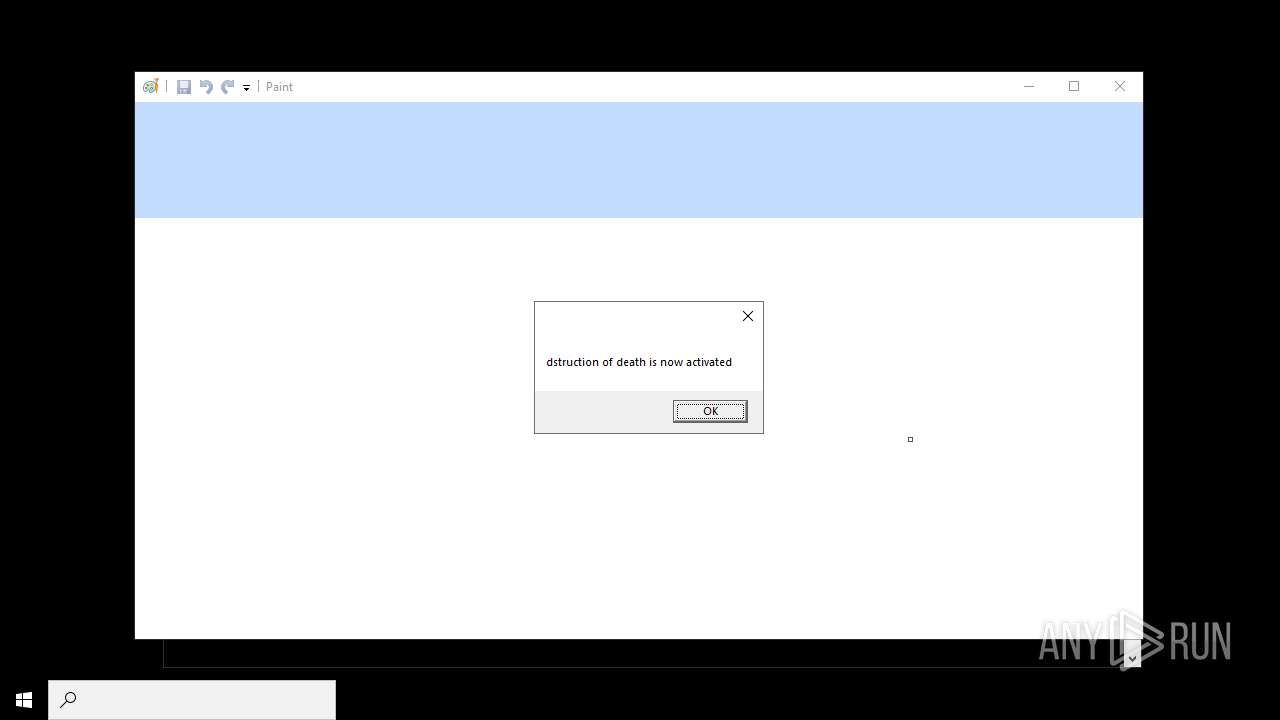
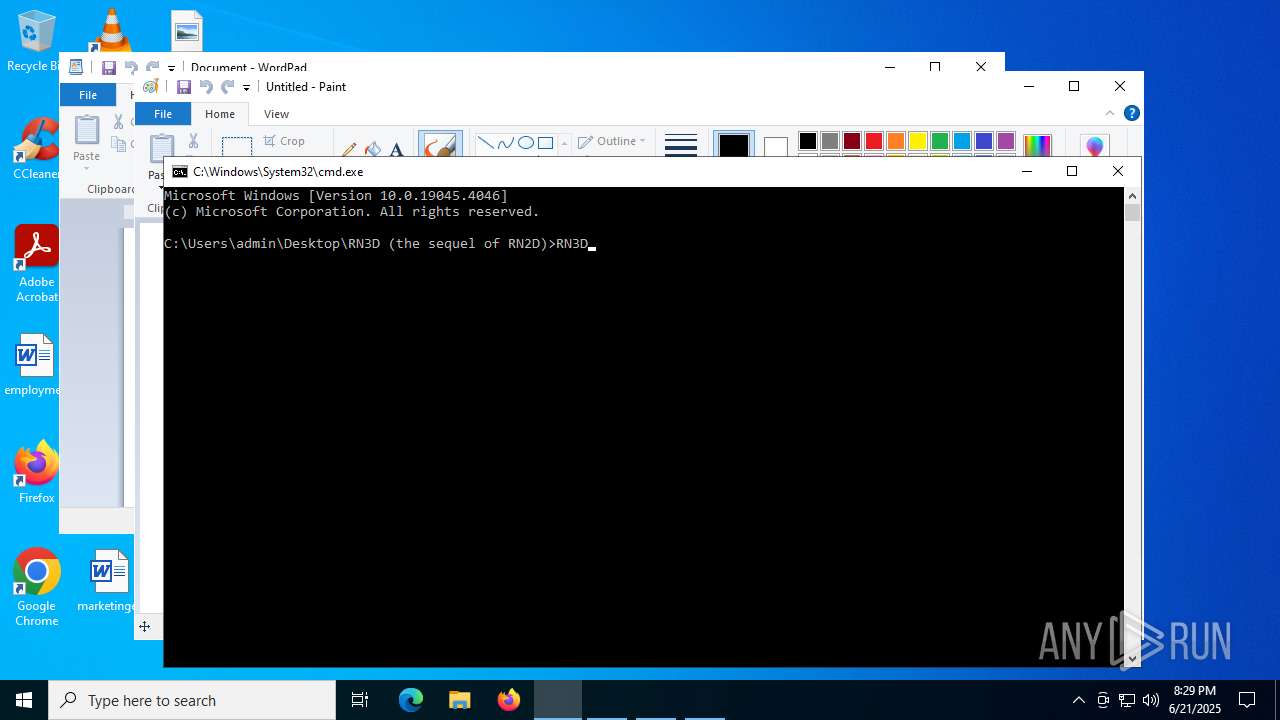
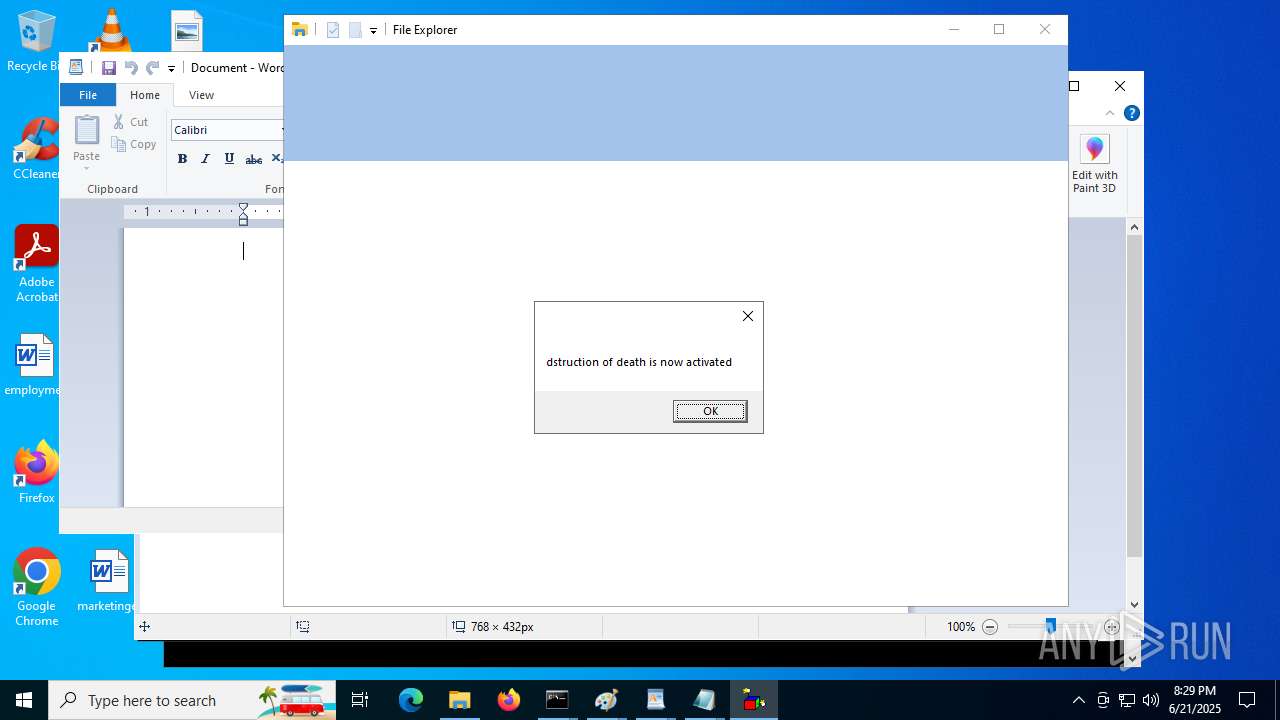
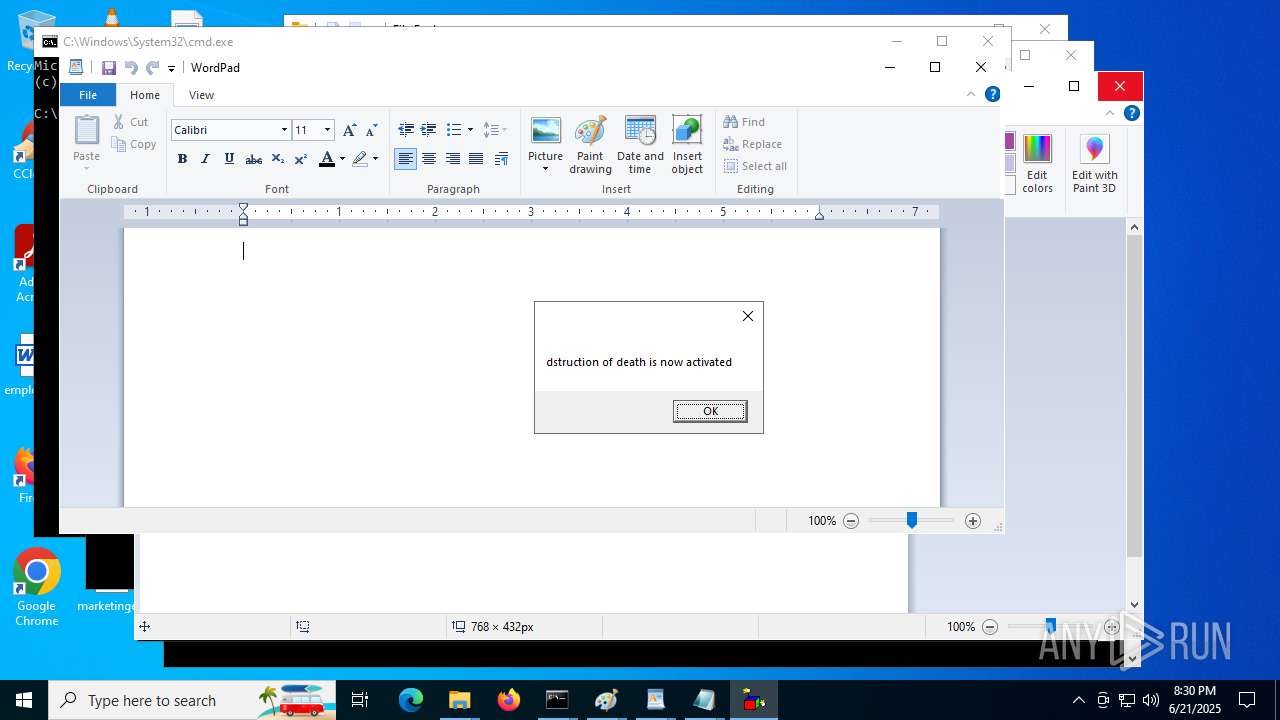
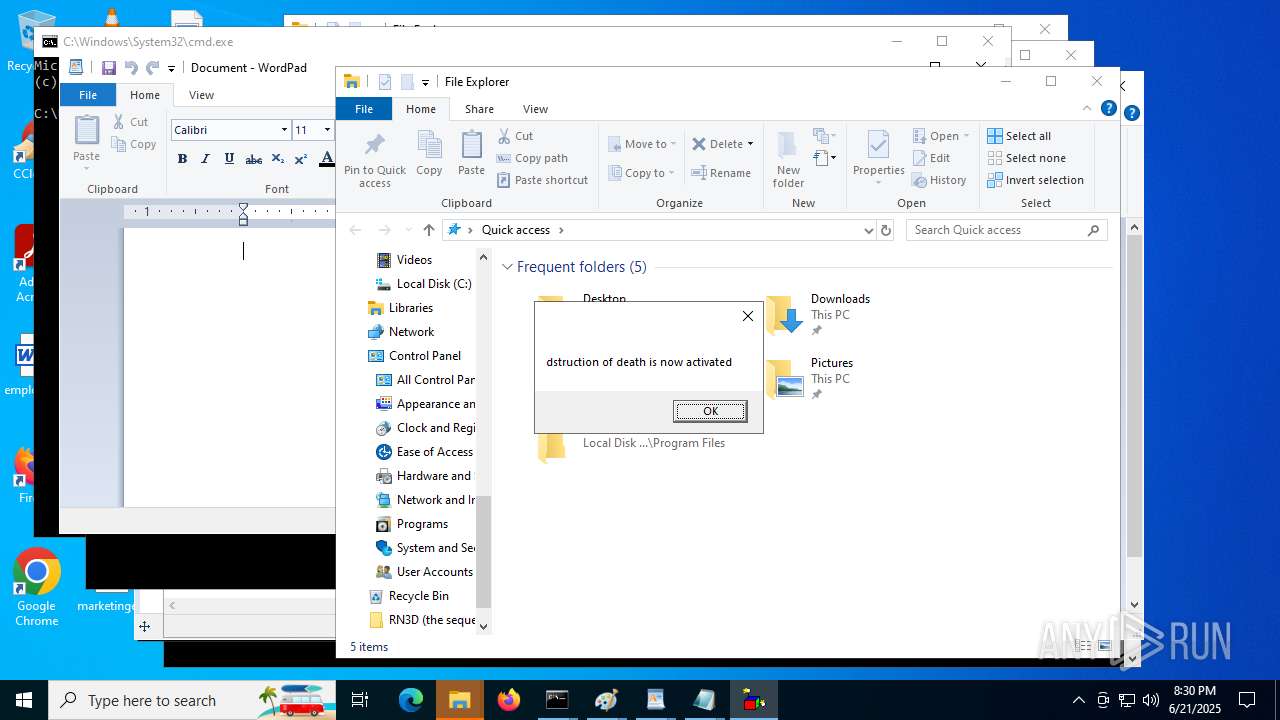
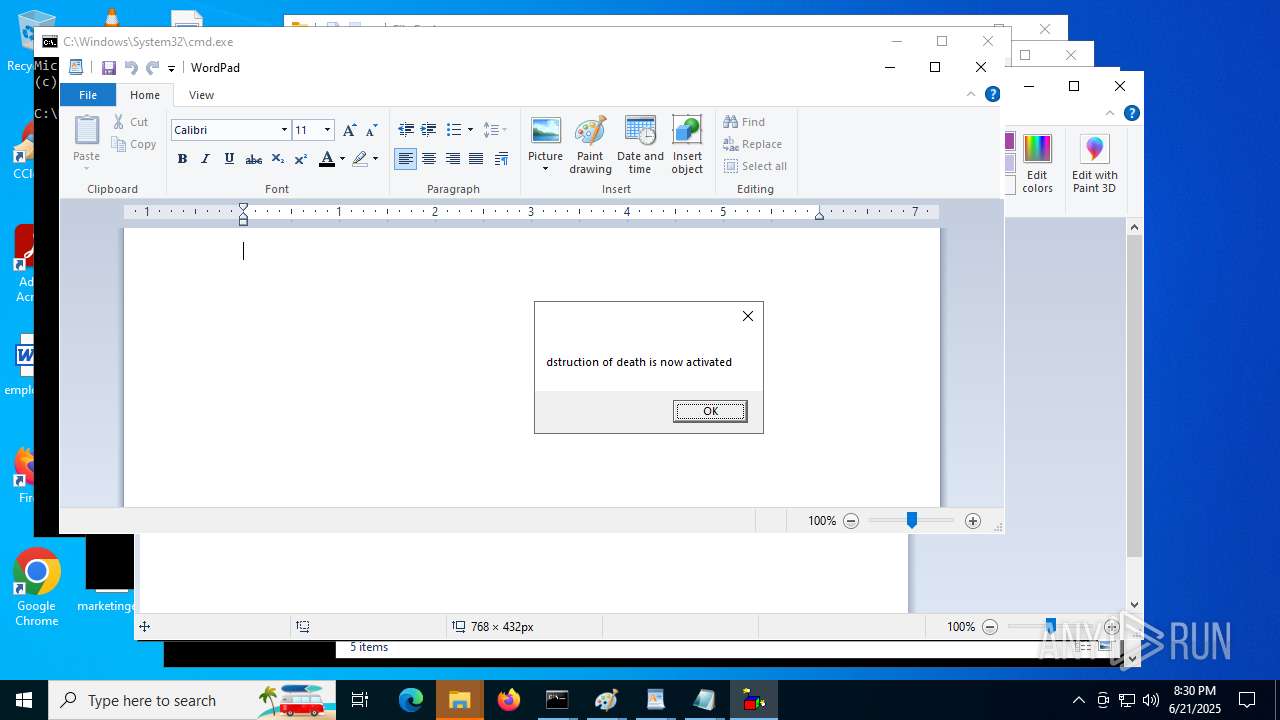
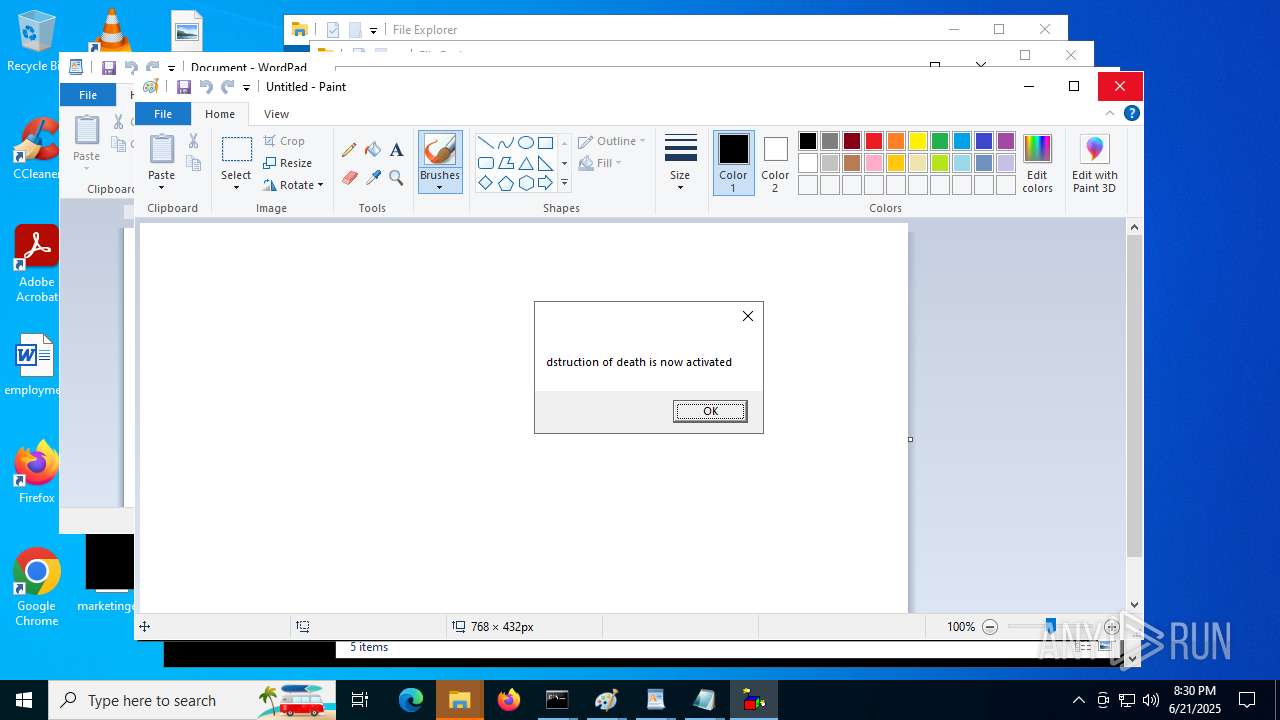
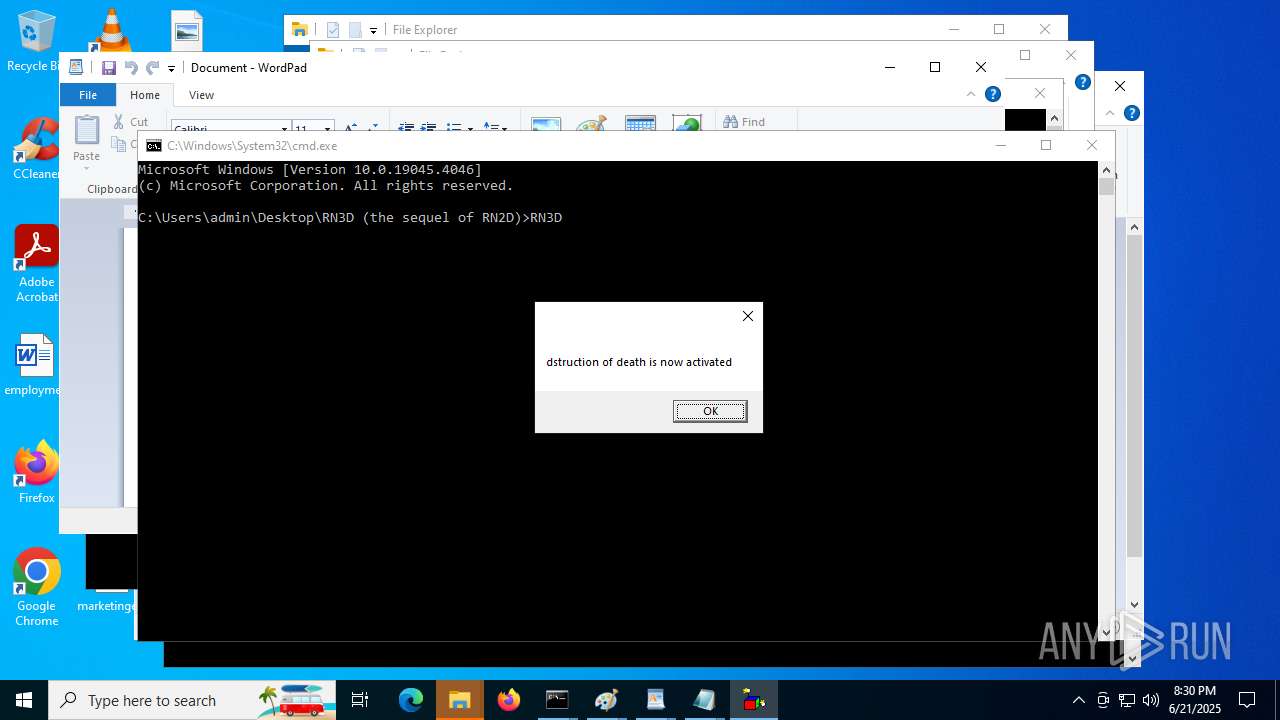
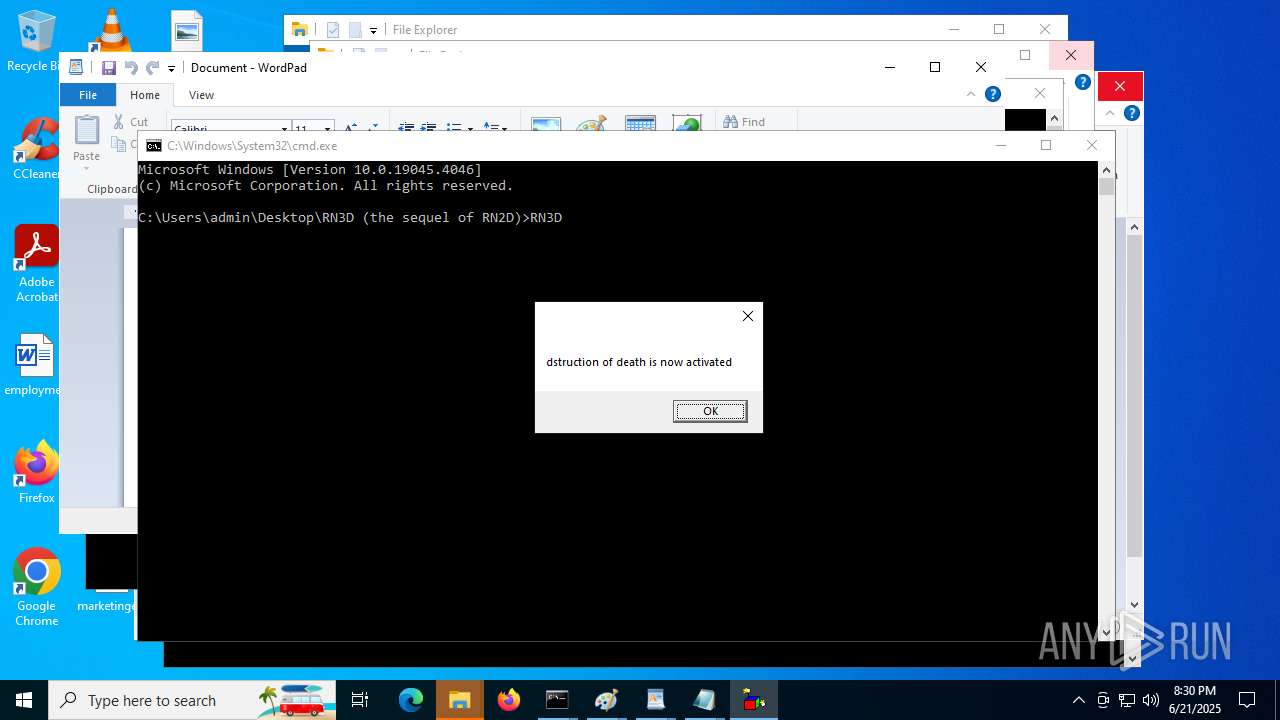
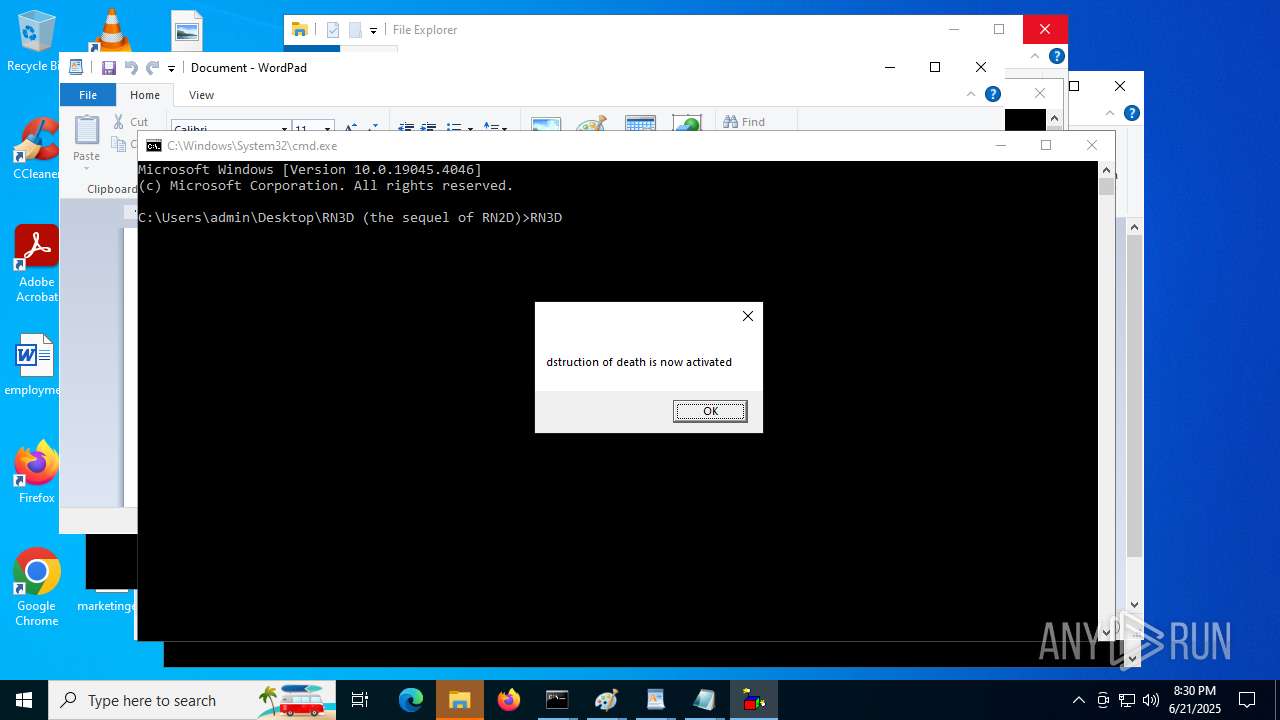
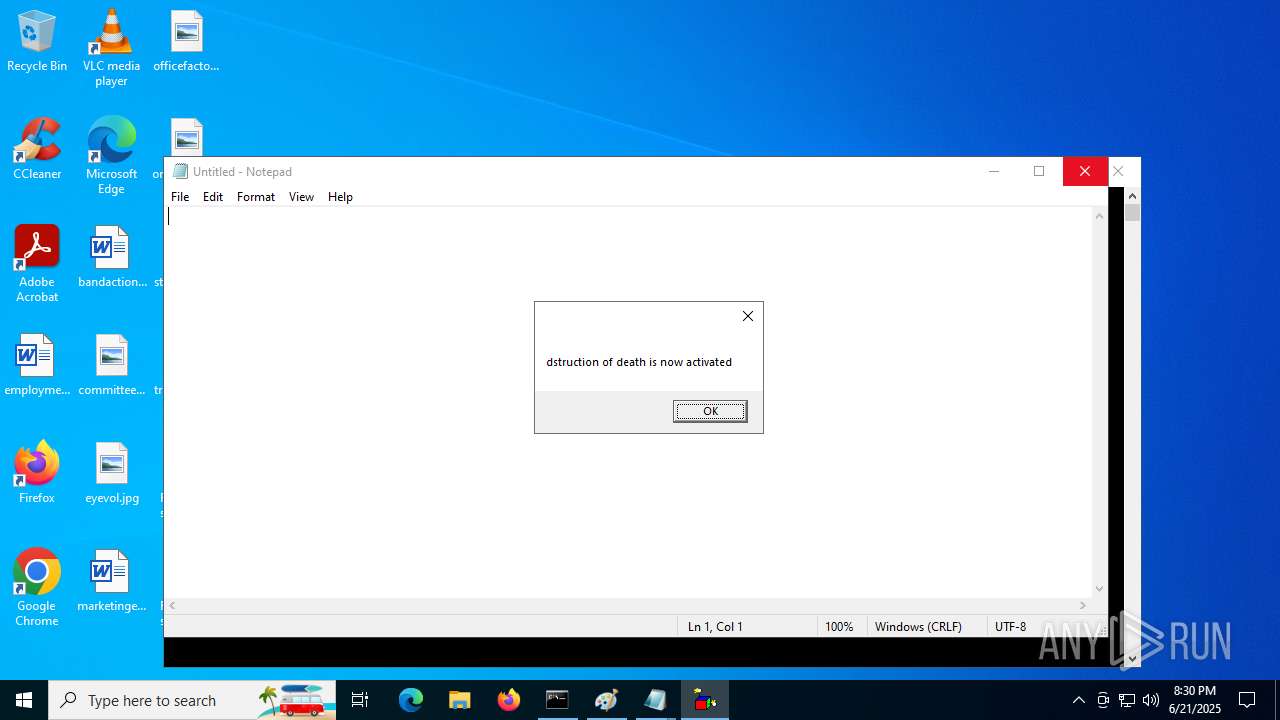
| File name: | RN3D (the sequel of RN2D).7z |
| Full analysis: | https://app.any.run/tasks/ce6ab252-9223-4f48-9bcf-399845dab0fa |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 20:25:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | BBD4D56C04C1426A2B4A4E22FDC6246A |
| SHA1: | BF6DB736158CB629615BD4DBFC2131EB691AAD49 |
| SHA256: | 0012B690896BD096A5F6FD74B3195D076973E490D9FDFA392DE689B178D6C26D |
| SSDEEP: | 49152:xXc5pAConURxlKsqiV7jhfwI87ADBedZRC7XgNJlRTDTnvpO1J2zz567wWaXDMd3:a5+gKsqWNuADYd3CXoJbjvo1J2zzqAXA |
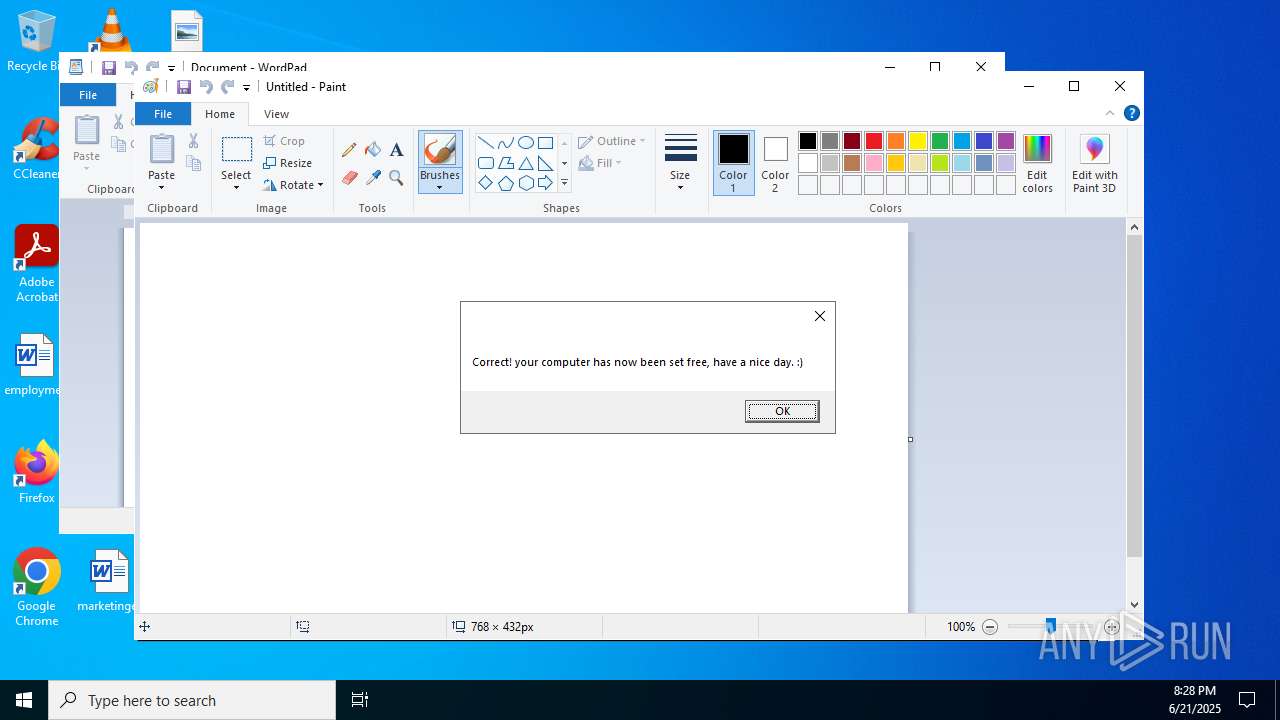
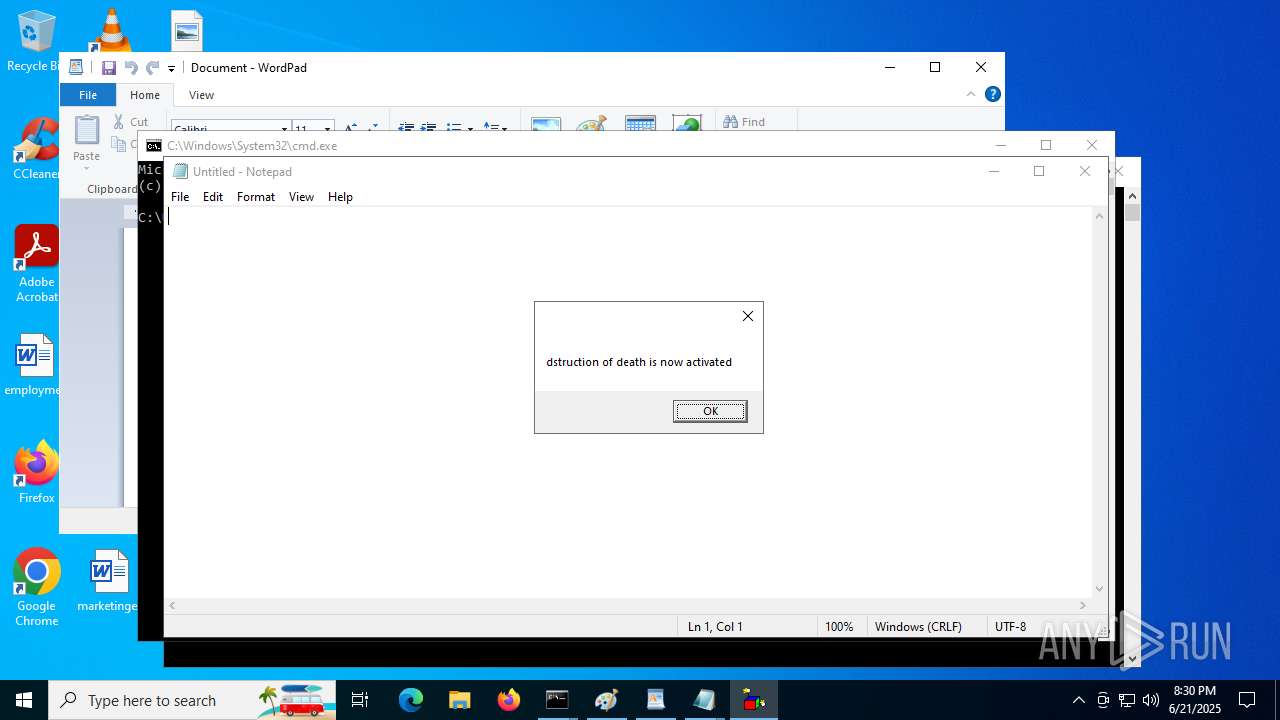
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7100)
SUSPICIOUS
Uses TASKKILL.EXE to kill process
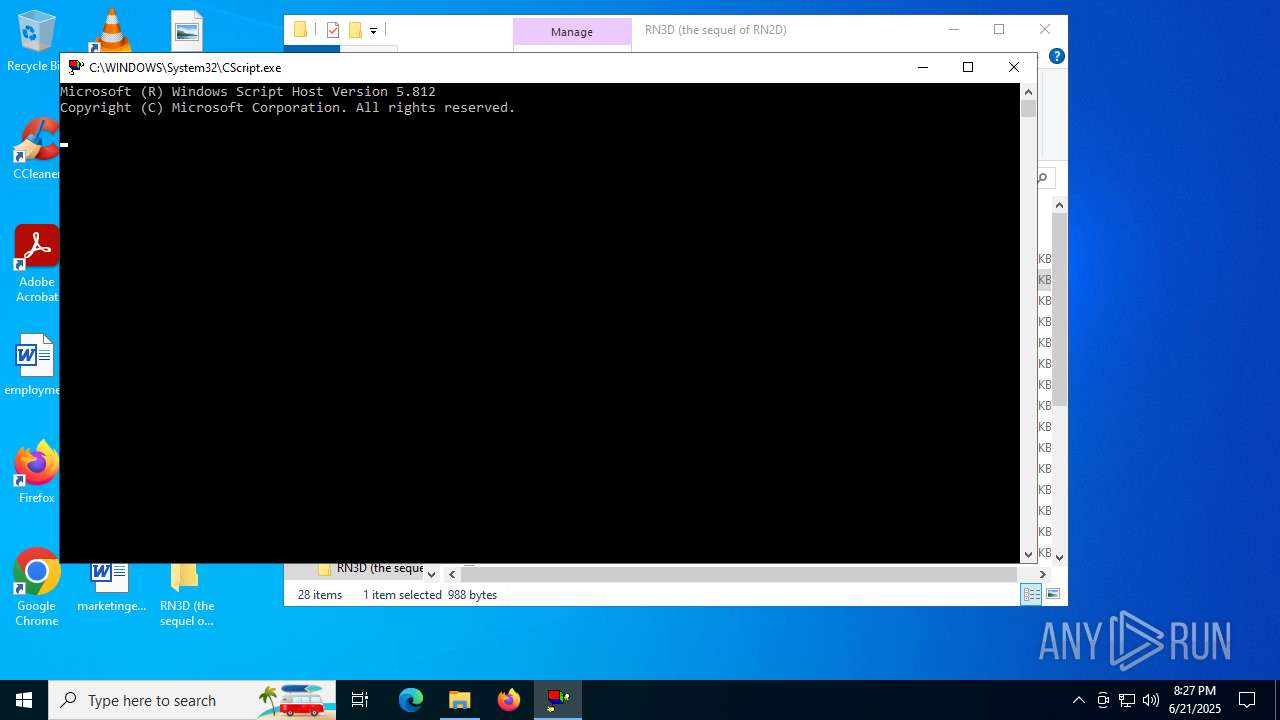
- wscript.exe (PID: 4832)
- cscript.exe (PID: 5480)
- wscript.exe (PID: 5036)
- wscript.exe (PID: 2448)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4832)
- cscript.exe (PID: 5480)
- wscript.exe (PID: 5036)
- wscript.exe (PID: 2448)
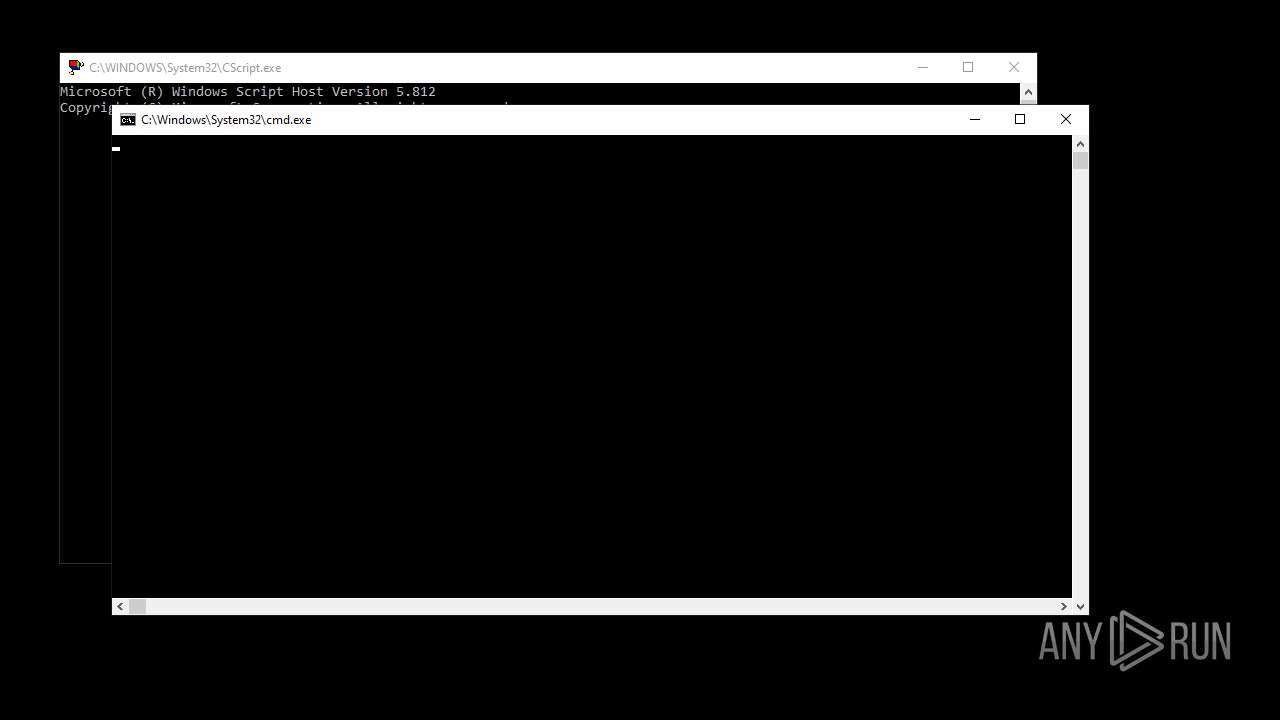
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4832)
- cscript.exe (PID: 5480)
- wscript.exe (PID: 5036)
- wscript.exe (PID: 2448)
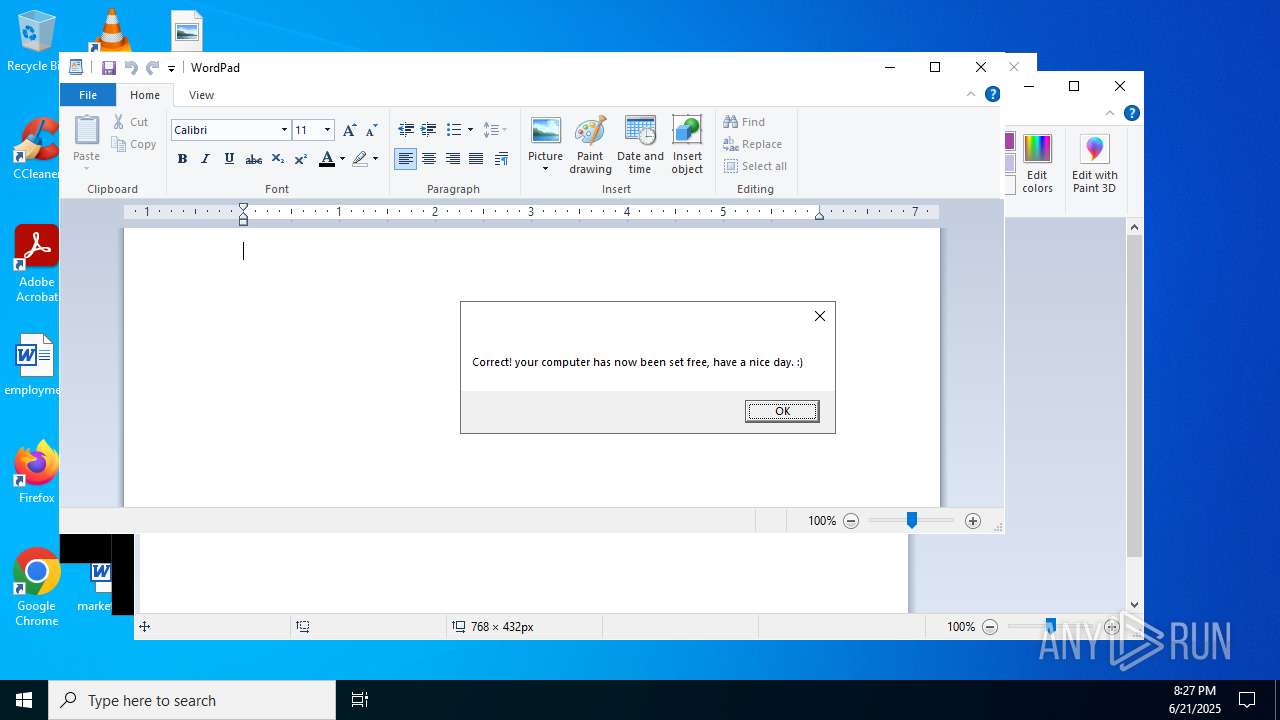
Reads security settings of Internet Explorer
- wordpad.exe (PID: 1036)
- StartMenuExperienceHost.exe (PID: 320)
- wordpad.exe (PID: 1512)
- StartMenuExperienceHost.exe (PID: 6728)
- wordpad.exe (PID: 2864)
- GameBar.exe (PID: 4236)
- StartMenuExperienceHost.exe (PID: 472)
- wordpad.exe (PID: 4680)
- StartMenuExperienceHost.exe (PID: 5144)
- wordpad.exe (PID: 5132)
- wordpad.exe (PID: 4544)
- wordpad.exe (PID: 5092)
- wordpad.exe (PID: 4192)
- wordpad.exe (PID: 1496)
- wordpad.exe (PID: 4112)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 320)
- SearchApp.exe (PID: 5876)
- StartMenuExperienceHost.exe (PID: 6728)
- SearchApp.exe (PID: 4444)
- StartMenuExperienceHost.exe (PID: 472)
- SearchApp.exe (PID: 5952)
- StartMenuExperienceHost.exe (PID: 5144)
