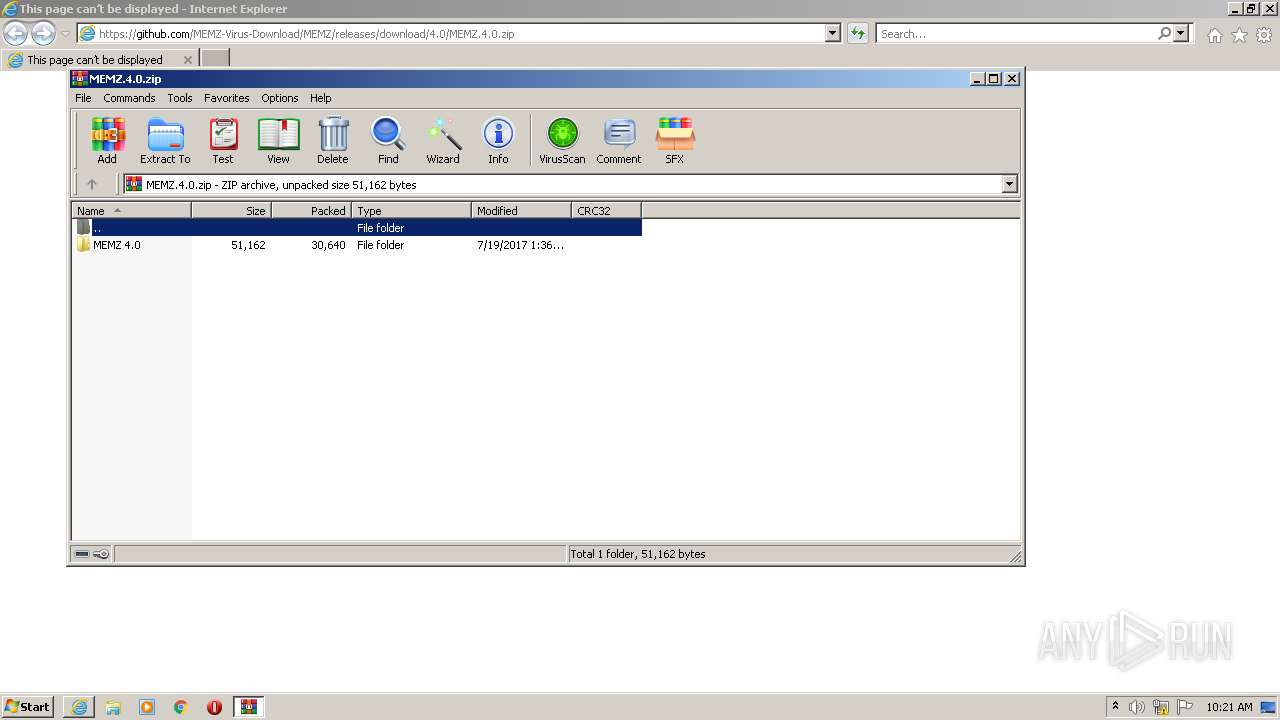
| URL: | https://github.com/MEMZ-Virus-Download/MEMZ/releases/download/4.0/MEMZ.4.0.zip |
| Full analysis: | https://app.any.run/tasks/8defef5b-6ac1-40ca-90bb-f7939c223ad9 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2022, 10:19:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E54736F0EB4C35128EF28DFE22130717 |
| SHA1: | 7E24C7796FEC68470A522F56BEF026CE6AC6E37F |
| SHA256: | 000014FAB79E4FAF28F98AC7762C5E10AFD5617DA6D62745322283EAEE664221 |
| SSDEEP: | 3:N8tEd6jDIjLEE89o//h2kCRhtrU:2ueY+WMc |
MALICIOUS
Drops executable file immediately after starts
- msdt.exe (PID: 2980)
SUSPICIOUS
Drops a file with too old compile date
- msdt.exe (PID: 2980)
Executable content was dropped or overwritten
- msdt.exe (PID: 2980)
- WinRAR.exe (PID: 3240)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 952)
Executed via COM
- sdiagnhost.exe (PID: 3312)
Uses IPCONFIG.EXE to discover IP address
- sdiagnhost.exe (PID: 3312)
Reads the computer name
- WinRAR.exe (PID: 3240)
Checks supported languages
- WinRAR.exe (PID: 3240)
INFO
Reads settings of System Certificates
- msdt.exe (PID: 2980)
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 952)
Reads the computer name
- msdt.exe (PID: 2980)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 3552)
- sdiagnhost.exe (PID: 3312)
- ipconfig.exe (PID: 3604)
- ROUTE.EXE (PID: 2832)
Reads internet explorer settings
- iexplore.exe (PID: 952)
Checks supported languages
- msdt.exe (PID: 2980)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 3552)
- sdiagnhost.exe (PID: 3312)
- ipconfig.exe (PID: 3604)
- ROUTE.EXE (PID: 2832)
- makecab.exe (PID: 524)
Checks Windows Trust Settings
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 952)
- msdt.exe (PID: 2980)
- sdiagnhost.exe (PID: 3312)
Application launched itself
- iexplore.exe (PID: 3552)
Changes internet zones settings
- iexplore.exe (PID: 3552)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3552)
Reads the date of Windows installation
- iexplore.exe (PID: 3552)
Creates files in the user directory
- iexplore.exe (PID: 3552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\system32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft� Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3552 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2832 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\system32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | -modal 131384 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF9E41.tmp -ep NetworkDiagnosticsWeb | C:\Windows\system32\msdt.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ.4.0.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3312 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3552 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/MEMZ-Virus-Download/MEMZ/releases/download/4.0/MEMZ.4.0.zip" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3604 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 251
Read events
18 733
Write events
518
Delete events
0
Modification events
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30935947 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30935947 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
53
Text files
45
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FFE2B1EF54D3783976C57388CB9E1724 | der | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2659C1A560AB92C9C29D4B2B25815AE8 | der | |
MD5:— | SHA256:— | |||
| 952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FFE2B1EF54D3783976C57388CB9E1724 | binary | |
MD5:— | SHA256:— | |||
| 952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2659C1A560AB92C9C29D4B2B25815AE8 | binary | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\NDF9E41.tmp | binary | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
34
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
952 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceTLSHybridECCSHA2562020CA1.crl | US | der | 292 b | whitelisted |
3552 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
3552 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 631 b | whitelisted |
952 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
952 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?87a8952d00f0e2ad | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
952 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
952 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3552 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
952 | iexplore.exe | 185.199.110.133:443 | objects.githubusercontent.com | GitHub, Inc. | NL | malicious |
3552 | iexplore.exe | 104.111.242.51:443 | go.microsoft.com | Akamai International B.V. | NL | unknown |
3552 | iexplore.exe | 131.253.33.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
3552 | iexplore.exe | 40.83.186.94:443 | query.prod.cms.msn.com | Microsoft Corporation | US | whitelisted |
— | — | 140.82.121.4:443 | github.com | — | US | malicious |
952 | iexplore.exe | 140.82.121.4:443 | github.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
680 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |