Cyber attacks get more personalized, and malware authors trick victims using individual approaches. Such campaigns adapt malicious programs to the attacked country: using local language, services, currency, and others.
In some cases, the geofenced malware won’t start execution if it detects the OS’s language or IP of a non-targeted country. Today we will discuss how to analyze location-based malware in ANY.RUN.
Why does malware aim at geolocation?
Hackers never seize to surprise us with their sophisticated and malicious methods. Unfortunately, this creativity hits the ground, and victims fall into their trickery.
Malware’s goal is to imply all possible ways to impersonate legitimate software. Among the others is geolocation. When a user launches a program and speaks with them in their native language, it creates common ground and builds trust.
Here are other reasons why malware creators aim to create geo-located malware:
- infects computers more effectively with localized phishing campaigns
- attacks the specific country or region
- evades detection longer
Let’s discuss the types and how to analyze these narrowly specialized malicious objects.
How does geofenced malware work?
Cars, clothes, and food brands usually localize their marketing campaigns, adapting products to the specific region for distribution. Hackers quickly picked up this trend and started to design malware to get highly successful attacks.
Geo-targeted malware can check the geolocation of the infected host to avoid delivery in non-target countries. It means you won’t get a payload during analysis if your malware analysis environment is not from the targeted country.
Here is a usual scheme of how geofenced malware work:
1. Distribution
Cybercriminals can put bank malware on computers in any region they prefer. It may be a rich country or just where crooks have opportunities, such as recruiting people to take money from the local ATMs using card numbers and PIN codes stolen by malware or skimmers.
There are many cases when criminals go to the black market to use compromised Traffic Direction Systems (TDS) that provide bets online and traffic direction to find the most suitable victims. That is similar to legal advertising networks that provide the most relevant ad every time you visit a website.
According to the Kaspersky research, here is the percentage of users who experienced faced the financial threat in different countries during 2021:
Countries attacked by banking malware
| Country | % |
| Turkmenistan | 8.4 |
| Afghanistan | 6.7 |
| Tajikistan | 6.6 |
| Uzbekistan | 5.7 |
| Yemen | 3.1 |
| Paraguay | 2.9 |
| Costa Rica | 2.7 |
| Sudan | 2.4 |
| Kazakhstan | 2.2 |
| Syria | 2.2 |
2. Adapting
How does a compromised web server work? It identifies your IP address that often shows your computer’s location after sending malicious data. And finally, you turned out to be using the malware “designed” for your region.
Crooks prefer this type of IP address identification using banking malware. Most of them work with a defined country or region. For example, German users are likely to be Deutsche Bank users. And malicious programs targeted at this bank could reach a high success rate.
3. Theft
Most geo attacks aim at financial data theft. Several malware types help reach this goal. Banking trojans, ransomware, and RATs are explicitly designed for this need. Also, different regions are attacked by specific malware families. For example, Dridex is frequently used in the USA and Germany; Ursnif prefers Italy.
How to analyze geo-located malware
There are a few ways to detect geo malware in ANY.RUN. Let’s go through them using samples from public submissions.
We can start by using the Network Geolocation feature. It allows analyzing malicious objects from a wide list of countries. You can turn on Tor or add your own VPN configuration. Moreover, HTTPS MITM proxy and FakeNet are helpful, too.
1. HTTPS MITM proxy
Analyze samples using cryptographic protocols designed to provide communications security, such as SSL and TLS. It allows you to save complete HTTP conversations for later analysis.
With the HTTP MITM Proxy option, you can use the route via Tor, but only with the fastest geolocation.
Today we have a phishing sample. It’s a popular technique designed to steal victims’ financial information. Thanks to the legit-looking design and a complex delivery method with social engineering, this is one of the most successful cyberattacks. And in most cases, phishing malicious emails and files track your geolocation.
If we open this website that looks trustworthy, the authorization window offers to input a password there. And if you do so in the secure environment, then in the HTTP requests, we can see a request with a special log-file record – this is our password.
In the Connections tab, we can see malware using the 443 port to interact with the network.
Because malware uses a cryptographic protocol for network interaction, the contents of the packets can’t be read without using additional tools. We haven’t had any problems since we checked HTTP MITM Proxy.
Analysts can use HTTPS MITM proxy to get deeper data when malware uses SSL or TLS protocols to send or receive information. It helps log and save the SSL/TLS master keys so that analysts can decrypt traffic connections with programs like Wireshark.
2. Tor and locale
Sometimes malicious objects contain macros that check Microsoft Office’s LanguageID and the first letter of its title. And they don’t work if the required settings are wrong.
Sometimes we can guess which country we need to choose for detecting malicious activity by looking at the malicious document decoy language in its description.
We may choose different countries in the Tor field in the expanded settings. It will fool malware that sends requests to the IP services that return the country of IP origin. Malware will quit execution if the country is not targeted. And with Tor, all we need is to determine what threat we’re dealing with in less than three minutes.