Sets XML DOM element text (SCRIPT)
- wordpad.exe (PID: 1036)
- wordpad.exe (PID: 1512)
- wordpad.exe (PID: 2864)
- wordpad.exe (PID: 4680)
- wordpad.exe (PID: 5132)
- wordpad.exe (PID: 4544)
- wordpad.exe (PID: 5092)
- wordpad.exe (PID: 4192)
- wordpad.exe (PID: 4112)
- wordpad.exe (PID: 1496)
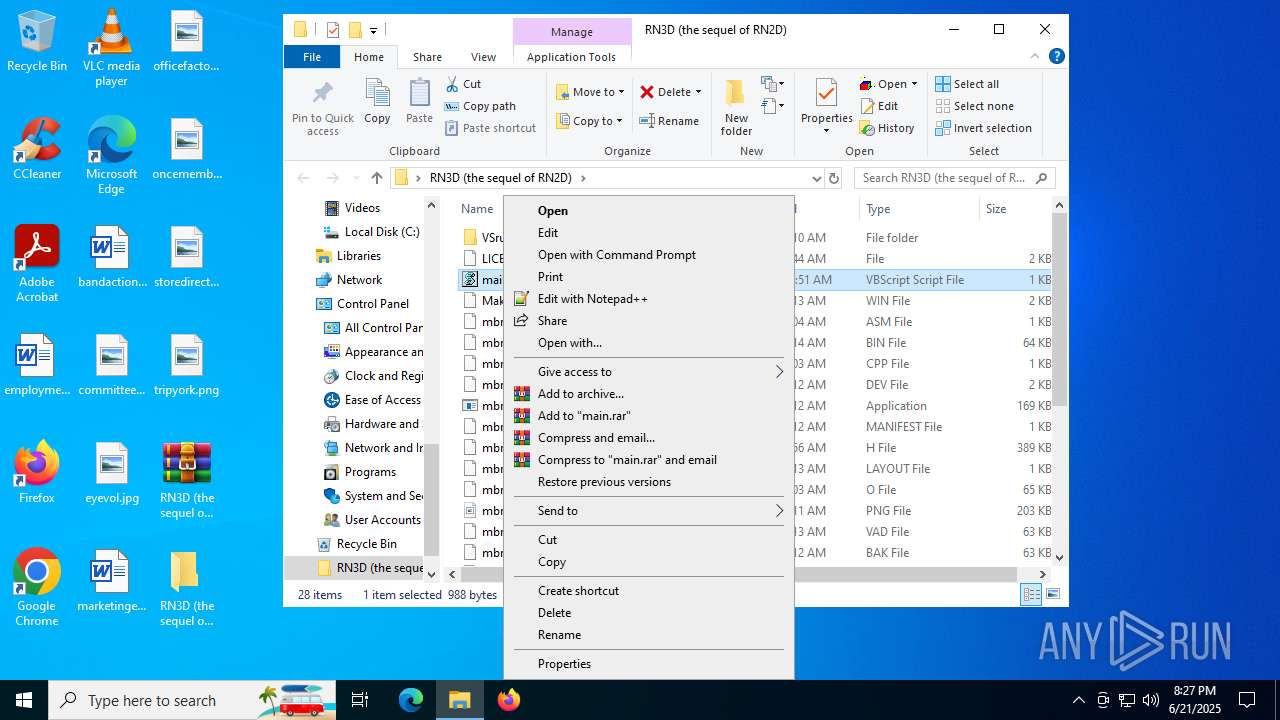
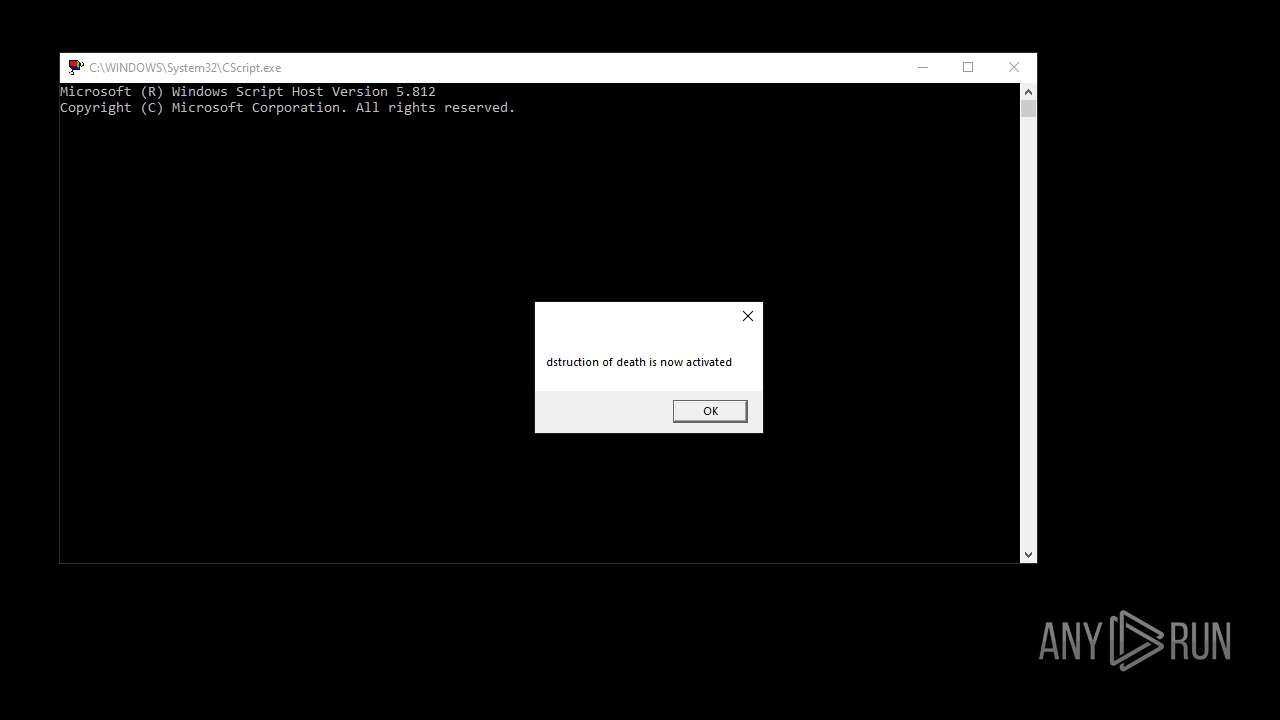
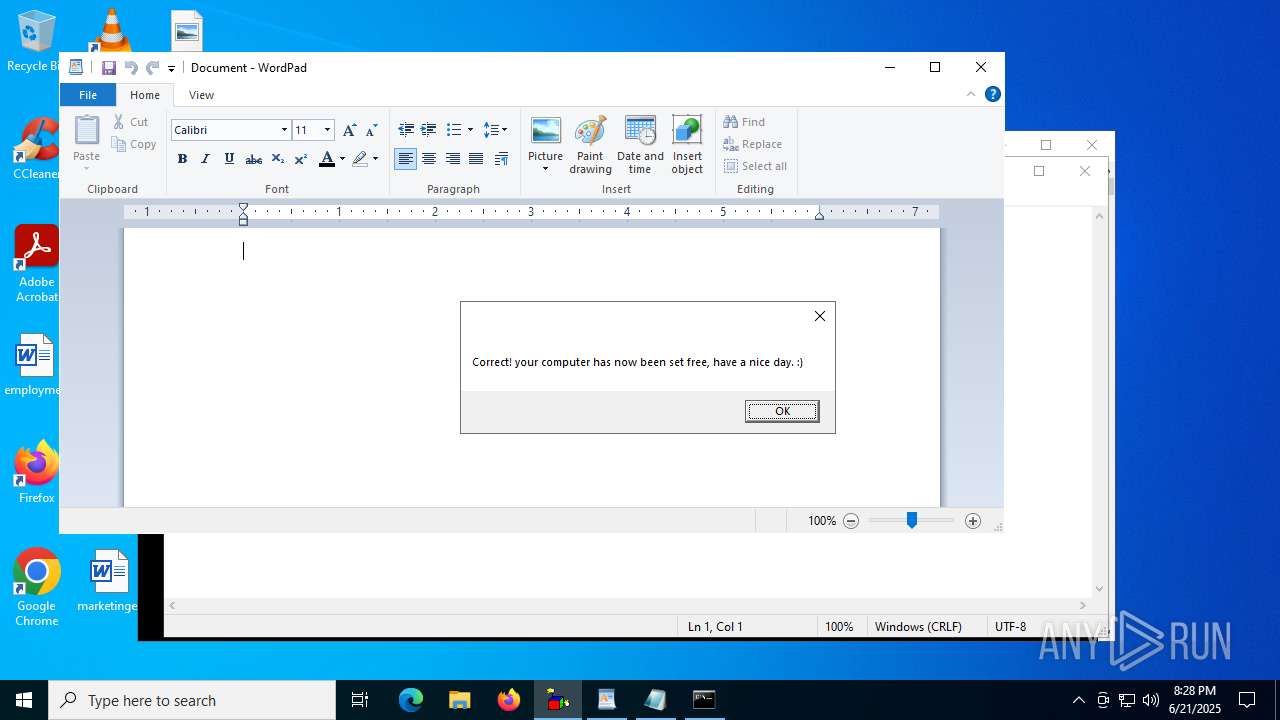
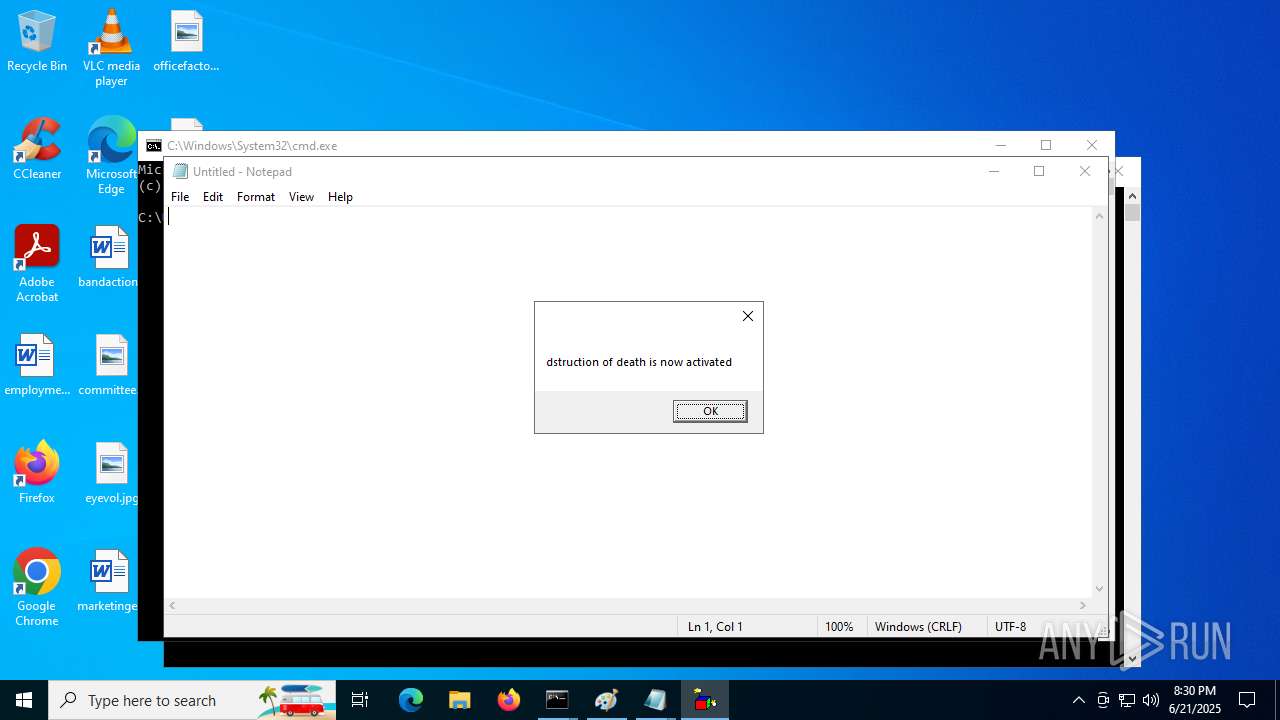
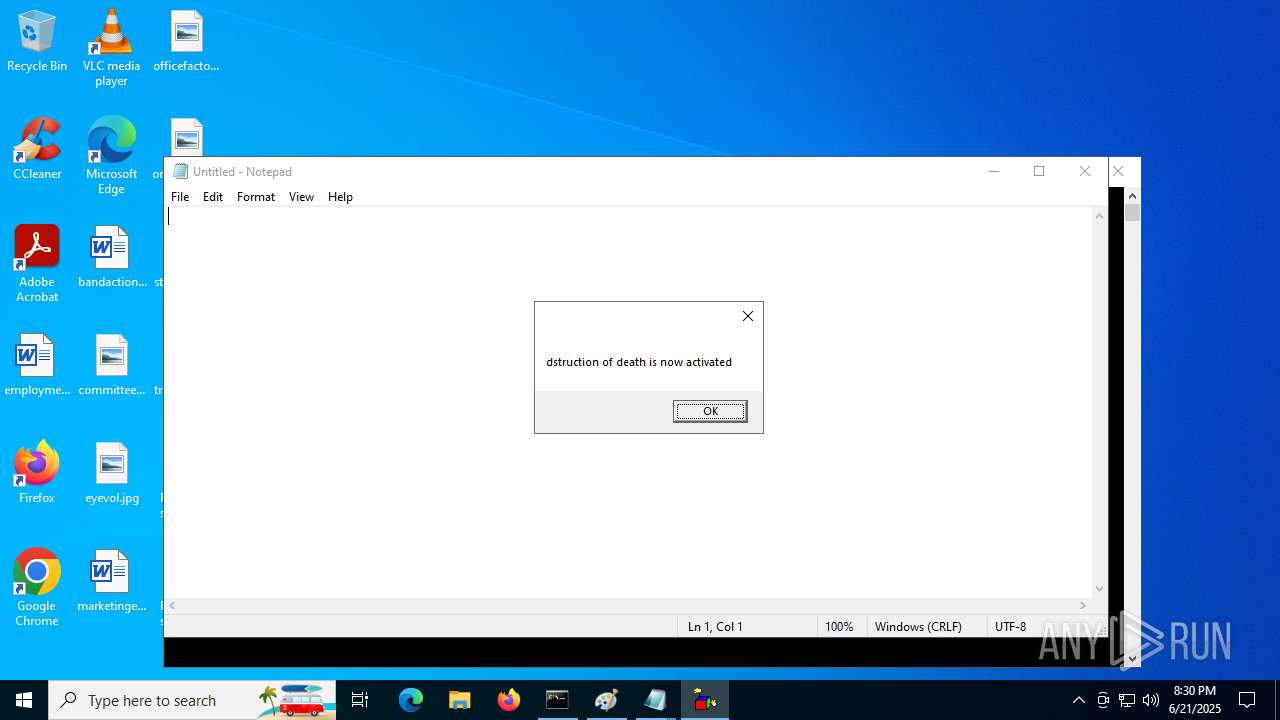
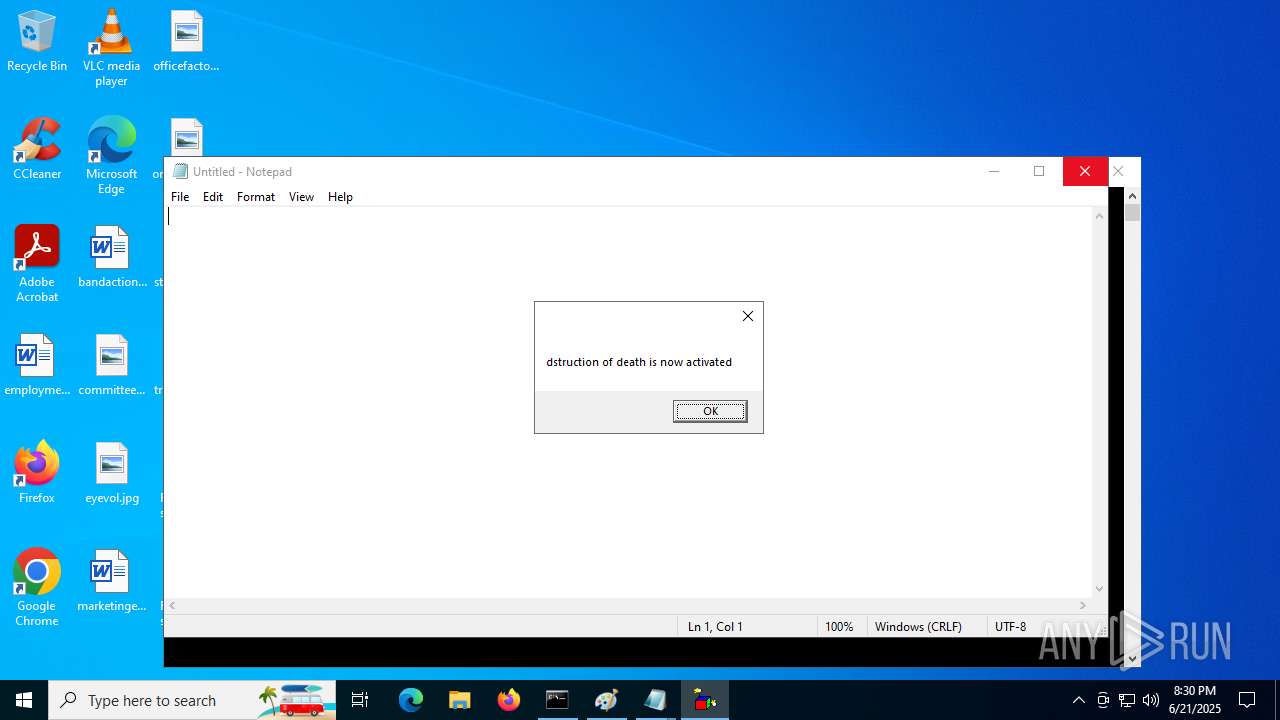
The process executes VB scripts
- explorer.exe (PID: 6936)
- explorer.exe (PID: 1700)
- explorer.exe (PID: 1096)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2512)
- wscript.exe (PID: 4832)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2512)
Reads the computer name
- wordpad.exe (PID: 1036)
- StartMenuExperienceHost.exe (PID: 320)
- SearchApp.exe (PID: 5876)
- wordpad.exe (PID: 1512)
- StartMenuExperienceHost.exe (PID: 6728)
- SearchApp.exe (PID: 4444)
- wordpad.exe (PID: 2864)
- GameBar.exe (PID: 4236)
- SearchApp.exe (PID: 5952)
- StartMenuExperienceHost.exe (PID: 472)
- TextInputHost.exe (PID: 2116)
- wordpad.exe (PID: 4680)
