Bank robbery is one of the most classic and old crimes in history. Though the goal of robbers hasn’t changed over the years, the modern Ocean’s Eleven is hiding behind the screen and has upgraded its methods. The evolved techniques put banking cybersecurity specialists on the edge of their seats.
Twitter’s posts like this one are the usual story in the news feed. It is one more proof that the finance sector is a common target for hackers.
Rapid digital transformation of the financial organizations and the effects of the lockdown have become the reason for the sector’s attack surface to expand considerably, exposing companies to increased levels of cyberthreat activity.
To protect banks from cybercriminals, you should know what threats you might face and how to fight and prevent them. Read on to find out all about it.
Top 6 banking cyber threats

1. Malware
Trojans, RATs, spyware, and ransomware are the malicious programs that take part in the banking outbreak. These types of malware get unauthorized access, cause data leakage, exploit vulnerabilities.
2. MITM attack
In a man-in-the-middle scheme, crooks impersonate one of the sides of a two-party transaction, manipulating or stealing data or transfers. MITM can be the infiltration step of the Advanced Persistent Threat (APT) attack.
3. XSS attack
Criminals try to compromise financial companies by a cross-site scripting attack. During the pandemic in 2020, the usage of online banking services rose. Threat actors fake banking websites and mobile applications by changing their appearance to trick customers into disclosing their credentials. XSS technique also can be a part of phishing.
4. Phishing
Spearphishing, the most common type for the finance sector, is a targeted attack that causes data breaches. Phishing attacks may imitate trusted senders, using social engineering tactics to gain a victim’s credibility. After gaining access, attackers get credentials and entry into a system.
5. A zero-day exploit
It is a threat actors’ practice of attacking systems with a prematurely unknown vulnerability. The main goal is to compromise personal bank accounts and capture log-in credentials.
6. DDoS attacks
Attackers flood bank servers with junk traffic, preventing users from online banking, slowing down website response is also in their focus. The websites of U.S. Bancorp, JPMorgan Chase, Bank of America, PNC Financial Services Group and SunTrust Banks, and other financial institutions suffered outages due to a coordinated denial of service cyberattacks. According to the latest report by Radware’s Threat Research team, in Q1 of 2021, DDoS attacks have a 30% increase in volume. And this tendency isn’t new, as we can see from the F5 Security Incident Response Team’s review:
The analysis of 729 public breach notification letters from the United States in 2020 allowed us to get the results and find out the most common types of data breaches.
Types of Data Breaches in Banks
| Ransomware | 31% |
| Third-Party Breach | 24% |
| Business Email Compromise | 27% |
| Cloud Breach | 17% |
| Web Exploit | 16% |
| Phishing | 8% |
| Mobile Exploit | 0.10% |
These cyberthreats can destroy the reputation and compromise the confidentiality of sensitive data. Data breaches could cause severe economic losses.
What can banks do?
Here are just a few methods you can adopt to safeguard finance processes and data as well as to defend against potential cyber threats.
- Participate in red and blue team exercises regularly.
- Be aware of emerging threats. The sharing and employment of cyber threat intelligence across the financial services sector are essential. If you understand yourself and your enemy, you can win any battle. (c) Sun Tzu
- Detect and analyze threats fast. Detailed investigation of malicious files and instant results enhance the security program and incident response time.
- Create robust remote work policies and staff education on cybersecurity awareness to prevent attacks. Give employees tips on how to recognize scams and keep the company’s cybersecurity strong.
- Analyze every user’s action on working stations. Restrict file and directory permissions
- Introduce multi-level password policies. 2FA, USB keys, and others guarantee the safety of the files. However, you need to keep in mind the employees’ convenience and don’t go overboard here.
- Establishing a strong outer perimeter by traffic monitoring. Use proxy servers, border router set-up, network traffic analyzers on different levels, and control of inbound and outbound traffic.