Combine Tor and locale to get better and faster results: some malware use quite simple checks related to geolocation. We can select different locales to bypass malware geo evasion during malware analysis. It includes changing:
- Keyboard layout
- Country & currency
- Time zone & format
Some malware will stop executing if there is a particular language in the system. For example, let’s start a task with a Raccoon stealer, selecting the locale Belarusian (be-BY). It’s easy to notice that all processes were terminated right after the start of the malware.
Now let’s restart the task and change the locale to the United States (en-US).
The increased activity is immediately noticeable: the detected malware, Raccoon, started exchanging information over the network, changing system certificate settings, etc.
As you can see, just changing the locale made a striking difference – in one case, the malware simply doesn’t work, while in the other, it shows its malicious properties.
3. VPN
You could also use your own VPN configurations for analysis. Check your Profile page on the service and upload the OpenVPN config file. Besides that, add your file while creating a new task in the network section and go straight to the analysis.
Excel process uses the DDE function to initiate a dynamic data exchange in a sample without a VPN. The process tries downloading the payload from the remote server and launches two regsvr32 processes. One has to run the 4137 file from the C:\Users\admin\AppData\Local\Temp\ catalog. But the payload wasn’t downloaded from the inmanagment.com source. That is why regsvr32 hasn’t launched it.
Suppose we rerun this task and change the simulation’s configurations. By checking the file’s characteristics in Static discovering, we find that there are Italian words. It means that the whole campaign is geotargeted.
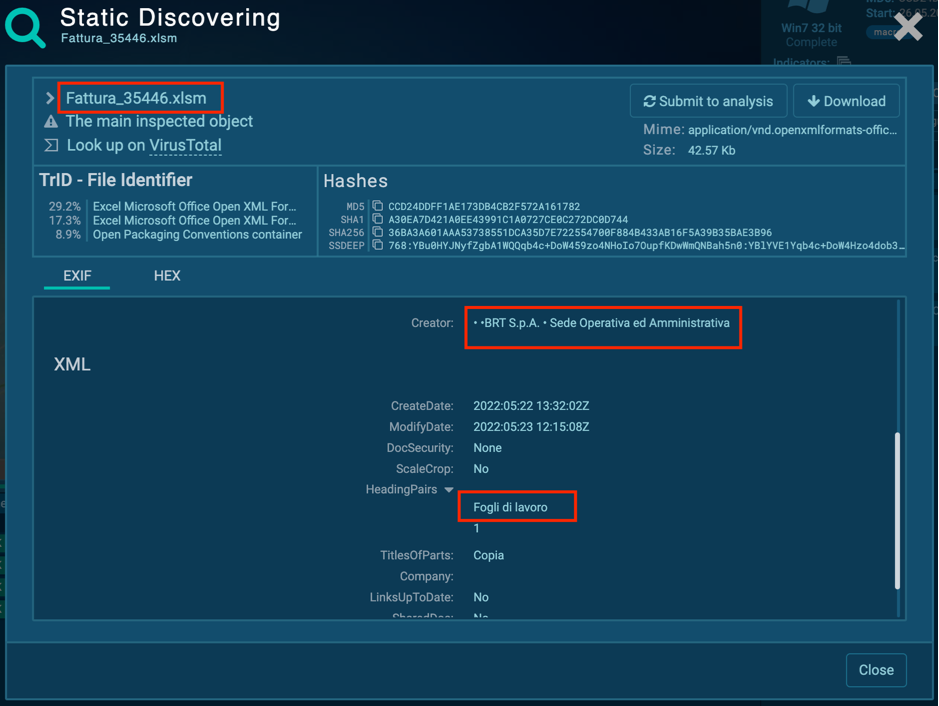
Use ANY. RUN’s Italian VPN for redirection and change OS locale to it-IT like in a sample with VPN.
After 20 sec, the Excel process successfully launches the executable file. The T1497.003 Sandbox Evasion: Time Based Evasion technique establishes the payload. The payload stays inactive.
Ursnif, aka Gozi/ISFB, acquires the same method. Moreover, the malware uses the T1497.002 Sandbox Evasion: User Activity-Based Checks – it tests if there is any activity in the network. After some API for network activity is used, the malware starts execution. It performs numerous operations: injects malicious code into OS’s applications, deletes itself, exchanges data with the remote server, etc.
To sum it up
Investigating malicious programs on systems outside the targeted region will not reveal their entire behavior, especially when the malware has built-in location checks. We discussed 3 ways to analyze a location-based malware that demonstrates different behavior in a specific country:
- HTTPS MITM proxy
- Tor and locale
- VPN
ANY.RUN‘s various features allow cybersecurity specialists to route traffic through their country of choice and uncover all data of geo-targeted malware.
4 comments










Looks great thank you!
Thanks?
A fat lot of good!
Hope it’s useful for your analysis?