- StartMenuExperienceHost.exe (PID: 5144)
- SearchApp.exe (PID: 504)
- wordpad.exe (PID: 5132)
- wordpad.exe (PID: 4544)
- wordpad.exe (PID: 5092)
- wordpad.exe (PID: 4192)
- wordpad.exe (PID: 1496)
- wordpad.exe (PID: 4112)
Checks supported languages
- wordpad.exe (PID: 1036)
- StartMenuExperienceHost.exe (PID: 320)
- SearchApp.exe (PID: 5876)
- wordpad.exe (PID: 1512)
- StartMenuExperienceHost.exe (PID: 6728)
- SearchApp.exe (PID: 4444)
- mbr.exe (PID: 2660)
- wordpad.exe (PID: 2864)
- GameBar.exe (PID: 4236)
- StartMenuExperienceHost.exe (PID: 472)
- SearchApp.exe (PID: 5952)
- TextInputHost.exe (PID: 2116)
- wordpad.exe (PID: 4680)
- StartMenuExperienceHost.exe (PID: 5144)
- SearchApp.exe (PID: 504)
- wordpad.exe (PID: 5132)
- wordpad.exe (PID: 4544)
- wordpad.exe (PID: 1496)
- wordpad.exe (PID: 5092)
- wordpad.exe (PID: 4192)
- wordpad.exe (PID: 4112)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6936)
- cscript.exe (PID: 5480)
- explorer.exe (PID: 1700)
- explorer.exe (PID: 1096)
- notepad.exe (PID: 4892)
- explorer.exe (PID: 3572)
Reads Environment values
- wordpad.exe (PID: 1036)
- SearchApp.exe (PID: 5876)
- SearchApp.exe (PID: 4444)
- wordpad.exe (PID: 1512)
- wordpad.exe (PID: 2864)
- SearchApp.exe (PID: 5952)
- wordpad.exe (PID: 4680)
- SearchApp.exe (PID: 504)
- wordpad.exe (PID: 5132)
- wordpad.exe (PID: 4544)
- wordpad.exe (PID: 5092)
- wordpad.exe (PID: 4192)
- wordpad.exe (PID: 1496)
- wordpad.exe (PID: 4112)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 320)
- SearchApp.exe (PID: 5876)
- StartMenuExperienceHost.exe (PID: 6728)
- SearchApp.exe (PID: 4444)
- StartMenuExperienceHost.exe (PID: 472)
- SearchApp.exe (PID: 5952)
- StartMenuExperienceHost.exe (PID: 5144)
- SearchApp.exe (PID: 504)
Checks proxy server information
- SearchApp.exe (PID: 5876)
- explorer.exe (PID: 6936)
- SearchApp.exe (PID: 4444)
- explorer.exe (PID: 1700)
- slui.exe (PID: 6828)
- SearchApp.exe (PID: 5952)
- explorer.exe (PID: 1096)
- SearchApp.exe (PID: 504)
- explorer.exe (PID: 3572)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5876)
- SearchApp.exe (PID: 4444)
- SearchApp.exe (PID: 5952)
- SearchApp.exe (PID: 504)
Reads Microsoft Office registry keys
- explorer.exe (PID: 6936)
- explorer.exe (PID: 1700)
- explorer.exe (PID: 1096)
Reads the software policy settings
- SearchApp.exe (PID: 5876)
- SearchApp.exe (PID: 4444)
- slui.exe (PID: 6828)
- SearchApp.exe (PID: 5952)
- SearchApp.exe (PID: 504)
Creates files or folders in the user directory
- explorer.exe (PID: 6936)
- explorer.exe (PID: 1700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2023:11:25 03:12:43+00:00 |
| ArchivedFileName: | RN3D (the sequel of RN2D) |
Total processes
251
Monitored processes
100
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Windows\System32\notepad.exe" | C:\Windows\System32\notepad.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 424 | "C:\Windows\System32\mspaint.exe" | C:\Windows\System32\mspaint.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 472 | "C:\Windows\System32\notepad.exe" | C:\Windows\System32\notepad.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
167 744
Read events
166 224
Write events
1 393
Delete events
127
Modification events
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\RN3D (the sequel of RN2D).7z | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
10
Suspicious files
54
Text files
135
Unknown types
0
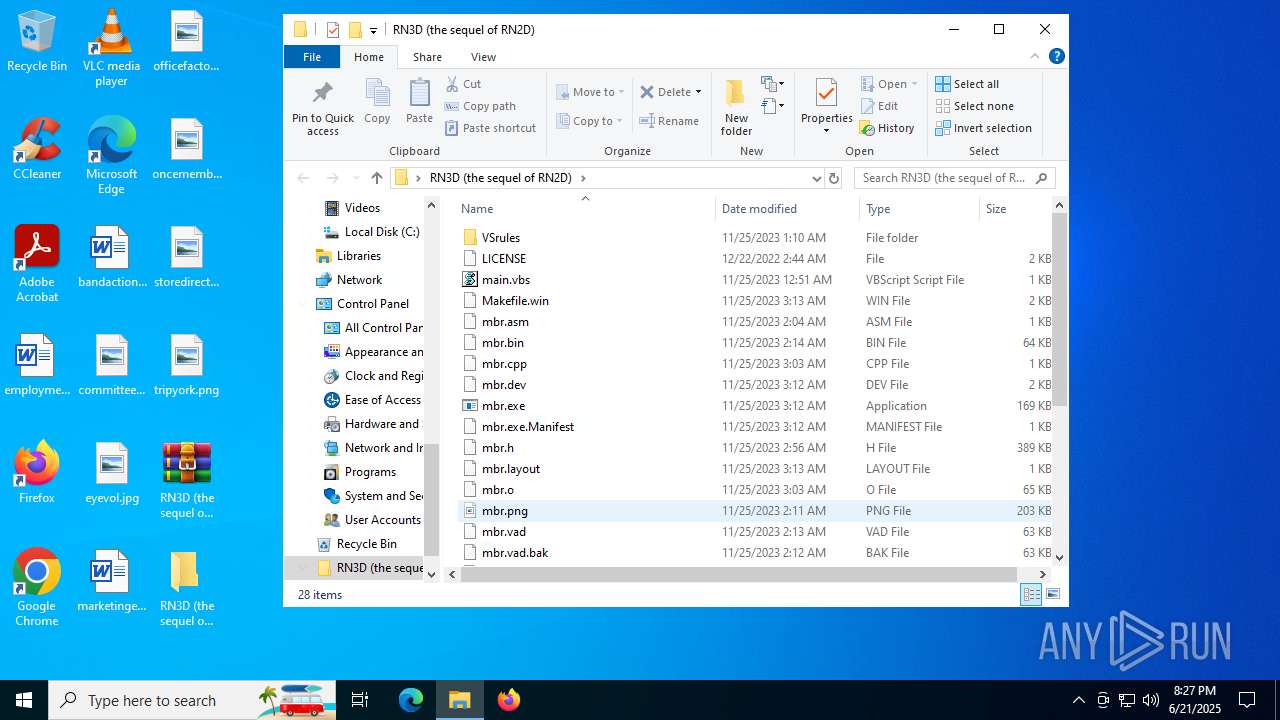
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.vad | binary | |
MD5:E42467978273DBE5046AD773B18DFDDA | SHA256:DA95A84F6880D21B1468E1D20DCDE63834F27E5A4B9B695ABD23AA302A85C0C1 | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.cpp | text | |