- Validate compliance with the PCI DSS license: the network segmentation, traffic encryption, limiting administrative privileges, server protection.
- Get a cybersecurity analyst to take part in all processes: from implementing new features, launching a site or an application to restoring the backup.
- Update servers and security patches constantly.
- Establish backup channel access.
- Filter emails.
- Set a separate server for malware analysis.
- Analyze requests on application and network layers (according to the OSI model) to avoid DDoS attacks.
- Encrypt and backup data: It is essential to secure the data of banks as thousands of customers do transact on the bank’s websites. The bank website must have an SSL certificate to avert data breaches.
We also asked our fellow malware analyst, Yasmine Johnstoon-Ison, for a piece of advice:
Banks face a multitude of security situations. They are a great example of an organization that can benefit from a Cyberthreat Intel team (CTI).
A CTI team would be able to:
- identify a wide range of risk/threat avenues a threat actor may take to exploit the bank. – track known threats and be proactive with detections and hunting.
- use actionable intelligence to hunt for unknowns.
- take apart malware that has hit the bank, banking systems, POS systems, and sites.
- tie back to a threat actor and identify the chain of infection, knowing the chain of infection could possibly identify the root cause of the infection. The IR (incident response) team could then remediate the issue so it doesn’t happen again, or the bank could weigh the risk.
- help with malicious email campaigns that aim to steal user credentials.
- investigate if the campaigns use any known TTPs (tactics, techniques, procedures) leading back to an actor/group.
- identify the root cause of the incident.
In the military, there is a saying, “staying left of the boom”. That is the job of intel – to keep informed and stay very much to the left. But also, when an incident goes down, a CTI team would be able to provide the IR team with actionable intel to handle the incident, quickly and efficiently.
Equipping the CTI team with the right tools will make their job easier and allow them to protect the bank better. They are very vital and keep your cybersecurity stance proactive and forward-thinking.
13 tools to improve bank cybersecurity
- FS-ISAC provides information that increases sector-wide knowledge of cybersecurity threats. It is solely focused on financial services.
- Splunk collects logs, events, and journals.
- Thycotic reports on all employee’s actions, manage admin rights.
- Passbolt and Keypass store passwords and allows their safe sharing.
- Zabbix monitors networks, servers, VMs, and cloud services.
- Wireshark and PRTG analyze the network.
- Kaspersky, McAfee, and Trend Micro monitor Windows.
- Squid is a caching proxy that reduces bandwidth and improves response times.
- Qrator provides automatic DDoS attacks mitigation.
- Qualys automates checks of security controls and configurations.
- Webex is a safe corporate messenger.
- Cisco Secure Email detects, quarantines, investigates and remediates cyberattacks that target your email.
- ANY.RUN helps to analyze malware, including ones that explicitly target Internet banking customers. A bonus to the ability to investigate suspicious files and links is a vast database of relatable threats for later scrutiny. Banks and large finance companies already use this service every day.
How can a bank employee check a suspicious link or file?
A bank employee’s day is busy enough. Paperwork, money transfer, recalculations, a compilation of reports. Customers with demands and colleagues with requests. And the most common way to deal with all of it is by email. And here comes a trick.
How to be sure that the email you got is not a scam? Here are few ways to get that something wrong is going on:
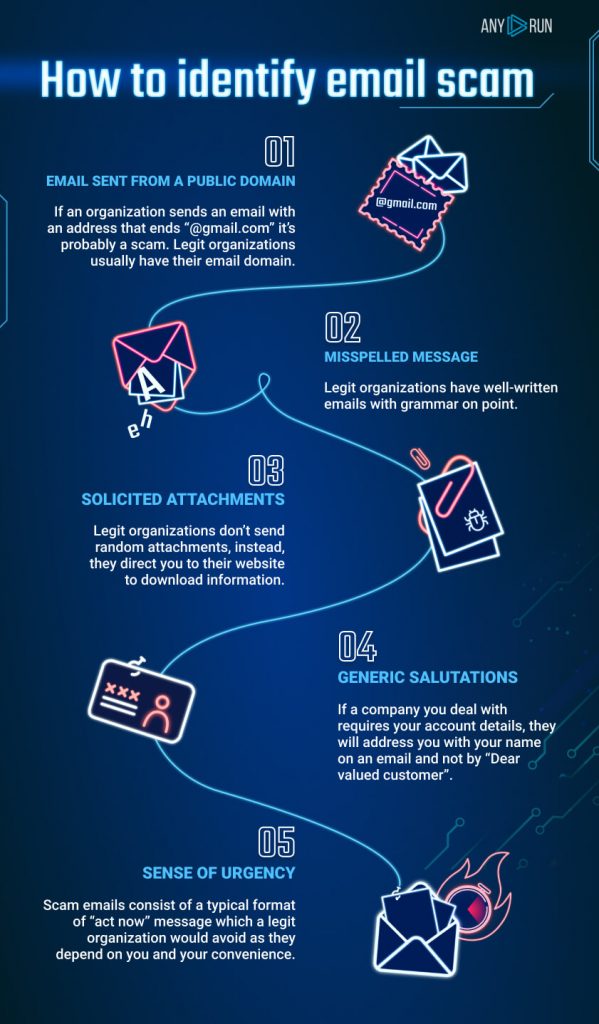
Now you know that the email you got has a surprise. Let’s find out whether it is malicious or not.
Phishing sites use graphical decoys of well-known brands. In the first sample, an email contains files that we are offered to open with Office, and it looks like a legit Microsoft theme. But it’s a fraud. After the user has given his credentials, a phishing website usually redirects the user to the original website. If you check the file beforehand in ANY.RUN service, you will see its malicious intentions in less than 2 minutes.
Another example will show you a different story. A so-called colleague sent you a report for recalculation. You opened a file and didn’t even notice that malware had already stolen your data. Definitely, not a happy end.
Let’s try one more time. Your internal Sherlock Holmes supposed that it was malicious spam with an attached malicious document. And you decided to reach the interactive sandbox. The instant result of the analysis showed you the whole process that was invisible to you before. The maldoc used CVE-2017-1182 vulnerability to download a payload by Equation Editor. After Formbook malware was downloaded, it injected the Explorer process and started stealing information from the infected system, that in another scenario, was yours. But this time, knowing the verdict, you can protect data and delete the email at once.
To infect the system, a user just needs to open a malicious document on his unpatched system.
Security of data is not only a company’s problem. Each employee should be aware of how to prevent suspicious activity and protect private data.
We bet you got tired of all these nagging about being careful and these notorious rules. Let’s have a look at them from another side, what happens if you don’t follow them? Here are our Harmful Tips for Cybersecurity, just for laughs.

But remember there’s a grain of truth in every joke. But a joke is the best way to remember things. So, feel free to print it for your office or working space. Here you can download the file: https://any.run/media-files/articles/harmful-tips.pdf
We swear it’s safe! But you know where to check it now, right?
Conclusion
Sophisticated attacks threaten data leakage, theft, and privacy violation – everything that finance organizations need to prevent and fight against. The best heist movies can’t reflect what a battle is going on behind the monitors. And the blue screen doesn’t show who the real superheroes are, but we know them: the ones who keep the data safe.
Samples that you can investigate:
Ransomware sample – https://app.any.run/tasks/9510f158-56e0-49a4-ba1a-b02f4f4b97b5
Stealer sample – https://app.any.run/tasks/08824087-dc42-46d8-8738-326be5d3213f
Phishing sample – https://app.any.run/tasks/2e2e261b-6d38-4be8-8e7b-df0ca7dfd541/
3 comments







Awesome article.
Nice blog!
I read this post completely on the topic of the comparison of latest and previous technologies, it’s
amazing article.