MD5:052CFEB2D7DA8FE6A51A95155AA1C9E2 | SHA256:76EC59E9F7A6FC61644FBABBDE28402EE25CC200BDFB98340230006582F451CE | |||
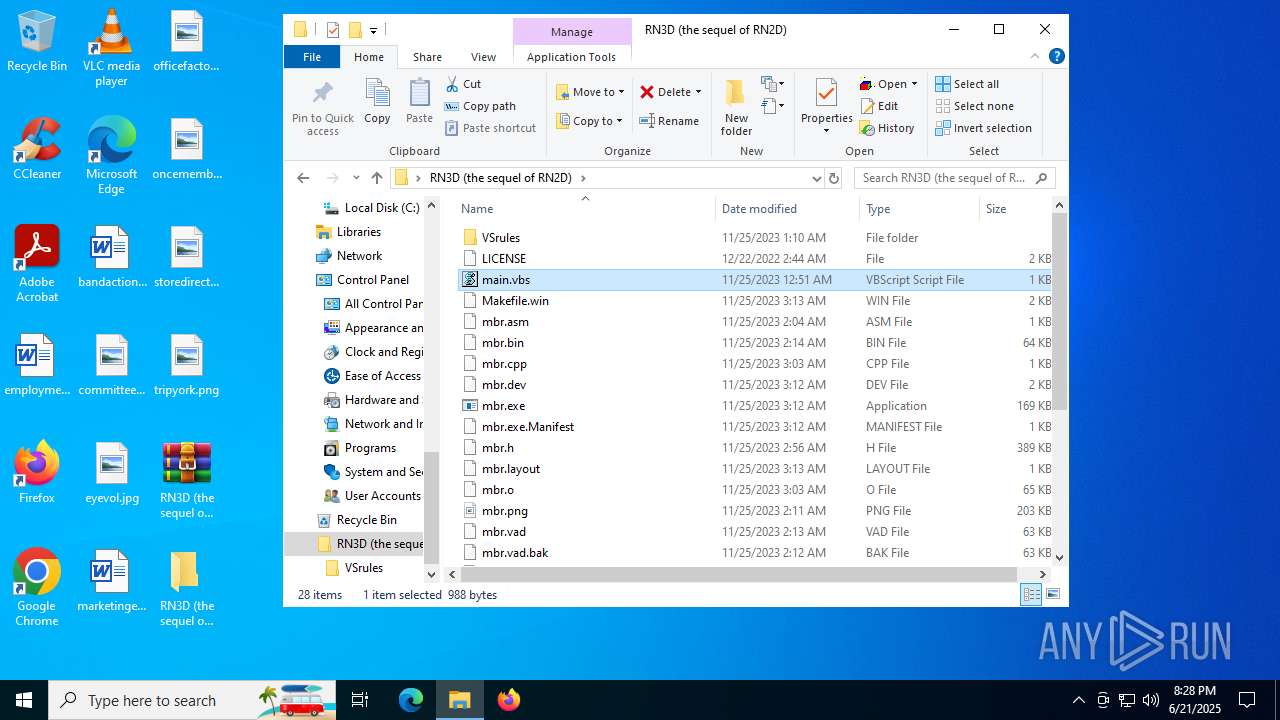
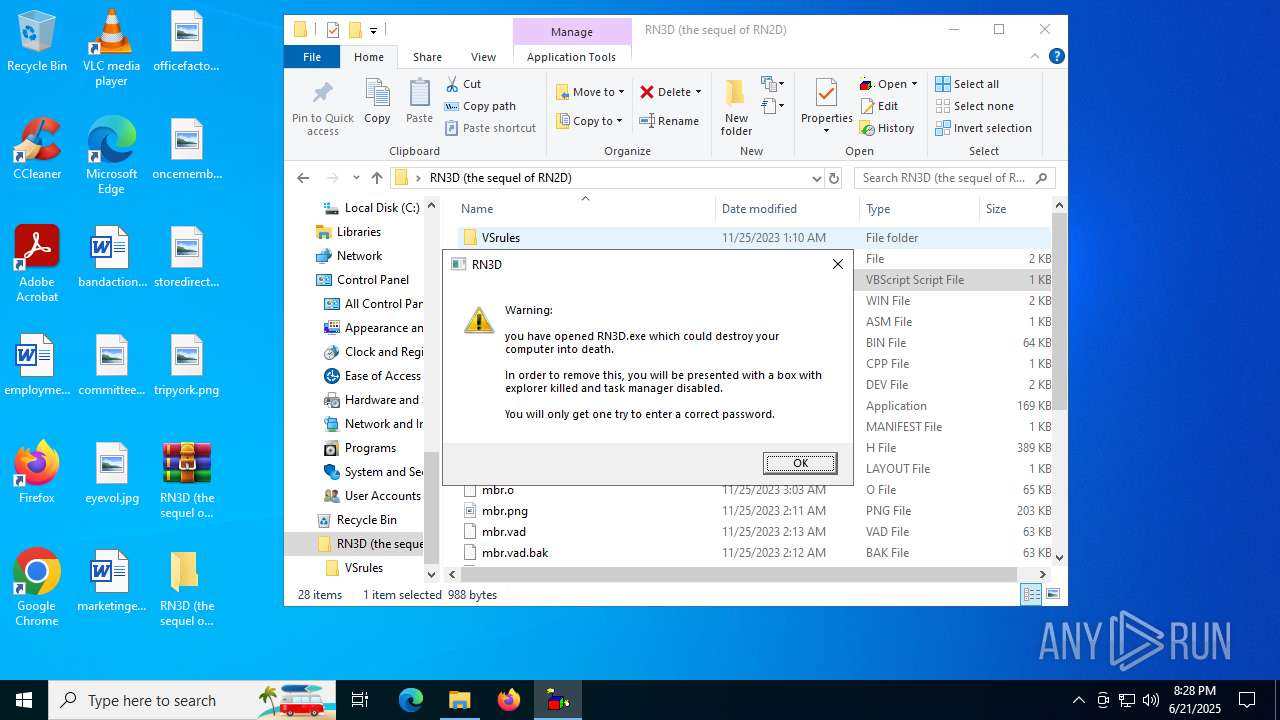
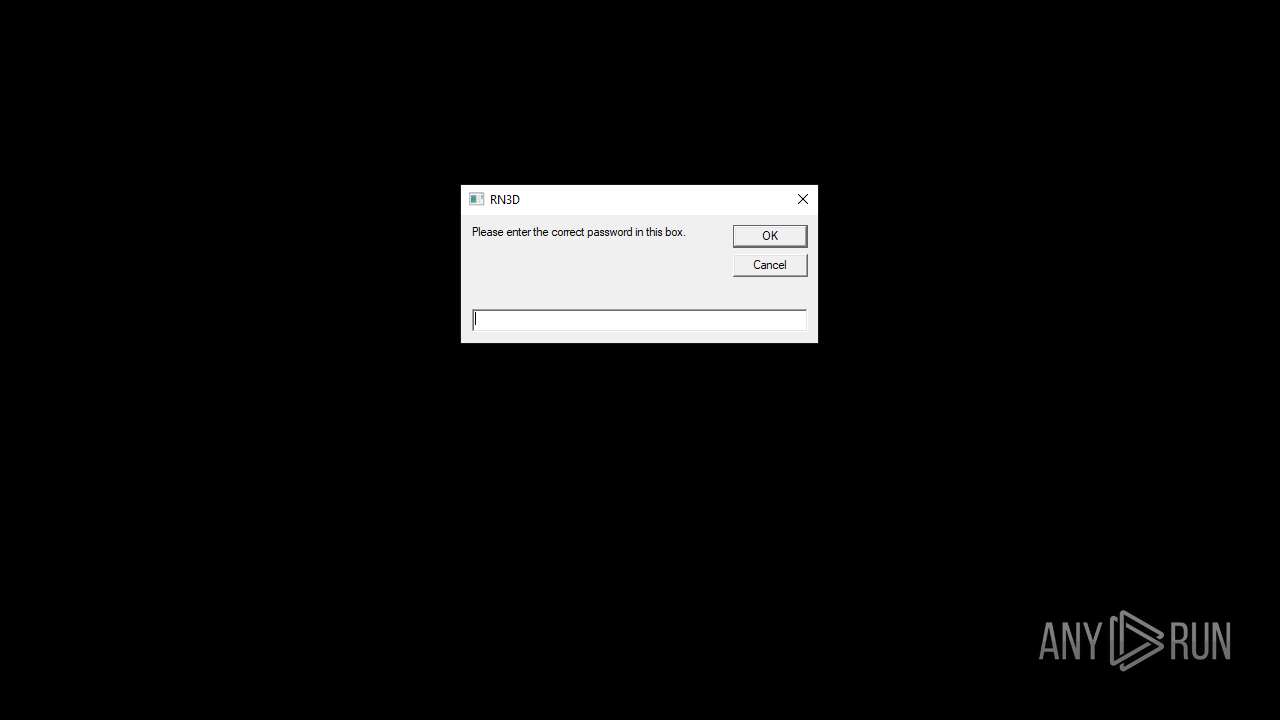
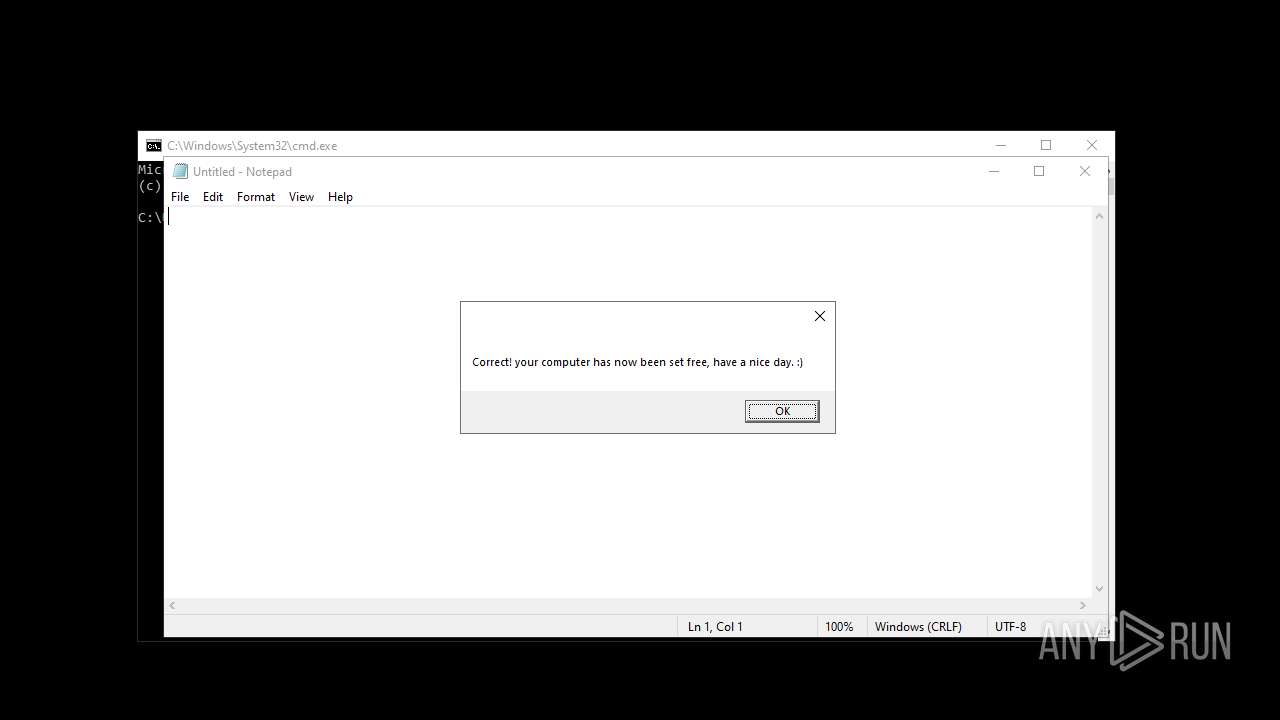
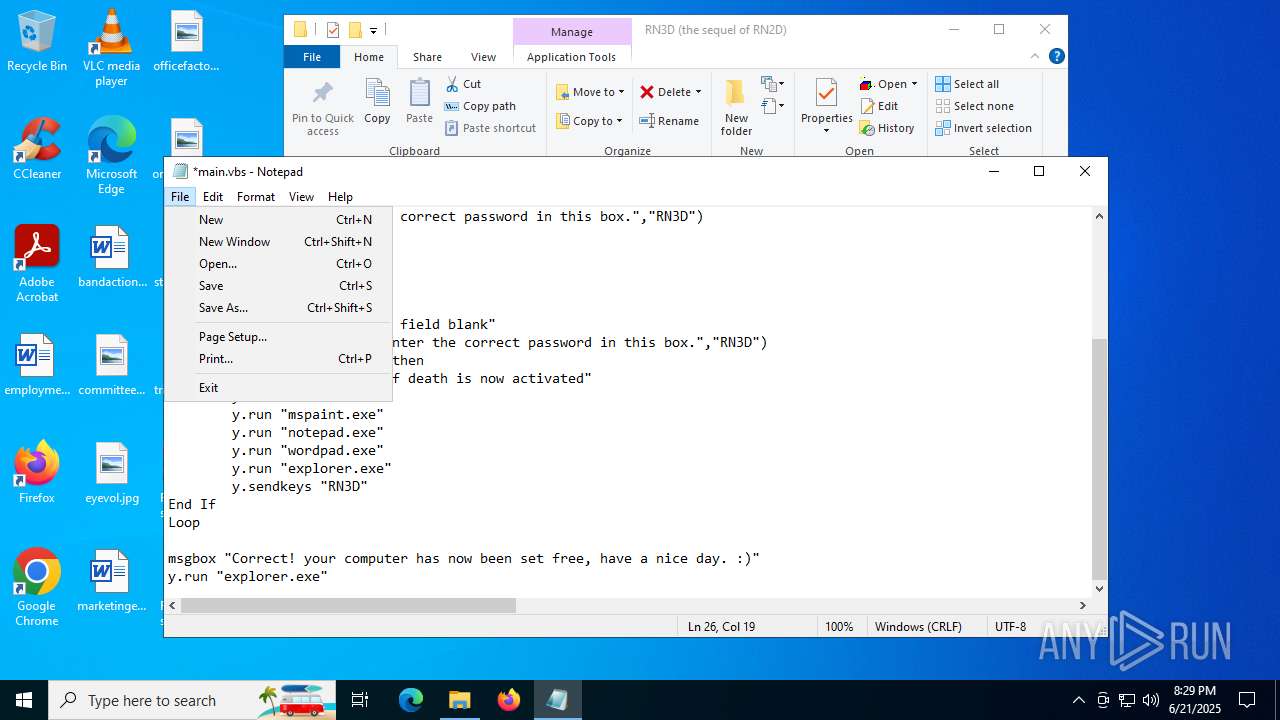
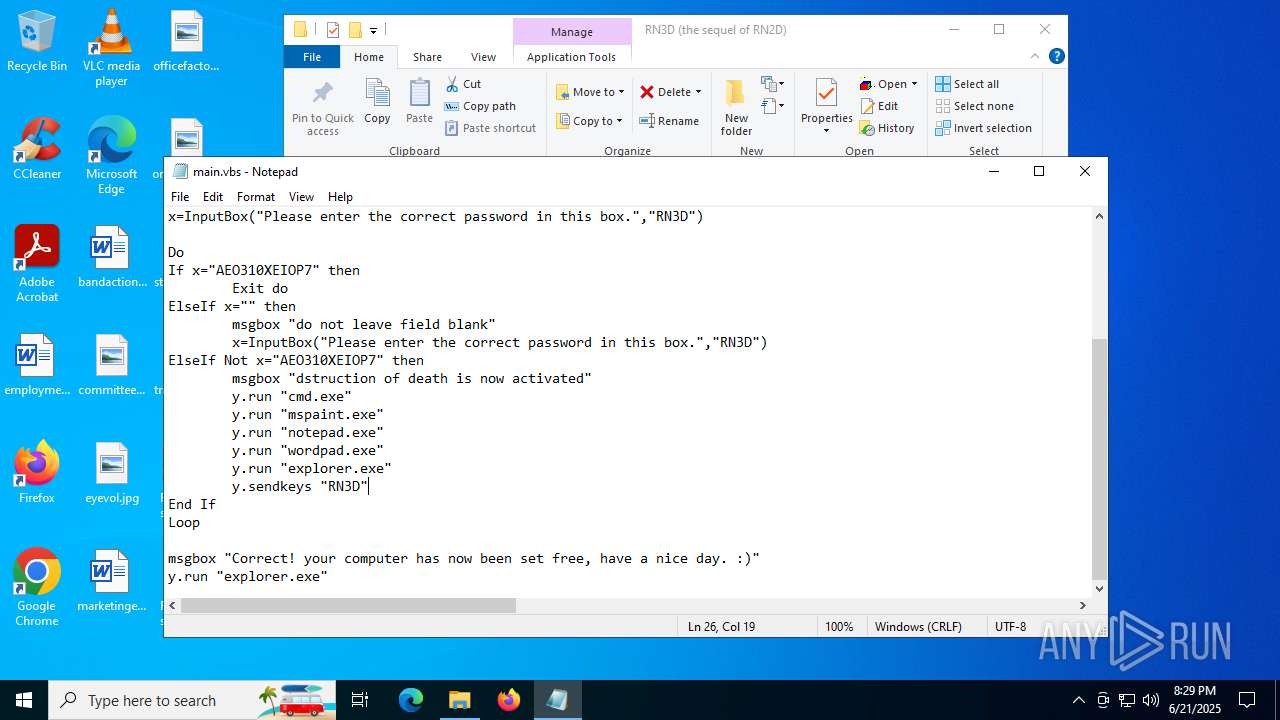
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\main.vbs | text | |
MD5:78723C5AA2FFB1B9B6791252F82DACEB | SHA256:D36852A4AB97613481784BB22CE104207D7DC80B1498965F4C9FEAE189DFB97B | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.layout | text | |
MD5:9C360B71F37640E19EA8C49BAB52E323 | SHA256:CB7AE18D9A8A164C908EC6AD7731584B6B63BB4EA2F7853BF102CA27E06EEA42 | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.exe.Manifest | xml | |
MD5:3A2A377F559C6C8EF47FBDB23E33E14D | SHA256:8CC616384E36815E2A11A4B1F690826501500A55B63D0A72F895CD88036A0258 | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.o | binary | |
MD5:A8D6B9AB0DA25944074D19474CCC6071 | SHA256:3209CDC596ABE823A6D8CEEB11418B357FA07F4AEFB6597273412D675458BFED | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr_private.rc | text | |
MD5:11C009F686EABB36FB7A1A8CDEBE622C | SHA256:FE032BE546543C8CC991B93B3694D58A0A37A6B37F8A088092F10B751E1E2525 | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.h | csv | |
MD5:CA626F16C22EC13D4E24644C1B9F1E8C | SHA256:3A771AB82C371D306214182F33BD79978E262152302362014C52C02FF1E97657 | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\Makefile.win | text | |
MD5:42E855E51762E3C0C7FDD16F7ABE1E75 | SHA256:5E0A6D007DB8941E44AB982EAB9260A585825C89F29A1BE2AB6C7998EDF0D45B | |||
| 2512 | WinRAR.exe | C:\Users\admin\Desktop\RN3D (the sequel of RN2D)\mbr.png | image | |
MD5:3016066378667F76473EE591CE64DE00 | SHA256:D72AC126DD414BF097E0EB2954E90DFE27C8E13DFF0CA1B82C18AA819D2F69A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
45
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.25.50.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5876 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3148 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
728 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4944 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.25.50.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |